Dec 17, 2025Ravie LakshmananEmail Safety / Risk Intelligence
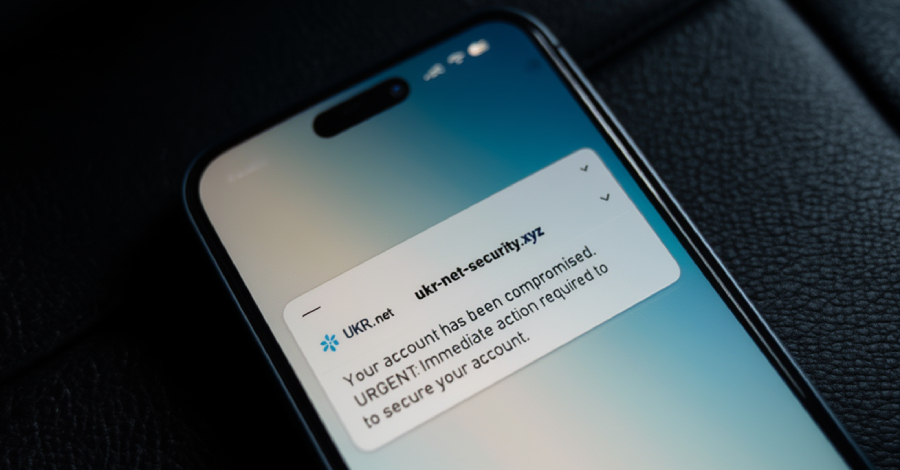
The Russian state-sponsored menace actor referred to as APT28 has been attributed to what has been described as a “sustained” credential-harvesting marketing campaign focusing on customers of UKR[.]web, a webmail and information service widespread in Ukraine.
The exercise, noticed by Recorded Future’s Insikt Group between June 2024 and April 2025, builds upon prior findings from the cybersecurity firm in Could 2024 that detailed the hacking group’s assaults focusing on European networks with the HeadLace malware and credential-harvesting internet pages.
APT28 can be tracked as BlueDelta, Fancy Bear, Forest Blizzard, FROZENLAKE, Iron Twilight, ITG05, Pawn Storm, Sednit, Sofacy, and TA422. It is assessed to be affiliated with Russia’s Principal Directorate of the Normal Workers of the Russian Federation’s Armed Forces (GRU).
The newest assaults are characterised by the deployment of UKR[.]net-themed login pages on reliable companies like Mocky to entice recipients into coming into their credentials and two-factor authentication (2FA) codes. Hyperlinks to those pages are embedded inside PDF paperwork which might be distributed by way of phishing emails.
The hyperlinks are shortened utilizing companies like tiny[.]cc or tinyurl[.]com. In some circumstances, the menace actor has additionally been noticed utilizing subdomains created on platforms like Blogger (*.blogspot[.]com) to launch a two-tier redirection chain that results in the credential harvesting web page.
The efforts are a part of a broader set of phishing and credential theft operations orchestrated by the adversary since mid-2000s focusing on authorities establishments, protection contractors, weapons suppliers, logistics corporations, and coverage assume tanks in pursuit of Russia’s strategic targets.
“Whereas this marketing campaign doesn’t reveal particular targets, BlueDelta’s historic give attention to credential theft to allow intelligence assortment offers robust indicators of probably intent to gather delicate info from Ukrainian customers in help of broader GRU intelligence necessities,” the Mastercard-owned firm mentioned in a report shared with The Hacker Information.
What has modified is the transition from utilizing compromised routers to proxy tunneling companies corresponding to ngrok and Serveo to seize and relay the stolen credentials and 2FA codes.
“BlueDelta’s continued abuse of free internet hosting and anonymized tunneling infrastructure probably displays an adaptive response to Western-led infrastructure takedowns in early 2024,” Recorded Future mentioned. “The marketing campaign highlights the GRU’s persistent curiosity in compromising Ukrainian consumer credentials to help intelligence-gathering operations amid Russia’s ongoing conflict in Ukraine.”