Aug 21, 2025Ravie LakshmananMalware / Cryptocurrency
Menace actors have been noticed leveraging the misleading social engineering tactic often called ClickFix to deploy a flexible backdoor codenamed CORNFLAKE.V3.
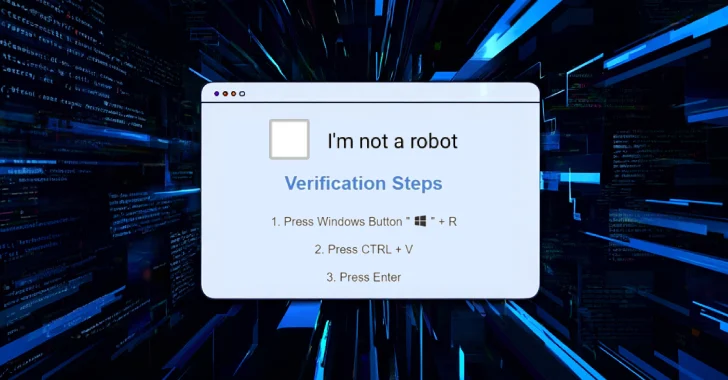
Google-owned Mandiant described the exercise, which it tracks as UNC5518, as a part of an access-as-a-service scheme that employs pretend CAPTCHA pages as lures to trick customers into offering preliminary entry to their techniques, which is then monetized by different menace teams.
“The preliminary an infection vector, dubbed ClickFix, entails luring customers on compromised web sites to repeat a malicious PowerShell script and execute it by way of the Home windows Run dialog field,” Google stated in a report printed at the moment.
The entry supplied by UNC5518 is assessed to be leveraged by at the least two completely different hacking teams, UNC5774 and UNC4108, to provoke a multi-stage an infection course of and drop further payloads –
UNC5774, one other financially motivated group that delivers CORNFLAKE as a technique to deploy varied subsequent payloads
UNC4108, a menace actor with unknown motivation that makes use of PowerShell to deploy instruments like VOLTMARKER and NetSupport RAT
The assault chain possible begins with the sufferer touchdown a pretend CAPTCHA verification web page after interacting with search outcomes that make use of search engine marketing (search engine optimization) poisoning or malicious advertisements.
The consumer is then tricked into operating a malicious PowerShell command by launching the Home windows Run dialog, which then executes the next-stage dropper payload from a distant server. The newly downloaded script checks if it is operating inside a virtualized setting and in the end launches CORNFLAKE.V3.
Noticed in each JavaScript and PHP variations, CORNFLAKE.V3 is a backdoor that helps the execution of payloads by way of HTTP, together with executables, dynamic-link libraries (DLLs), JavaScript recordsdata, batch scripts, and PowerShell instructions. It could possibly additionally acquire primary system info and transmit it to an exterior server. The visitors is proxied via Cloudflare tunnels in an try to keep away from detection.
“CORNFLAKE.V3 is an up to date model of CORNFLAKE.V2, sharing a good portion of its codebase,” Mandiant researcher Marco Galli stated. “In contrast to V2, which functioned solely as a downloader, V3 options host persistence by way of a registry Run key, and helps further payload varieties.”
Each generations are markedly completely different from their progenitor, a C-based downloader that makes use of TCP sockets for command-and-control (C2) communications and solely has the power to run DLL payloads.
Persistence on the host is achieved by way of Home windows Registry modifications. At the least three completely different payloads are delivered by way of CORNFLAKE.V3. This includes an Energetic Listing reconnaissance utility, a script to reap credentials by way of Kerberoasting, and one other backdoor known as WINDYTWIST.SEA, a C model of WINDYTWIST that helps relaying TCP visitors, offering a reverse shell, executing instructions, and eradicating itself.
Choose variations of WINDYTWIST.SEA have additionally been noticed making an attempt to maneuver laterally within the community of the contaminated machine.
“To mitigate malware execution via ClickFix, organizations ought to disable the Home windows Run dialog field the place attainable,” Galli stated. “Common simulation workout routines are essential to counter this and different social engineering ways. Moreover, strong logging and monitoring techniques are important for detecting the execution of subsequent payloads, resembling these related to CORNFLAKE.V3.”
USB An infection Drops XMRig Miner
The disclosure comes because the menace intelligence agency detailed an ongoing marketing campaign that employs USB drives to contaminate different hosts and deploy cryptocurrency miners since September 2024.
“This demonstrates the continued effectiveness of preliminary entry by way of contaminated USB drives,” Mandiant stated. “The low value and skill to bypass community safety make this method a compelling possibility for attackers.”
The assault chain begins when a sufferer is tricked into executing a Home windows shortcut (LNK) within the compromised USB drive. The LNK file ends in the execution of a Visible Primary script additionally situated in the identical folder. The script, for its half, launches a batch script to provoke the an infection –
DIRTYBULK, a C++ DLL launcher to provoke the execution of different malicious elements, resembling CUTFAIL
CUTFAIL, a C++ malware dropper answerable for decrypting and putting in malware onto a system, resembling HIGHREPS and PUMPBENCH, in addition to third-libraries like OpenSSL, libcurl, and WinPthreadGC
HIGHREPS, a downloader that retrieves further recordsdata to make sure persistence of PUMPBENCH
PUMPBENCH, a C++ backdoor that facilitates reconnaissance, gives distant entry by speaking with a PostgreSQL database server, and obtain XMRig
XMRig, an an open-source software program for mining cryptocurrencies resembling Monero, Dero, and Ravencoin
“PUMPBENCH spreads by infecting USB drives,” Mandiant stated. “It scans the system for out there drives after which creates a batch file, a VBScript file, a shortcut file, and a DAT file.”