Jul 31, 2025Ravie LakshmananPhishing / Risk Intelligence
Cybersecurity researchers have disclosed particulars of a brand new phishing marketing campaign that conceals malicious payloads by abusing hyperlink wrapping companies from Proofpoint and Intermedia to bypass defenses.
“Hyperlink wrapping is designed by distributors like Proofpoint to guard customers by routing all clicked URLs by way of a scanning service, permitting them to dam recognized malicious locations in the intervening time of click on,” the Cloudflare Electronic mail Safety group mentioned.
“Whereas that is efficient towards recognized threats, assaults can nonetheless succeed if the wrapped hyperlink hasn’t been flagged by the scanner at click on time.”
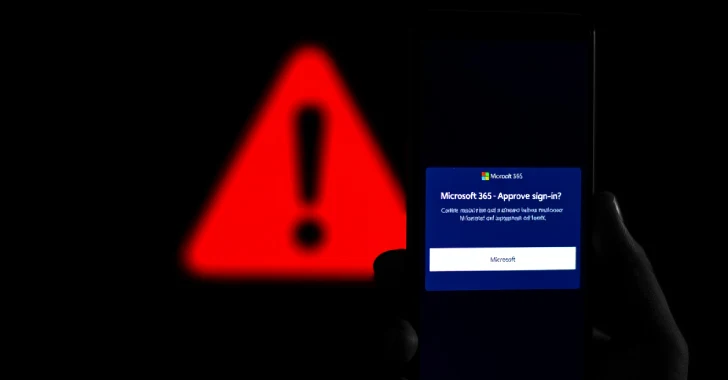
The exercise, noticed during the last two months, as soon as once more illustrates how risk actors discover alternative ways to leverage legit options and trusted instruments to their benefit and carry out malicious actions, on this case, redirecting victims to Microsoft 365 phishing pages.
It is noteworthy that the abuse of hyperlink wrapping includes the attackers gaining unauthorized entry to e-mail accounts that already use the function inside a company, in order that any e-mail message containing a malicious URL despatched from that account is robotically rewritten with the wrapped hyperlink (e.g., urldefense.proofpoint[.]com/v2/url?u=).
One other necessary facet considerations what Cloudflare calls “multi-tiered redirect abuse,” during which the risk actors first cloak their malicious hyperlinks utilizing a URL shortening service like Bitly, after which ship the shortened hyperlink in an e-mail message by way of a Proofpoint-secured account, inflicting it to be obscured a second time.
This habits successfully creates a redirection chain, the place the URL passes by way of two ranges of obfuscation – Bitly and Proofpoint’s URL Protection – earlier than taking the sufferer to the phishing web page.
Within the assaults noticed by the net infrastructure firm, the phishing messages masquerade as voicemail notifications, urging recipients to click on on a hyperlink to hearken to them, finally directing them to a bogus Microsoft 365 phishing web page designed to seize their credentials.
Alternate an infection chains make use of the identical method in emails that notify customers of a supposed doc acquired on Microsoft Groups and trick them into clicking on booby-trapped hyperlinks.
A 3rd variation of those assaults impersonates Groups in emails, claiming that they’ve unread messages and that they’ll click on on the “Reply in Groups” button embedded within the messages to redirect them to credential harvesting pages.
“By cloaking malicious locations with legit urldefense[.]proofpoint[.]com and url[.]emailprotection URLs, these phishing campaigns’ abuse of trusted hyperlink wrapping companies considerably will increase the probability of a profitable assault,” Cloudflare mentioned.
The event comes amid a spike in phishing assaults that weaponize Scalable Vector Graphics (SVG) recordsdata to get round conventional anti-spam and anti-phishing protections and provoke multi-stage malware infections.
“Not like JPEG or PNG recordsdata, SVG recordsdata are written in XML and help JavaScript and HTML code,” the New Jersey Cybersecurity and Communications Integration Cell (NJCCIC) mentioned final month. “They will comprise scripts, hyperlinks, and interactive parts, which will be exploited by embedding malicious code inside innocent SVG recordsdata.”
Phishing campaigns have additionally been noticed embedding faux Zoom videoconferencing hyperlinks in emails that, when clicked, set off a redirection chain to a faux web page that mimics a realistic-looking interface, after which they’re served a “assembly connection timed out” message and brought to a phishing web page that prompts them to enter their credentials to rejoin the assembly.
“Sadly, as an alternative of ‘rejoining,’ the sufferer’s credentials together with their IP handle, nation, and area are exfiltrated by way of Telegram, a messaging app infamous for ‘safe, encrypted communications,’ and inevitably despatched to the risk actor,” Cofense mentioned in a current report.