Oct 24, 2025Ravie LakshmananMalware / Hacking Information
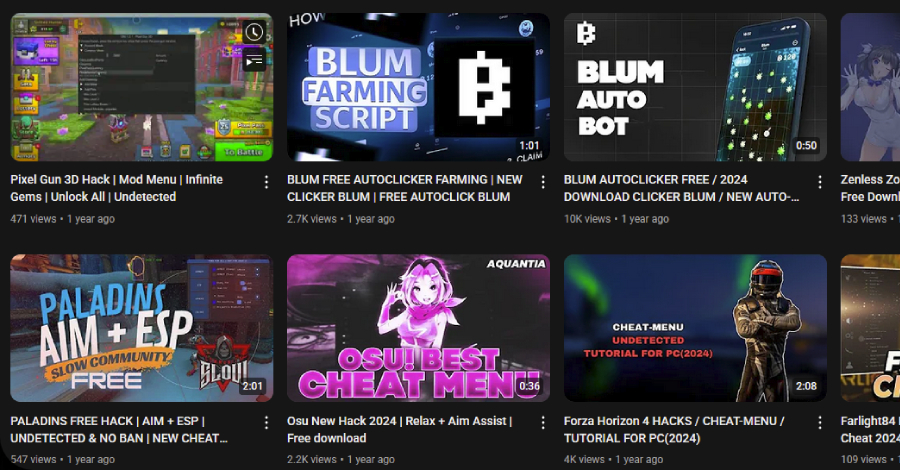
A malicious community of YouTube accounts has been noticed publishing and selling movies that result in malware downloads, primarily abusing the recognition and belief related to the video internet hosting platform for propagating malicious payloads.
Energetic since 2021, the community has printed greater than 3,000 malicious movies so far, with the quantity of such movies tripling because the begin of the yr. It has been codenamed the YouTube Ghost Community by Test Level. Google has since stepped in to take away a majority of those movies.
The marketing campaign leverages hacked accounts and replaces their content material with “malicious” movies which might be centred round pirated software program and Roblox recreation cheats to contaminate unsuspecting customers trying to find them with stealer malware. A few of these movies have racked up lots of of hundreds of views, starting from 147,000 to 293,000.
“This operation took benefit of belief indicators, together with views, likes, and feedback, to make malicious content material appear protected,” Eli Smadja, safety analysis group supervisor at Test Level, stated. “What appears to be like like a useful tutorial can really be a elegant cyber lure. The size, modularity, and class of this community make it a blueprint for the way risk actors now weaponize engagement instruments to unfold malware.”
Using YouTube for malware distribution is just not a brand new phenomenon. For years, risk actors have been noticed hijacking legit channels or utilizing newly created accounts to publish tutorial-style movies with descriptions pointing to malicious hyperlinks that, when clicked, result in malware.
These assaults are a part of a broader development the place attackers repurpose legit platforms for nefarious functions, turning them into an efficient avenue for malware distribution. Whereas a few of the campaigns have abused legit advert networks, corresponding to these related to search engines like google and yahoo like Google or Bing, others have capitalized on GitHub as a supply car, as within the case of the Stargazers Ghost Community.
One of many foremost the explanation why Ghost Networks has taken off in a giant method is that they can’t solely be used to amplify the perceived legitimacy of the hyperlinks shared, but additionally keep operational continuity even when the accounts are banned or taken down by the platform homeowners, because of their role-based construction.
“These accounts make the most of numerous platform options, corresponding to movies, descriptions, posts (a lesser-known YouTube characteristic much like Fb put up), and feedback to advertise malicious content material and distribute malware, whereas making a false sense of belief,” safety researcher Antonis Terefos stated.
“The vast majority of the community consists of compromised YouTube accounts, which, as soon as added, are assigned particular operational roles. This role-based construction allows stealthier distribution, as banned accounts may be quickly changed with out disrupting the general operation.”
There are particular forms of accounts –
Video-accounts, which add phishing movies and supply descriptions containing hyperlinks to obtain the marketed software program (alternatively, the hyperlinks are shared as a pinned remark or supplied instantly within the video as a part of the set up course of)
Submit-accounts, that are accountable for publishing group messages and posts containing hyperlinks to exterior websites
Work together-accounts, which like and put up encouraging feedback to provide the movies a veneer of belief and credibility
The hyperlinks direct customers to a variety of providers like MediaFire, Dropbox, or Google Drive, or phishing pages hosted on Google Websites, Blogger, and Telegraph that, in flip, incorporate hyperlinks to obtain the supposed software program. In lots of of those instances, the hyperlinks are hid utilizing URL shorteners to masks the true vacation spot.
Among the malware households distributed by way of the YouTube Ghost Community embrace Lumma Stealer, Rhadamanthys Stealer, StealC Stealer, RedLine Stealer, Phemedrone Stealer, and different Node.js-based loaders and downloaders –
A channel named @Sound_Writer (9,690 subscribers), which has been compromised for over a yr to add cryptocurrency software program movies to deploy Rhadamanthys
A channel named @Afonesio1 (129,000 subscribers), which was compromised on December 3, 2024, and January 5, 2025, to add a video promoting a cracked model of Adobe Photoshop to distribute an MSI installer that deploys Hijack Loader, which then delivers Rhadamanthys
“The continuing evolution of malware distribution strategies demonstrates the outstanding adaptability and resourcefulness of risk actors in bypassing standard safety defenses,” Test Level stated. “Adversaries are more and more shifting towards extra refined, platform-based methods, most notably, the deployment of Ghost Networks.”
“These networks leverage the belief inherent in legit accounts and the engagement mechanisms of fashionable platforms to orchestrate large-scale, persistent, and extremely efficient malware campaigns.”