Might 12, 2025Ravie LakshmananMalware / Synthetic Intelligence
Menace actors have been noticed leveraging faux synthetic intelligence (AI)-powered instruments as a lure to entice customers into downloading an info stealer malware dubbed Noodlophile.
“As an alternative of counting on conventional phishing or cracked software program websites, they construct convincing AI-themed platforms – usually marketed by way of legitimate-looking Fb teams and viral social media campaigns,” Morphisec researcher Shmuel Uzan stated in a report revealed final week.
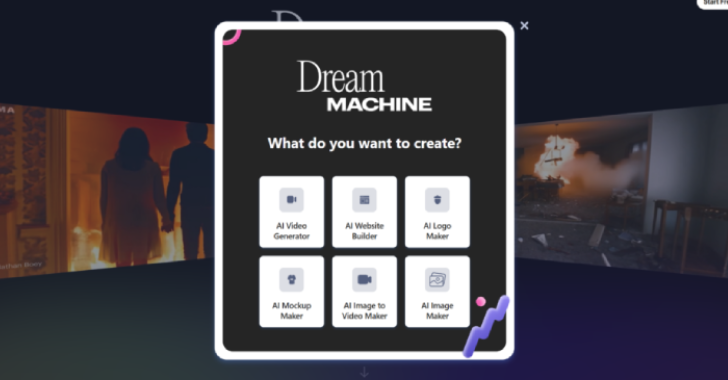
Posts shared on these pages have been discovered to draw over 62,000 views on a single publish, indicating that customers in search of AI instruments for video and picture modifying are the goal of this marketing campaign. A number of the faux social media pages recognized embrace Luma Dreammachine Al, Luma Dreammachine, and gratistuslibros.
Customers who land on the social media posts are urged to click on on hyperlinks that publicize AI-powered content material creation providers, together with movies, logos, photos, and even web sites. One of many bogus web sites masquerades as CapCut AI, providing customers an “all-in-one video editor with new AI options.”
As soon as unsuspecting customers add their picture or video prompts on these websites, they’re then requested to obtain the supposed AI-generated content material, at which level a malicious ZIP archive (“VideoDreamAI.zip”) is downloaded as an alternative.
Current inside the file is a misleading file named “Video Dream MachineAI.mp4.exe” that kick-starts the an infection chain by launching a professional binary related to ByteDance’s video editor (“CapCut.exe”). This C++-based executable is used to run a .NET-based loader named CapCutLoader that, in flip, finally masses a Python payload (“srchost.exe”) from a distant server.
The Python binary paves the best way for the deployment of Noodlophile Stealer, which comes with capabilities to reap browser credentials, cryptocurrency pockets info, and different delicate information. Choose situations have additionally bundled the stealer with a distant entry trojan like XWorm for entrenched entry to the contaminated hosts.
The developer of Noodlophile is assessed to be of Vietnamese origin, who, on their GitHub profile, claims to be a “passionate Malware Developer from Vietnam.” The account was created on March 16, 2025. It is price declaring that the Southeast Asian nation is dwelling to a thriving cybercrime ecosystem that has a historical past of distributing varied stealer malware households concentrating on Fb.
Unhealthy actors weaponizing public curiosity in AI applied sciences to their benefit just isn’t a brand new phenomenon. In 2023, Meta stated it took down greater than 1,000 malicious URLs from being shared throughout its providers that have been discovered to leverage OpenAI’s ChatGPT as a lure to propagate about 10 malware households since March 2023.
The disclosure comes as CYFIRMA detailed one other new .NET-based stealer malware household codenamed PupkinStealer that may steal a variety of information from compromised Home windows methods and exfiltrate it to an attacker-controlled Telegram bot.
“With no particular anti-analysis defenses or persistence mechanisms, PupkinStealer depends upon easy execution and low-profile conduct to keep away from detection throughout its operation,” the cybersecurity firm stated. “PupkinStealer exemplifies a easy but efficient type of data-stealing malware that leverages frequent system behaviors and broadly used platforms to exfiltrate delicate info.”
Discovered this text fascinating? Observe us on Twitter and LinkedIn to learn extra unique content material we publish.