Jul 24, 2025Ravie LakshmananMalware / Cybercrime
Cybersecurity researchers have make clear a brand new versatile malware loader known as CastleLoader that has been put to make use of in campaigns distributing varied info stealers and distant entry trojans (RATs).
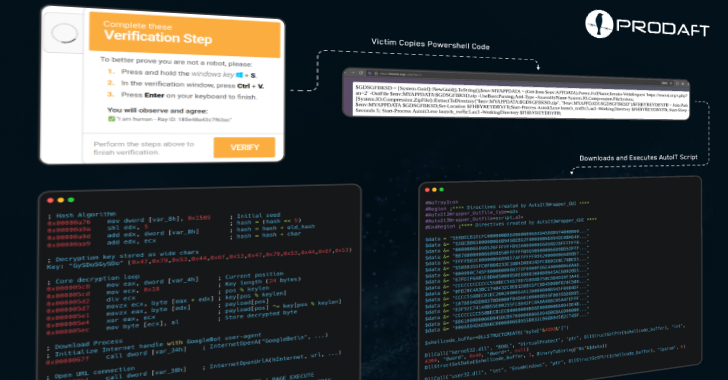
The exercise employs Cloudflare-themed ClickFix phishing assaults and faux GitHub repositories opened below the names of authentic functions, Swiss cybersecurity firm PRODAFT stated in a report shared with The Hacker Information.
The malware loader, first noticed within the wild earlier this 12 months, has been used to distribute DeerStealer, RedLine, StealC, NetSupport RAT, SectopRAT, and even different loaders like Hijack Loader.
“It employs useless code injection and packing methods to hinder evaluation,” the corporate stated. “After unpacking itself at runtime, it connects to a C2 (command-and-control) server, downloads goal modules, and executes them.”CastleLoader’s modular construction permits it to behave as each a supply mechanism and a staging utility, enabling menace actors to separate preliminary an infection from payload deployment. This separation complicates attribution and response as a result of it decouples the an infection vector from the eventual malware conduct, giving attackers extra flexibility in adapting campaigns over time.
CastleLoader payloads are distributed as transportable executables containing an embedded shellcode, which then invokes the primary module of the loader that, in flip, connects to the C2 server with a view to fetch and execute the next-stage malware.
Assaults distributing the malware have relied on the prevalent ClickFix method on domains posing as software program improvement libraries, videoconferencing platforms, browser replace notifications, or doc verification techniques, in the end tricking customers into copying and executing PowerShell instructions that activate the an infection chain.
Victims are directed to the bogus domains by way of Google searches, at which level they’re served pages containing pretend error messages and CAPTCHA verification bins developed by the menace actors, asking them to hold out a collection of directions to supposedly handle the difficulty.
Alternatively, CastleLoader leverages pretend GitHub repositories mimicking authentic instruments as a distribution vector, inflicting customers who unknowingly obtain them to compromise their machines with malware as a substitute.
“This method exploits builders’ belief in GitHub and their tendency to run set up instructions from repositories that seem respected,” PRODAFT stated.This strategic abuse of social engineering mirrors methods utilized in preliminary entry brokers (IABs), underscoring its function inside a broader cybercrime provide chain.
PRODAFT stated it has noticed Hijack Loader being delivered through DeerStealer in addition to CastleLoader, with the latter additionally propagating DeerStealer variants. This means the overlapping nature of those campaigns, regardless of them being orchestrated by completely different menace actors.
Since Could 2025, CastleLoader campaigns have leveraged seven distinct C2 servers, with over 1,634 an infection makes an attempt recorded throughout the time interval. Evaluation of its C2 infrastructure and its web-based panel—which is used to supervise and handle the infections – reveals that as many as 469 gadgets had been compromised, leading to an an infection price of 28.7%.Researchers additionally noticed components of anti-sandboxing and obfuscation—options typical in superior loaders like SmokeLoader or IceID. Mixed with PowerShell abuse, GitHub impersonation, and dynamic unpacking, CastleLoader displays a rising pattern in stealth-first malware loaders that function as stagers in malware-as-a-service (MaaS) ecosystems.
“Fort Loader is a brand new and lively menace, quickly adopted by varied malicious campaigns to deploy an array of different loaders and stealers,” PRODAFT stated. “Its refined anti-analysis methods and multi-stage an infection course of spotlight its effectiveness as a major distribution mechanism within the present menace panorama.”
“The C2 panel demonstrates operational capabilities usually related to malware-as-a-service (MaaS) choices, suggesting the operators have expertise in cybercriminal infrastructure improvement.”