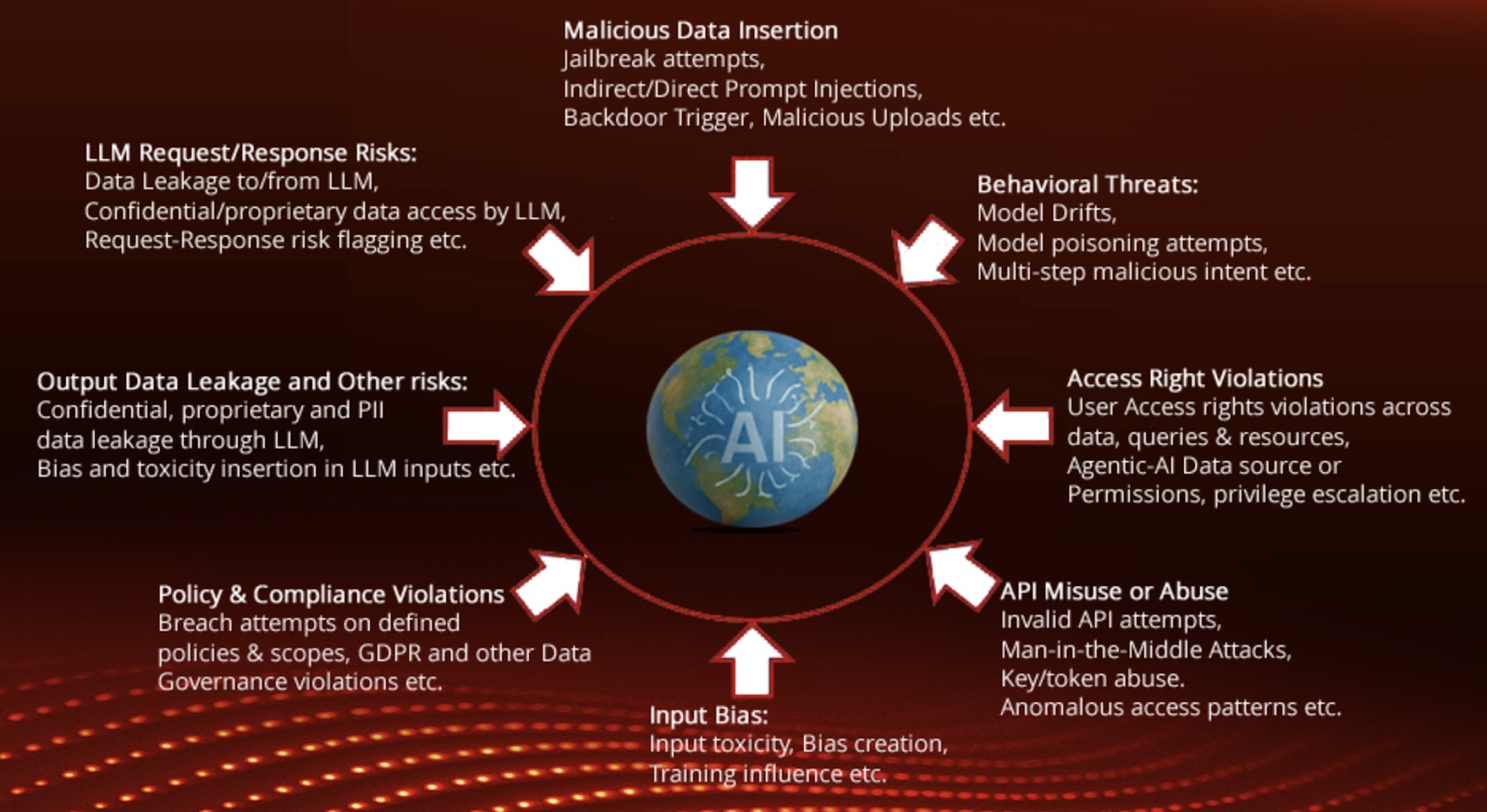
Fixed visibility and safety of information with the suitable stage of safety to take care of protected operational use.
Tel Aviv, Israel-based Ray Safety emerged from stealth with $11 million seed funding and a need to alter the best way company information is protected. The funding was co-led by Enterprise Guides and Ibex Buyers.
The premise of the Ray Safety platform is to know how company information is used, and to use the proper stage of safety on the right time, in actual time. “The platform aligns safety with actual utilization: energetic information stays obtainable with the suitable controls, and dormant information will get stricter safeguards,” says Ariel Zamir (CEO and co-founder at Ray Safety).
This functionality is offered by an AI engine that originally learns and understands the company information, after which constantly screens (and predicts) information utilization. It acknowledges information in use, is aware of whether or not it’s regular and acceptable use (primarily based on understanding how the enterprise usually operates), and may predict the subsequent steps for that standard utilization. It then dynamically applies the proper stage of safety that retains information in use protected whereas not impeding operations.
Any uncommon habits triggers dynamic controls – like revoking entry, implementing MFA, or blocking classes – to cease threats as they emerge. “It detects uncommon entry to delicate information, sudden mass downloads, privilege adjustments, or AI instruments pulling information they shouldn’t. It additionally detects ransomware or an insider menace. It will possibly revoke entry, require further authentication, block the session, or alert safety groups, eradicating dangerous sharing hyperlinks, or quarantining information. The bottom line is it acts instantly, not hours later,” explains Zamir.
Regardless of the provide of automated and actual time mitigations, the enterprise doesn’t cede management to the AI. “We don’t exchange human judgment, we pace up response time,” continues Zamir. The enterprise decides which actions the AI can take robotically, which want approval, and which run in ‘observe solely’ mode first.
“Clients have a tendency to use completely different automation ranges to completely different threats: when the menace appears to be associated to a low-to-medium quantity of information, clients favor to have a human concerned within the loop. Nonetheless, when the system identifies a considerable amount of information being accessed quickly, downloaded and even corrupted, some clients favor to reply robotically to forestall any threat of large harm.”
Sudden encryption exercise (ransomware?) might be blocked immediately and robotically; sudden massive scale information being despatched out of the system (double extortion?) might be stopped. However all actions taken by the platform are logged, reversible and might be paused at any time.Commercial. Scroll to proceed studying.
The platform additionally has a useful impact on alert fatigue by fixing most of the ‘alert’ points earlier than they attain the safety staff. We stop 90% of the alerts earlier than they’re born,” says Zamir. “We additionally group associated alerts into one incident and suppress duplicates, so groups solely see high-value occasions with clear context. We additionally cut back the alerts by understanding ‘what’s regular.’ Most alerts occur as a result of safety instruments don’t know the finance staff all the time downloads studies earlier than board conferences, or that builders entry sure databases throughout deployments. When you understand what regular appears like, you solely alert on genuinely uncommon exercise.”
The underlying function and performance of the Ray Safety platform is to mix visibility, understanding and response right into a single actual time automated mitigation, reasonably than the present reliance on scanning, anomaly detection, alerting the safety staff and ready for triage and mitigation hours (when you’re fortunate) later.
Ray Safety, primarily based in Tel Aviv, was based by Ariel Zamir (CEO), Eric Wolf (CBO), and Dekel Levkovich (CTO) in September 2024. The seed funding shall be used for product growth and go-to-market growth. It intends to extend its footprint in mid-size to massive enterprises by concentrating on high-risk, data-intensive industries resembling finance, healthcare and tech.
Associated: AI Emerges because the Hope—and Threat—for Overloaded SOCs
Associated: Ransomware Losses Climb as AI Pushes Phishing to New Heights
Associated: Ox Safety Luggage $60M Collection B to Deal with Appsec Alert Fatigue
Associated: Google Targets SOC Overload With Automated AI Alert and Malware Evaluation Instruments