ClickFix, FileFix, pretend CAPTCHA — no matter you name it, assaults the place customers work together with malicious scripts of their internet browser are a fast-growing supply of safety breaches.
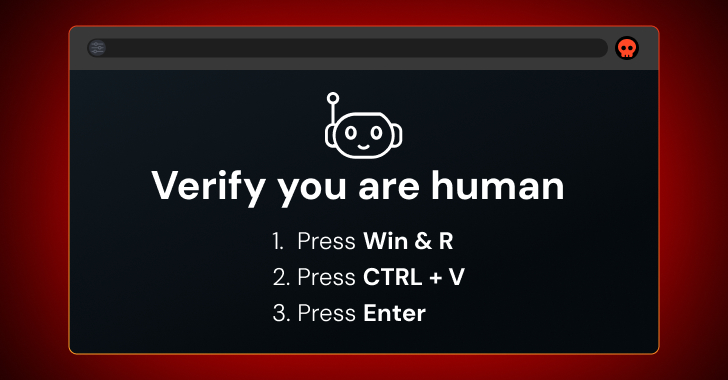
ClickFix assaults immediate the person to unravel some form of drawback or problem within the browser — mostly a CAPTCHA, but additionally issues like fixing an error on a webpage.
The title is a little bit deceptive, although — the important thing issue within the assault is that they trick customers into operating malicious instructions on their machine by copying malicious code from the web page clipboard and operating it regionally.
Examples of ClickFix lures utilized by attackers within the wild.
ClickFix is thought to be repeatedly utilized by the Interlock ransomware group and different prolific menace actors, together with state-sponsored APTs. Numerous latest public information breaches have been linked to ClickFix-style TTPs, reminiscent of Kettering Well being, DaVita, Metropolis of St. Paul, Minnesota, and the Texas Tech College Well being Sciences Facilities (with many extra breaches more likely to contain ClickFix the place the assault vector wasn’t identified or disclosed).
However why are these assaults proving to be so efficient?
Cause 1: Customers aren’t prepared for ClickFix
For the previous decade or extra, person consciousness has targeted on stopping customers from clicking hyperlinks in suspicious emails, downloading dangerous recordsdata, and coming into their username and password into random web sites. It hasn’t targeted on opening up a program and operating a command.
Suspicion is additional decreased when you think about that the malicious clipboard copy motion is carried out behind the scenes by way of JavaScript 99% of the time.
Instance of unobfuscated JavaScript code performing the copy perform mechanically on a ClickFix web page with out person enter.
And with fashionable ClickFix websites and lures turning into more and more legitimate-looking (see the instance beneath), it isn’t stunning that customers are falling sufferer.
One of many extra legit-looking ClickFix lures — this one even has an embedded video displaying the person what to do!
When you think about the truth that these assaults are shifting away from electronic mail altogether, it does not match the mannequin of what customers are educated to be suspicious of.
The highest supply vector recognized by Push Safety researchers was discovered to be search engine optimisation poisoning & malvertising by way of Google Search. By creating new domains or taking on professional ones, attackers are creating watering gap situations to intercept customers shopping the web.
And even for those who have been suspicious, there is not any handy “report phishing” button or workflow to inform your safety crew for Google Search outcomes, social media messages, web site adverts, and so forth.
Cause 2: ClickFix is not being detected throughout supply
There are a number of elements of why ClickFix assaults are going undetected by technical controls.
ClickFix pages, like different fashionable phishing websites, are utilizing a variety of detection evasion methods that forestall them from being flagged by safety instruments — from electronic mail scanners, to web-crawling safety instruments, to internet proxies analyzing community visitors. Detection evasion primarily entails camouflaging and rotating domains to remain forward of known-bad detections (i.e., blocklists), utilizing bot safety to stop evaluation, and closely obfuscating web page content material to cease detection signatures from firing.
And through the use of non-email supply vectors, a complete layer of detection alternative is lower out.
Like different fashionable phishing assaults, ClickFix lures are distributed all around the web — not simply electronic mail.
Malvertising provides one other layer of focusing on to the image. For instance, Google Adverts will be focused to searches coming from particular geographic places, tailor-made to particular electronic mail area matches, or particular machine varieties (e.g. desktop, cellular, and many others.). If you recognize the place your goal is situated, you’ll be able to tailor the advert parameters accordingly.
Together with different methods, like conditional loading to return a lure acceptable in your working system (or not triggering in any respect except sure situations are met, e.g. you are visiting from a cellular OS, or from exterior a goal IP vary) attackers have a means of reaching a lot of potential victims whereas avoiding safety controls on the electronic mail layer and stopping undesirable evaluation.
Instance of a ClickFix lure constructed onto a vibe-coded web site.
Lastly, as a result of the code is copied contained in the browser sandbox, typical safety instruments are unable to look at and flag this motion as probably malicious. Because of this the final — and solely — alternative for organizations to cease ClickFix is on the endpoint, after the person has tried to run the malicious code.
Cause 3: EDR is the final and solely line of protection — and it isn’t foolproof
There are a number of levels to the assault that may and needs to be intercepted by EDR, however the stage of detection raised, and whether or not an motion is blocked in actual time, is pushed by context.
As a result of there is not any file obtain from the net, and the act of operating code on the machine is initiated by the person, there is not any context tying the motion to a different software to make it seem suspicious. For instance, malicious PowerShell executed from Outlook or Chrome would seem clearly suspicious, however as a result of it is user-initiated, it is remoted from the context of the place the code was delivered.
The malicious instructions themselves may be obfuscated or damaged into levels to keep away from straightforward detection by heuristic guidelines. EDR telemetry may document {that a} PowerShell course of ran, however with no identified dangerous signature or a transparent coverage violation, it could not flag it instantly.
The ultimate stage at which the assault needs to be intercepted by any respected EDR is on the level of malware execution. However detection evasion is a cat-and-mouse sport, and attackers are all the time searching for methods to tweak their malware to evade or disable detection instruments. So, exceptions do occur.
And for those who’re a company that enables staff and contractors to make use of unmanaged BYOD gadgets, there is a robust probability that there are gaps in your EDR protection.
Finally, organizations are leaving themselves counting on a single line of protection — if the assault is not detected and blocked by EDR, it is not noticed in any respect.
Why the usual suggestions are falling quick
Many of the vendor-agnostic suggestions have targeted on limiting entry to providers just like the Home windows Run dialog field for typical customers. However though mshta and PowerShell stay essentially the most generally noticed, safety researchers have already noticed a variety of LOLBINS focusing on completely different providers, a lot of that are troublesome to stop customers from accessing.
It is also value contemplating how ClickFix-style assaults could proceed to evolve sooner or later. The present assault path straddles browser and endpoint — what if it may happen fully within the browser and evade EDR altogether? For instance, by pasting malicious JavaScript immediately into the devtools on a related webpage.
The present hybrid assault path sees the attacker ship lures within the browser, to compromise the endpoint, to get entry to creds and cookies saved within the browser. What for those who may skip the endpoint altogether?
Stopping ClickFix on the entrance line — within the browser
Push Safety’s newest function, malicious copy and paste detection, tackles ClickFix-style assaults on the earliest alternative by means of browser-based detection and blocking. It is a universally efficient management that works whatever the lure supply channel, web page model and construction, or the specifics of the malware sort and execution.
Not like heavy-handed DLP options that block copy-paste altogether, Push protects your staff with out disrupting their person expertise or hampering productiveness.
Try the video beneath for extra data.
Be taught extra
If you wish to be taught extra about ClickFix assaults and the way they’re evolving, try this upcoming webinar the place Push Safety researchers shall be diving into real-world ClickFix examples and demonstrating how ClickFix websites work below the hood.
Push Safety’s browser-based safety platform supplies complete assault detection and response capabilities in opposition to methods like AiTM phishing, credential stuffing, ClickFixing, malicious browser extensions, and session hijacking utilizing stolen session tokens. It’s also possible to use Push to search out and repair vulnerabilities throughout the apps that your staff use, like ghost logins, SSO protection gaps, MFA gaps, susceptible passwords, dangerous OAuth integrations, and extra, to harden your id assault floor.
To be taught extra about Push, try our newest product overview or guide a while with one in every of our crew for a dwell demo.
Discovered this text fascinating? This text is a contributed piece from one in every of our valued companions. Comply with us on Google Information, Twitter and LinkedIn to learn extra unique content material we put up.