Aug 07, 2025Ravie LakshmananVulnerability / Risk Intelligence
Cybersecurity researchers have disclosed a number of safety flaws in video surveillance merchandise from Axis Communications that, if efficiently exploited, might expose them to takeover assaults.
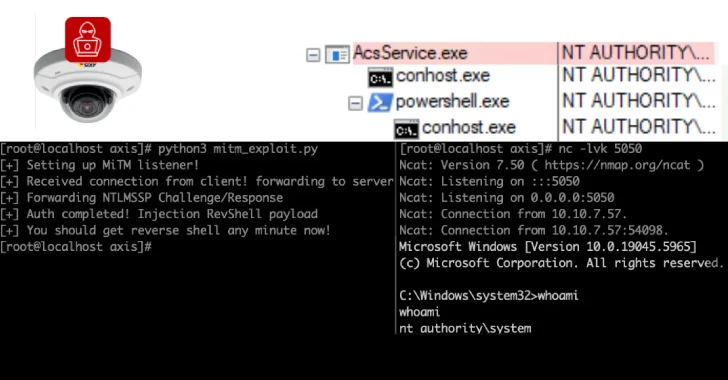
“The assault ends in pre-authentication distant code execution on Axis Gadget Supervisor, a server used to configure and handle fleets of cameras, and the Axis Digital camera Station, shopper software program used to view digital camera feeds,” Claroty researcher Noam Moshe stated.
“Moreover, utilizing web scans of uncovered Axis.Remoting providers, an attacker can enumerate weak servers and shoppers, and perform granular, extremely focused assaults.”
The listing of recognized flaws is beneath –
CVE-2025-30023 (CVSS rating: 9.0) – A flaw within the communication protocol used between shopper and server that would result in an authenticated person performing a distant code execution assault (Mounted in Digital camera Station Professional 6.9, Digital camera Station 5.58, and Gadget Supervisor 5.32)
CVE-2025-30024 (CVSS rating: 6.8) – A flaw within the communication protocol used between shopper and server that may very well be leveraged to execute an adversary-in-the-middle (AitM) assault (Mounted in Gadget Supervisor 5.32)
CVE-2025-30025 (CVSS rating: 4.8) – A flaw within the communication protocol used between the server course of and the service management that would result in an area privilege escalation (Mounted in Digital camera Station Professional 6.8 and Gadget Supervisor 5.32)
CVE-2025-30026 (CVSS rating: 5.3) – A flaw within the Axis Digital camera Station Server that would result in an authentication bypass (Mounted in Digital camera Station Professional 6.9 and Digital camera Station 5.58)
Profitable exploitation of the aforementioned vulnerabilities might permit an attacker to imagine an AitM place between the Digital camera Station and its shoppers, successfully making it attainable to change requests/responses and execute arbitrary actions on both the server or shopper techniques. There isn’t a proof that the problems have been exploited within the wild.
Claroty stated it discovered greater than 6,500 servers that expose the proprietary Axis.Remoting protocol and its providers over the web, out of which practically 4,000 of them are situated within the U.S.
“Profitable exploits give attackers system-level entry on the interior community and the power to manage every of the cameras inside a selected deployment,” Moshe famous. “Feeds may be hijacked, watched, and/or shut down. Attackers can exploit these safety points to bypass authentication to the cameras and acquire pre-authentication distant code execution on the gadgets.”