Jan 02, 2026Ravie LakshmananCloud Safety / E mail Safety
Cybersecurity researchers have disclosed particulars of a phishing marketing campaign that entails the attackers impersonating reliable Google-generated messages by abusing Google Cloud’s Software Integration service to distribute emails.
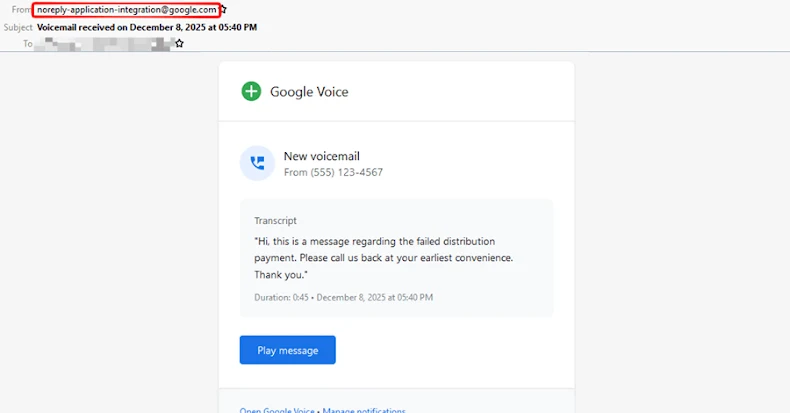
The exercise, Verify Level stated, takes benefit of the belief related to Google Cloud infrastructure to ship the messages from a reliable e-mail tackle (“noreply-application-integration@google[.]com”) in order that they will bypass conventional e-mail safety filters and have a greater probability of touchdown in customers’ inboxes.
“The emails mimic routine enterprise notifications comparable to voicemail alerts and file entry or permission requests, making them seem regular and reliable to recipients,” the cybersecurity firm stated.
Attackers have been noticed sending 9,394 phishing emails focusing on roughly 3,200 prospects over a 14-day interval noticed in December 2025, with the affected organizations positioned within the U.S., Asia-Pacific, Europe, Canada, and Latin America.
On the coronary heart of the marketing campaign is the abuse of Software Integration’s “Ship E mail” job, which permits customers to ship customized e-mail notifications from an integration. Google notes in its assist documentation that solely a most of 30 recipients might be added to the duty.
The truth that these emails might be configured to be despatched to any arbitrary e-mail addresses demonstrates the risk actor’s means to misuse a reliable automation functionality to their benefit and ship emails from Google-owned domains, successfully bypassing DMARC and SPF checks.
“To additional enhance belief, the emails intently adopted Google notification fashion and construction, together with acquainted formatting and language,” Verify Level stated. “The lures generally referenced voicemail messages or claims that the recipient had been granted entry to a shared file or doc, comparable to entry to a ‘This autumn’ file, prompting recipients to click on embedded hyperlinks and take quick motion.”
The assault chain is a multi-stage redirection stream that commences when an e-mail recipient clicks on a hyperlink hosted on storage.cloud.google[.]com, one other trusted Google Cloud service. The hassle is seen as one other effort to decrease person suspicion and provides it a veneer of legitimacy.
The hyperlink then redirects the person to content material served from googleusercontent[.]com, presenting them with a pretend CAPTCHA or image-based verification that acts as a barrier by blocking automated scanners and safety instruments from scrutinizing the assault infrastructure, whereas permitting actual customers to cross by.
As soon as the validation part is full, the person is taken to a pretend Microsoft login web page that is hosted on a non-Microsoft area, finally stealing any credentials entered by the victims.
In response to the findings, Google has blocked the phishing efforts that abuse the e-mail notification function inside Google Cloud Software Integration, including that it is taking extra steps to forestall additional misuse.
Verify Level’s evaluation has revealed that the marketing campaign has primarily focused manufacturing, know-how, monetary, skilled providers, and retail sectors, though different trade verticals, together with media, training, healthcare, vitality, authorities, journey, and transportation, have been singled out.
“These sectors generally depend on automated notifications, shared paperwork, and permission-based workflows, making Google-branded alerts particularly convincing,” it added. “This marketing campaign highlights how attackers can misuse reliable cloud automation and workflow options to distribute phishing at scale with out conventional spoofing.”