Oct 15, 2025Ravie LakshmananVulnerability / Risk Intelligence
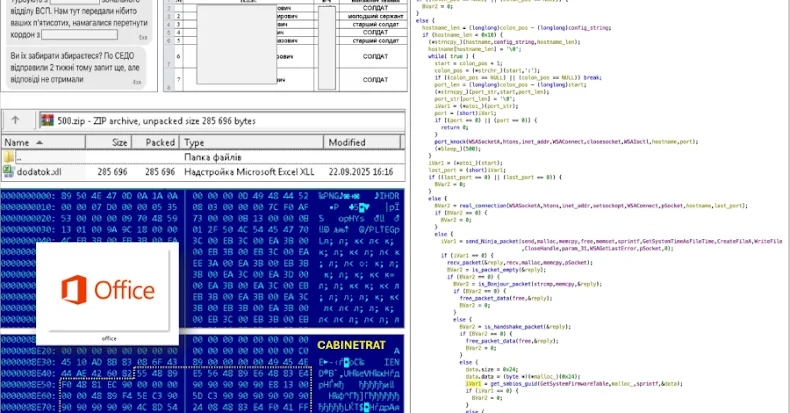
U.S. cybersecurity firm F5 on Wednesday disclosed that unidentified risk actors broke into its techniques and stole recordsdata containing a few of BIG-IP’s supply code and data associated to undisclosed vulnerabilities within the product.
It attributed the exercise to a “extremely subtle nation-state risk actor,” including the adversary maintained long-term, persistent entry to its community. The corporate mentioned it realized of the breach on August 9, 2025, per a Kind 8-Okay submitting with the U.S. Securities and Change Fee (SEC).
“We now have taken intensive actions to include the risk actor,” it famous. “Since starting these actions, we now have not seen any new unauthorized exercise, and we imagine our containment efforts have been profitable.”
F5 didn’t say for a way lengthy the risk actors had entry to its BIG-IP product improvement surroundings, however emphasised that it has not noticed any indication that the vulnerabilities have been exploited in a malicious context. It additionally mentioned that the attackers didn’t entry its CRM, monetary, assist case administration, or iHealth techniques.
That mentioned, the corporate acknowledged that a number of the exfiltrated recordsdata from its information administration platform contained configuration or implementation data for a small share of consumers. Impacted clients are anticipated to be instantly notified following a overview of the recordsdata.
Following the invention of the incident, F5 has engaged the companies of Google Mandiant and CrowdStrike, in addition to rotated credentials and strengthened entry controls, deployed tooling to higher monitor threats, bolstered its product improvement surroundings with additional safety controls, and carried out enhancements to its community safety structure.
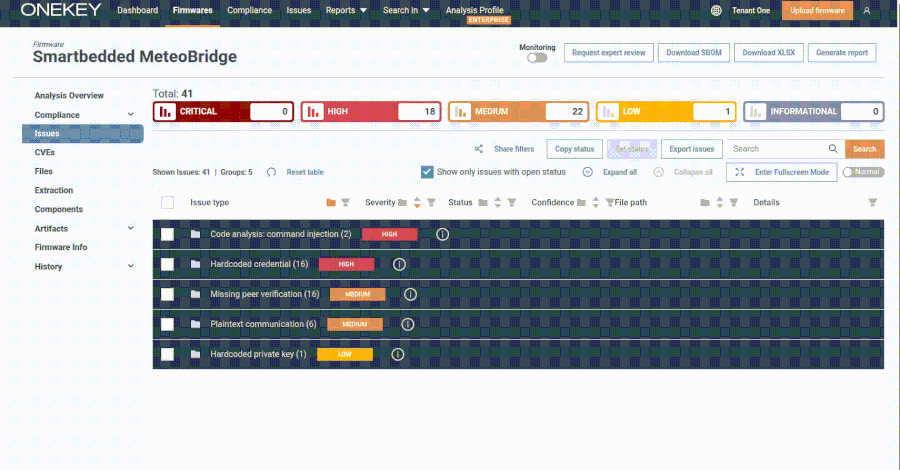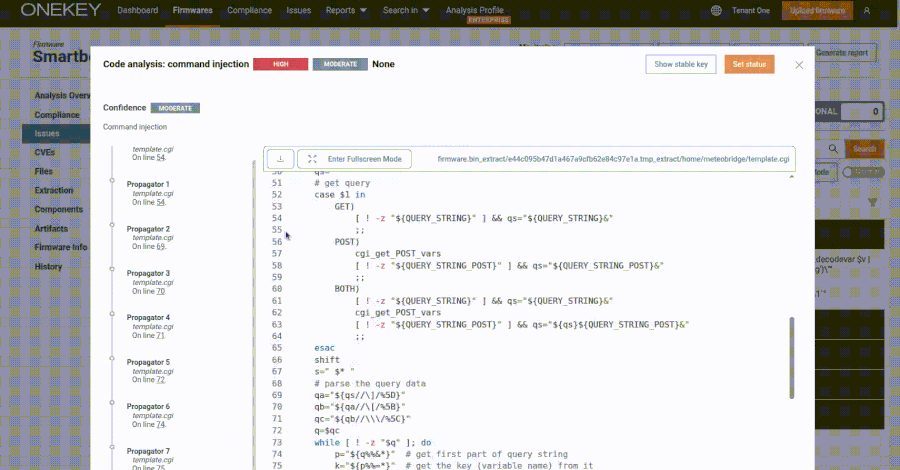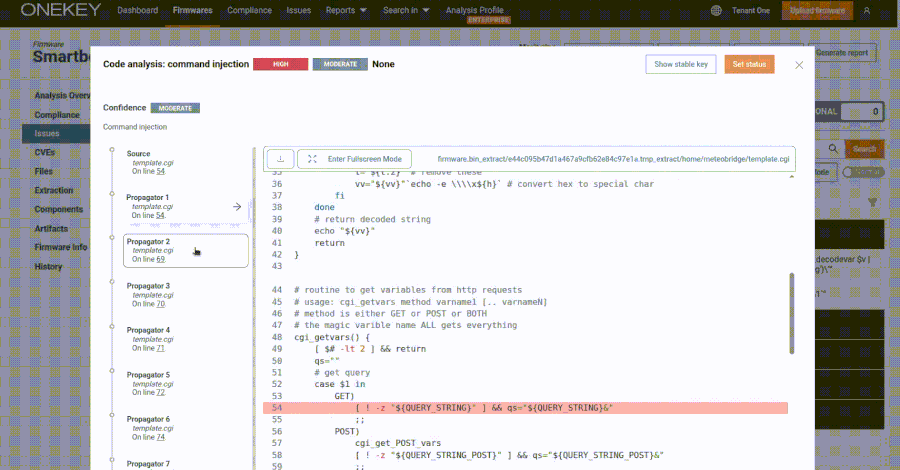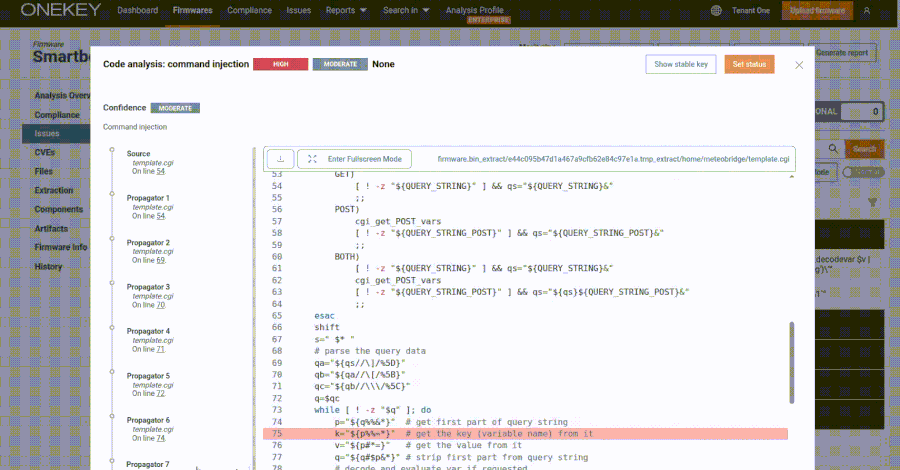
Customers are suggested to use the newest updates for BIG-IP, F5OS, BIG-IP Subsequent for Kubernetes, BIG-IQ, and APM purchasers as quickly as potential for optimum safety.