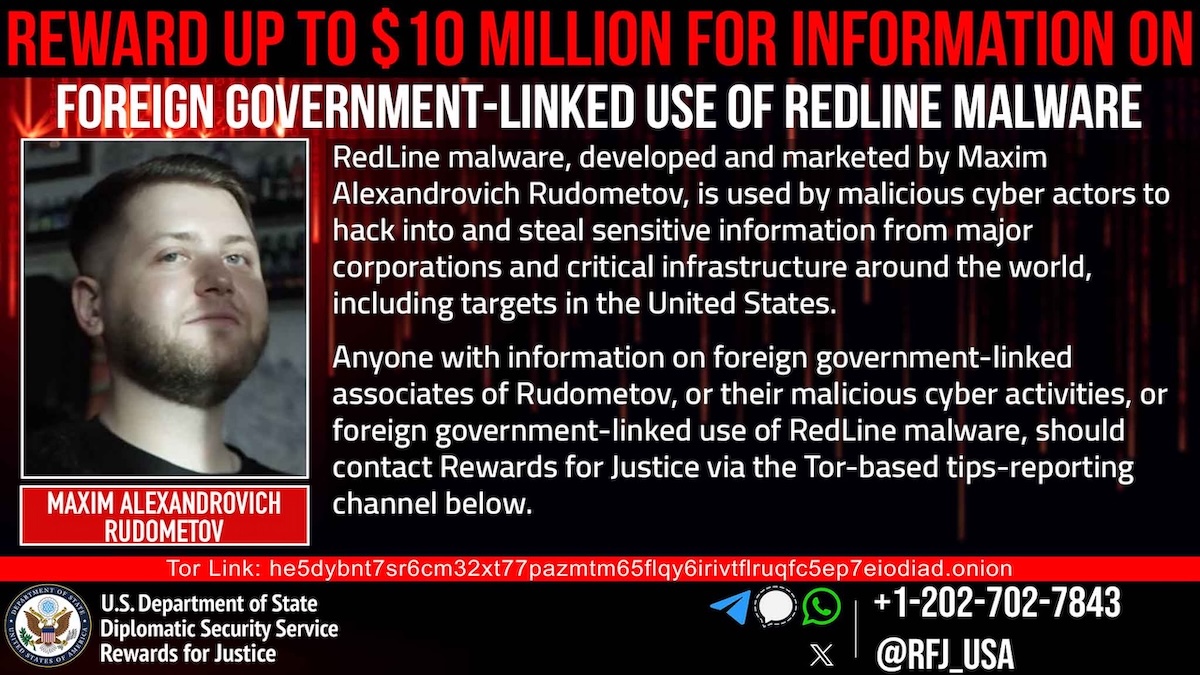
The US Division of State, by its Rewards for Justice program, is providing a reward of as much as $10 million for data on Maxim Alexandrovich Rudometov, a person accused of being a developer and administrator of the RedLine information-stealer malware.
RedLine is a chunk of malware that permits cybercriminals to steal priceless data from compromised methods, together with credentials, cryptocurrency wallets, and different monetary data.
In late October 2024, legislation enforcement companies in six nations introduced disrupting the infrastructure related to RedLine, in addition to the infostealer named Meta. As a part of the operation, authorities shut down servers, seized domains, and arrested two individuals.
On the time of its disruption, RedLine had been used — below a malware-as-a-service mannequin — by greater than 20 Russian-speaking cybercrime teams, which leveraged it to steal the knowledge of hundreds of thousands of customers worldwide, in addition to in intrusions involving essential infrastructure and main organizations.
When RedLine infrastructure was disrupted, the US introduced expenses in opposition to Rudometov, accusing him of growing the malware and serving to handle its infrastructure.
The US has now introduced a reward of as much as $10 million for data that may result in the arrest of Rudometov, recognized on-line as dendimirror, alinchok, ghackihg, makc1901, navi_ghacking, and bloodzz.fenix.
In response to authorities, Rudometov was born in Ukraine and fled to Russia at the beginning of the 2022 invasion of Ukraine.
There don’t look like any current studies describing assaults involving the RedLine malware, however the wording within the Rewards for Justice announcement means that the infostealer should be lively.Commercial. Scroll to proceed studying.
“Anybody with data on overseas authorities linked associates of Rudometov, or their malicious cyber actions, or overseas government-linked use of RedLine malware, ought to contact Rewards for Justice through the Tor-based tips-reporting channel,” reads the announcement.
Suggestions will be submitted by a number of channels, together with Telegram, Sign, WhatsApp, and a Tor-based web site.
Associated: US Providing $2.5 Million Reward for Belarusian Malware Distributor
Associated: US Providing $10 Million Reward for Iranian ICS Hackers
Associated: US Provides $10 Million Reward for Info on North Korean Hacker