Jul 18, 2025Ravie LakshmananCloud Safety / AI Safety
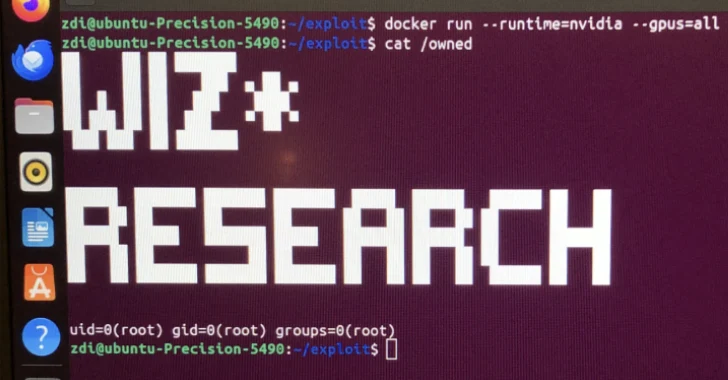
Cybersecurity researchers have disclosed a crucial container escape vulnerability within the NVIDIA Container Toolkit that might pose a extreme risk to managed AI cloud companies.
The vulnerability, tracked as CVE-2025-23266, carries a CVSS rating of 9.0 out of 10.0. It has been codenamed NVIDIAScape by Google-owned cloud safety firm Wiz.
“NVIDIA Container Toolkit for all platforms comprises a vulnerability in some hooks used to initialize the container, the place an attacker may execute arbitrary code with elevated permissions,” NVIDIA mentioned in an advisory for the bug.
“A profitable exploit of this vulnerability would possibly result in escalation of privileges, knowledge tampering, data disclosure, and denial-of-service.”
The shortcoming impacts all variations of NVIDIA Container Toolkit as much as and together with 1.17.7 and NVIDIA GPU Operator as much as and together with 25.3.0. It has been addressed by the GPU maker in variations 1.17.8 and 25.3.1, respectively.
The NVIDIA Container Toolkit refers to a set of libraries and utilities that allow customers to construct and run GPU-accelerated Docker containers. The NVIDIA GPU Operator is designed to deploy these containers mechanically on GPU nodes in a Kubernetes cluster.
Wiz, which shared particulars of the flaw in a Thursday evaluation, mentioned the shortcoming impacts 37% of cloud environments, permitting an attacker to probably entry, steal, or manipulate the delicate knowledge and proprietary fashions of all different clients operating on the identical shared {hardware} via a three-line exploit.
The vulnerability stems from a misconfiguration in how the toolkit handles the Open Container Initiative (OCI) hook “createContainer.” A profitable exploit for CVE-2025-23266 may end up in an entire takeover of the server. Wiz additionally characterised the flaw as “extremely” simple to weaponize.
“By setting LD_PRELOAD of their Dockerfile, an attacker may instruct the nvidia-ctk hook to load a malicious library,” Wiz researchers Nir Ohfeld and Shir Tamari added.
“Making issues worse, the createContainer hook executes with its working listing set to the container’s root filesystem. This implies the malicious library will be loaded instantly from the container picture with a easy path, finishing the exploit chain.”
All of this may be achieved with a “stunningly easy three-line Dockerfile” that masses the attacker’s shared object file right into a privileged course of, leading to a container escape.
The disclosure comes a few months after Wiz detailed a bypass for one more vulnerability in NVIDIA Container Toolkit (CVE-2024-0132, CVSS rating: 9.0 and CVE-2025-23359, CVSS rating: 8.3) that might have been abused to attain full host takeover.
“Whereas the hype round AI safety dangers tends to deal with futuristic, AI-based assaults, ‘old-school’ infrastructure vulnerabilities within the ever-growing AI tech stack stay the rapid risk that safety groups ought to prioritize,” Wiz mentioned.
“Moreover, this analysis highlights, not for the primary time, that containers will not be a robust safety barrier and shouldn’t be relied upon as the only technique of isolation. When designing functions, particularly for multi-tenant environments, one ought to at all times ‘assume a vulnerability’ and implement at the very least one sturdy isolation barrier, resembling virtualization.”