Jun 04, 2025Ravie Lakshmanan Menace Intelligence / Knowledge Breach
Google has disclosed particulars of a financially motivated menace cluster that it mentioned “specialises” in voice phishing (aka vishing) campaigns designed to breach organizations’ Salesforce cases for large-scale knowledge theft and subsequent extortion.
The tech large’s menace intelligence group is monitoring the exercise underneath the moniker UNC6040, which it mentioned displays traits that align with menace teams with ties to a web-based cybercrime collective referred to as The Com.
“Over the previous a number of months, UNC6040 has demonstrated repeated success in breaching networks by having its operators impersonate IT help personnel in convincing telephone-based social engineering engagements,” the corporate mentioned in a report shared with The Hacker Information.
This strategy, Google’s Menace Intelligence Group (GTIG) added, has had the good thing about tricking English-speaking staff into performing actions that give the menace actors entry or result in the sharing of invaluable info resembling credentials, that are then used to facilitate knowledge theft.
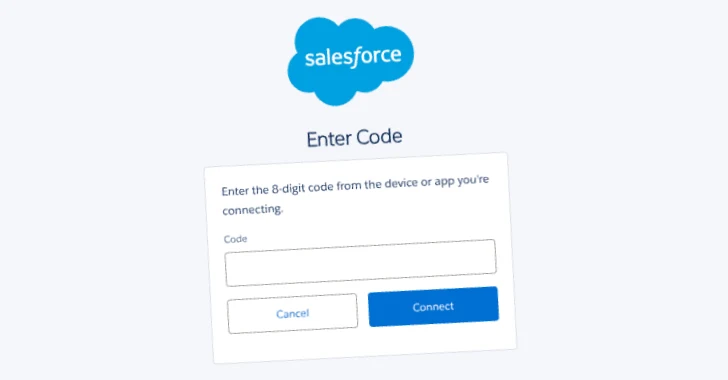
A noteworthy side of UNC6040’s actions includes the usage of a modified model of Salesforce’s Knowledge Loader that victims are deceived into authorizing in order to hook up with the group’s Salesforce portal in the course of the vishing assault. Knowledge Loader is an software used to import, export, and replace knowledge in bulk throughout the Salesforce platform.
Particularly, the attackers information the goal to go to Salesforce’s linked app setup web page and approve the modified model of the Knowledge Loader app that carries a distinct identify or branding (e.g., “My Ticket Portal”) from its respectable counterpart. This motion grants them unauthorized entry to the Salesforce buyer environments and exfiltrate knowledge.
Past knowledge loss, the assaults function a stepping stone for UNC6040 to maneuver laterally by means of the sufferer’s community, after which entry and harvest info from different platforms resembling Okta, Office, and Microsoft 365.
Choose incidents have additionally concerned extortion actions, however solely “a number of months” after the preliminary intrusions have been noticed, indicating an try to monetize and revenue off the stolen knowledge presumably in partnership with a second menace actor.
“Throughout these extortion makes an attempt, the actor has claimed affiliation with the well-known hacking group ShinyHunters, doubtless as a technique to extend stress on their victims,” Google mentioned.
UNC6040’s overlaps with teams linked to The Com stem from the concentrating on of Okta credentials and the usage of social engineering by way of IT help, a tactic that has been embraced by Scattered Spider, one other financially motivated menace actor that is a part of the loose-knit organized collective.
The vishing marketing campaign hasn’t gone unnoticed by Salesforce, which, in March 2025, warned of menace actors utilizing social engineering techniques to impersonate IT help personnel over the telephone and trick its prospects’ staff into gifting away their credentials or approving the modified Knowledge Loader app.
“They’ve been reported luring our prospects’ staff and third-party help employees to phishing pages designed to steal credentials and MFA tokens or prompting customers to navigate to the login.salesforce[.]com/setup/join web page as a way to add a malicious linked app,” the corporate mentioned.
“In some instances, we’ve got noticed that the malicious linked app is a modified model of the Knowledge Loader app revealed underneath a distinct identify and/or branding. As soon as the menace actor good points entry to a buyer’s Salesforce account or provides a linked app, they use the linked app to exfiltrate knowledge.”
The event not solely highlights the continued sophistication of social engineering campaigns, but in addition exhibits how IT help employees are being more and more focused as a technique to achieve preliminary entry.
“The success of campaigns like UNC6040’s, leveraging these refined vishing techniques, demonstrates that this strategy stays an efficient menace vector for financially motivated teams looking for to breach organizational defenses,” Google mentioned.
“Given the prolonged timeframe between preliminary compromise and extortion, it’s potential that a number of sufferer organizations and probably downstream victims may face extortion calls for within the coming weeks or months.”
Discovered this text fascinating? Observe us on Twitter and LinkedIn to learn extra unique content material we submit.