Cybersecurity researchers have disclosed particulars of an ongoing marketing campaign dubbed KongTuke that used a malicious Google Chrome extension masquerading as an advert blocker to intentionally crash the online browser and trick victims into operating arbitrary instructions utilizing ClickFix-like lures to ship a beforehand undocumented distant entry trojan (RAT) dubbed ModeloRAT.
This new escalation of ClickFix has been codenamed CrashFix by Huntress.
KongTuke, additionally tracked as 404 TDS, Chaya_002, LandUpdate808, and TAG-124, is the title given to a visitors distribution system (TDS) recognized for profiling sufferer hosts earlier than redirecting them to a payload supply web site that infects their programs. Entry to those compromised hosts is then handed off to different risk actors, together with ransomware teams, for follow-on malware supply.
Among the cybercriminal teams which have leveraged TAG-124 infrastructure embody Rhysida ransomware, Interlock ransomware, and TA866 (aka Asylum Ambuscade), with the risk actor additionally related to SocGholish and D3F@ck Loader, based on a Recorded Future report from April 2025.
Within the assault chain documented by the cybersecurity firm, the sufferer is alleged to have looked for an advert blocker after they had been served a malicious commercial that redirected them to an extension hosted on the Official Chrome Net Retailer.
The browser extension in query, “NexShield – Superior Net Guardian” (ID: cpcdkmjddocikjdkbbeiaafnpdbdafmi), masquerades because the “final privateness protect” and claims to guard customers in opposition to advertisements, trackers, malware, and intrusive content material on internet pages. It was downloaded at the least 5,000 occasions. It is at present not accessible for obtain.
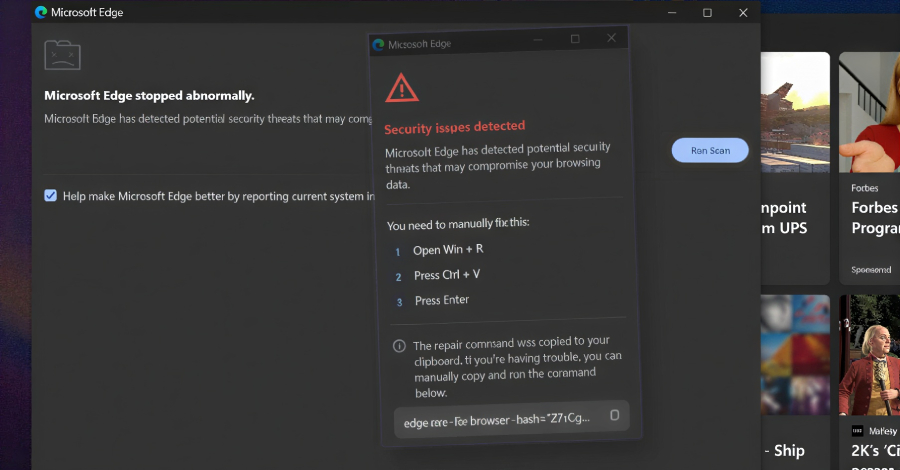
The extension, per Huntress, is a near-identical clone of uBlock Origin Lite model 2025.1116.1841, a official advert blocker add-on accessible for all main internet browsers. It is engineered to show a pretend safety warning, claiming the browser had “stopped abnormally” and prompting customers to run a “scan” to remediate a possible safety risk detected by Microsoft Edge.
Ought to the person choose to run the scan, the sufferer is offered with a bogus safety alert that instructs them to open the Home windows Run dialog and paste the displayed command already copied to the clipboard, and execute it. This, in flip, causes the browser to fully freeze, crashing it by launching a denial-of-service (DoS) assault that creates new runtime port connections by means of an infinite loop that triggers one billion iterations of the identical step repeatedly.
This useful resource exhaustion approach ends in extreme reminiscence consumption, inflicting the online browser to change into gradual, unresponsive, and ultimately crash.
As soon as put in, the extension can also be designed to transmit a singular ID to an attacker-controlled server (“nexsnield[.]com”), giving the operators the power to trace victims. As well as, it adopts a delayed execution mechanism that ensures the malicious habits is barely triggered 60 minutes after it is put in. After that, the payload is executed each 10 minutes.
“The pop-up solely seems on browser startup after the browser turns into unresponsive,” researchers Anna Pham, Tanner Filip, and Dani Lopez mentioned. “Earlier than the DoS executes, a timestamp is saved in native storage. When the person force-quits and restarts their browser, the startup handler checks for this timestamp, and if it exists, the CrashFix popup seems, and the timestamp is eliminated.”
“The DoS solely executes if the UUID exists (which means the person is being tracked), the C2 server responds efficiently to a fetch request, and the pop-up window has been opened at the least as soon as and subsequently closed. This final situation could also be intentional to make sure person interplay with the extension earlier than triggering the payload.”
The tip result’s that it creates a loop of its personal, activating the pretend warning each time the sufferer force-quits and restarts the browser after it turns into unresponsive because of the DoS assault. Within the occasion the extension just isn’t eliminated, the assault is triggered once more after 10 minutes.
The pop-up additionally incorporates numerous anti-analysis methods that disable right-click context menus and stop makes an attempt to make use of keyboard shortcuts to launch developer instruments. The CrashFix command employs the official Home windows utility, finger.exe, to retrieve and execute the next-stage payload from the attacker’s server (“199.217.98[.]108”). KongTuke’s use of the Finger command was documented by safety researcher Brad Duncan in December 2025.
The payload obtained from the server is a PowerShell command that is configured to retrieve a secondary PowerShell script, which, in flip, takes a web page out of SocGholish’s playbook, utilizing a number of layers of Base64 encoding and XOR operations to hide the next-stage malware.
The decrypted blob scans operating processes for over 50 evaluation instruments and digital machine indicators, and instantly ceases execution, if discovered. It additionally checks if the machine is domain-joined or standalone, and sends an HTTP POST request to the identical server containing two items of data –
An inventory of put in antivirus merchandise
A flag with the worth “ABCD111” for standalone “WORKGROUP” machines or “BCDA222” for domain-joined hosts
Within the occasion, the compromised system is marked as domain-joined, the KongTuke assault chain culminates with the deployment of ModeloRAT, a fully-featured Python-based Home windows RAT that makes use of RC4 encryption for command-and-control (C2) communications (“170.168.103[.]208” or “158.247.252[.]178”), units up persistence utilizing Registry, and facilitates the execution of binaries, DLLs, Python scripts, and PowerShell instructions.
ModeloRAT is supplied to replace or terminate itself upon receiving a self-update (“VERSION_UPDATE”) or exit (“TERMINATION_SIGNAL”) command. It additionally implements a assorted beaconing logic to fly beneath the radar.
“Beneath regular operation, it makes use of a typical interval of 300 seconds (5 minutes),” Huntress mentioned. “When the server sends an activation configuration command, the implant enters lively mode with fast polling at a configurable interval, defaulting to 150 milliseconds.”
“After six or extra consecutive communication failures, the RAT backs off to an prolonged interval of 900 seconds (quarter-hour) to keep away from detection. When recovering from a single communication failure, it makes use of a reconnection interval of 150 seconds earlier than resuming regular operations.”
Whereas the concentrating on of domain-joined machines with ModeloRAT means that KongTuke goes after company environments to facilitate deeper entry, customers on standalone workstations are subjected to a separate multi-stage an infection sequence that ends with the C2 server responding with the message “TEST PAYLOAD!!!!,” indicating it might nonetheless be within the testing part.
“KongTuke’s CrashFix marketing campaign demonstrates how risk actors proceed to evolve their social engineering ways,” the cybersecurity firm concluded. “By impersonating a trusted open-source undertaking (uBlock Origin Lite), crashing the person’s browser on objective, after which providing a pretend repair, they’ve constructed a self-sustaining an infection loop that preys on person frustration.”