A newly emerged ransomware-as-a-service (RaaS) gang known as Chaos is probably going made up of former members of the BlackSuit crew, because the latter’s darkish net infrastructure has been the topic of a regulation enforcement seizure.
Chaos, which sprang forth in February 2025, is the newest entrant within the ransomware panorama to conduct big-game searching and double extortion assaults.
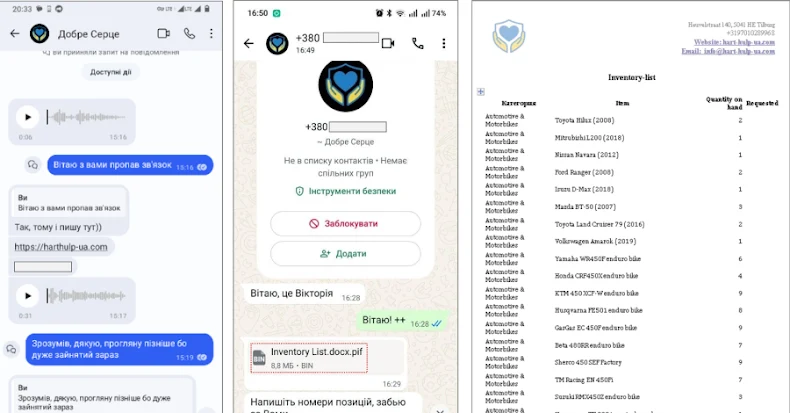
“Chaos RaaS actors initiated low-effort spam flooding, escalating to voice-based social engineering for entry, adopted by RMM software abuse for persistent connection and bonafide file-sharing software program for knowledge exfiltration,” Cisco Talos researchers Anna Bennett, James Nutland, and Chetan Raghuprasad stated.
“The ransomware makes use of multi-threaded speedy selective encryption, anti-analysis methods, and targets each native and community sources, maximizing impression whereas hindering detection and restoration.”
It is vital to notice right here that the ransomware group is unrelated to the Chaos ransomware builder variants equivalent to Yashma and Lucky_Gh0$t, indicating that the menace actors are utilizing the identical title to sow confusion. A majority of the victims are positioned in the US, primarily based on knowledge from Ransomware.dwell.
Appropriate with Home windows, ESXi, Linux and NAS programs, Chaos has been noticed in search of ransoms of $300,000 from victims in trade for a decryptor and a “detailed penetration overview with important kill chain and safety suggestions.”
The assaults contain a mix of phishing and voice phishing methods to acquire preliminary entry by tricking victims into putting in distant desktop software program, notably Microsoft Fast Help.
The menace actors subsequently perform post-compromise discovery and reconnaissance, adopted by putting in different RMM instruments equivalent to AnyDesk, ScreenConnect, OptiTune, Syncro RMM, and Splashtop to ascertain persistent distant entry to the community.
Additionally undertaken are steps to reap credentials, delete PowerShell occasion logs, and delete safety instruments put in on the machine to undermine detection. The assaults culminate with the deployment of the ransomware, however not earlier than lateral motion and knowledge exfiltration utilizing GoodSync.
The ransomware binary helps multithreading to facilitate speedy encryption of each native and community sources, all whereas blocking restoration efforts and implementing multi-layered anti-analysis methods to evade debugging instruments, digital machine environments, automated sandboxes, and different safety platforms.
The hyperlinks to BlackSuit stem from similarities within the tradecraft employed, together with within the encryption instructions, the theme and construction of the ransom be aware, and the RMM instruments used. It is price noting that BlackSuit is a rebrand of the Royal ransomware group, which, in itself, was an offshoot of Conti, highlighting the shape-shifting nature of the menace.
The event comes across the identical time BlackSuit’s darkish web pages have been seized as a part of a joint regulation enforcement effort known as Operation Checkmate. Guests are greeted by a splash display screen that states, “This web site has been seized by U.S. Homeland Safety Investigations as a part of a coordinated worldwide regulation enforcement investigation.” There was no official assertion from authorities on the takedown.
In a associated transfer, the U.S. Federal Bureau of Investigation (FBI) and the Division of Justice (DoJ) publicly introduced the seizure of 20.2891382 BTC (now valued at over $2.4 million) from a cryptocurrency pockets tackle related to a member of the Chaos ransomware group referred to as Hors.
Chaos is the newest entrant to the ransomware panorama, which has additionally witnessed the arrival of different new strains like Backups, Bert, BlackFL, BQTLOCK, Gunra, Jackalock, Moscovium, RedFox, and Sinobi. Assessed to be primarily based on the notorious Conti ransomware, Gunra has claimed 13 victims since late April 2025.
“Gunra ransomware employs superior evasion and anti-analysis methods used to contaminate Home windows Working programs whereas minimizing the danger of detection,” CYFIRMA stated. “Its evasion capabilities embody obfuscation of malicious exercise, avoidance of rule-based detection programs, robust encryption strategies, ransom calls for, and warnings to publish knowledge on underground boards.”
Different current ransomware assaults embody using DLL side-loading to drop NailaoLocker and ClickFix-like lures to trick customers into downloading malicious HTML Utility (HTA) recordsdata beneath the pretext of finishing a CAPTCHA verification examine and spreading Epsilon Crimson ransomware.
“Epsilon Crimson ransomware, first recognized in 2021, leaves a ransom be aware on contaminated computer systems that bears a resemblance to the REvil ransomware be aware, albeit with minor grammatical enhancements,” CloudSEK stated.
In response to NCC Group, ransomware assaults within the second quarter of 2025 dropped 43% to 1,180, a decline from 2,074 in Q1 2025. Qilin has change into probably the most energetic ransomware group in the course of the time interval, main with 151 assaults, adopted by Akira at 131, Play at 115, SafePay at 108, and Lynx at 46. In all, a complete of 86 new and present energetic assault teams are estimated to be energetic in 2025.
“The quantity of victims being uncovered on ransomware leak websites could be declining however this doesn’t suggest threats are decreased,” Matt Hull, International Head of Menace Intelligence at NCC Group, stated.
“Legislation enforcement crackdowns and leaked ransomware supply code is probably a contributing issue as to a drop in exercise, however ransomware teams are utilizing this chance to evolve by way of rebranding and using superior social engineering ways.”