Jun 16, 2025Ravie LakshmananMalware / Ransomware
An rising ransomware pressure has been found incorporating capabilities to encrypt recordsdata in addition to completely erase them, a improvement that has been described as a “uncommon dual-threat.”
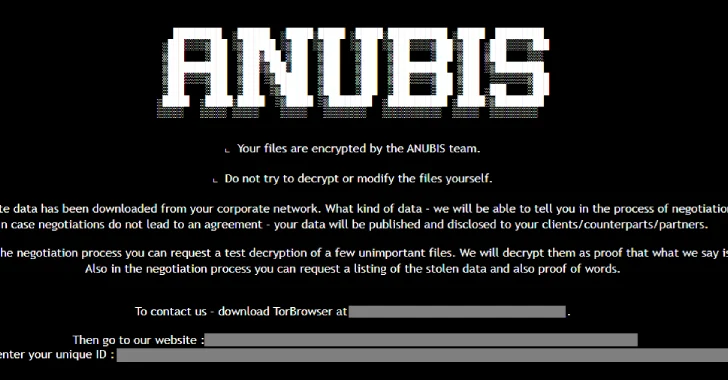
“The ransomware incorporates a ‘wipe mode,’ which completely erases recordsdata, rendering restoration unimaginable even when the ransom is paid,” Development Micro researchers Maristel Policarpio, Sarah Pearl Camiling, and Sophia Nilette Robles mentioned in a report revealed final week.
The ransomware-as-a-service (RaaS) operation in query is known as Anubis, which grew to become energetic in December 2024, claiming victims throughout healthcare, hospitality, and building sectors in Australia, Canada, Peru, and the U.S. Evaluation of early, trial samples of the ransomware means that the builders initially named it Sphinx, earlier than tweaking the model title within the last model.
It is price noting that the e-crime crew has no ties to an Android banking trojan and a Python-based backdoor of the identical title, the latter of which is attributed to the financially-motivated FIN7 (aka GrayAlpha) group.
“Anubis runs a versatile associates program, providing negotiable income splits and supporting further monetization paths like information extortion and entry gross sales,” the cybersecurity firm mentioned.
The associates program follows an 80-20 cut up, permitting affiliate actors to take 80% of the ransom paid. However, information extortion and entry monetization schemes provide a 60-40 and 50-50 cut up, respectively.
Assault chains mounted by Anubis contain the usage of phishing emails because the preliminary entry vector, with the menace actors leveraging the foothold to escalate privileges, conduct reconnaissance, and take steps to delete quantity shadow copies, earlier than encrypting recordsdata and, if needed, wipe their contents.
Because of this the file sizes are lowered to 0 KB whereas leaving the file names or their extensions untouched, making restoration unimaginable and, due to this fact, exerting extra stress on victims to pay up.
“The ransomware features a wiper characteristic utilizing /WIPEMODE parameter, which may completely delete the contents of a file, stopping any restoration try,” the researchers mentioned.
“Its capacity to each encrypt and completely destroy information considerably raises the stakes for victims, amplifying the stress to conform — simply as robust ransomware operations goal to do.”
The invention of Anubis’ damaging habits comes as Recorded Future detailed new infrastructure related to the FIN7 group that is getting used to impersonate authentic software program services as a part of a marketing campaign designed to ship NetSupport RAT.
The Mastercard-owned menace intelligence agency mentioned it recognized three distinctive distribution vectors over the previous yr which have employed bogus browser replace pages, pretend 7-Zip obtain websites, and TAG-124 (aka 404 TDS, Chaya_002, Kongtuke, and LandUpdate808) to ship the malware.
Whereas the pretend browser replace methodology masses a customized loader dubbed MaskBat to execute the distant entry trojan, the remaining two an infection vectors make use of one other customized PowerShell loader dubbed PowerNet that decompresses and executes it.
“[MaskBat] is similar to FakeBat however is obfuscated and comprises strings linked to GrayAlpha,” Recorded Future’s Insikt Group mentioned. “Though all three an infection vectors have been noticed getting used concurrently, solely the pretend 7-Zip obtain pages have been nonetheless energetic on the time of writing, with newly registered domains showing as just lately as April 2025.”
Discovered this text attention-grabbing? Observe us on Twitter and LinkedIn to learn extra unique content material we submit.