Jul 30, 2025Ravie LakshmananCryptocurrency / Browser Safety
Cybersecurity researchers are calling consideration to an ongoing marketing campaign that distributes pretend cryptocurrency buying and selling apps to deploy a compiled V8 JavaScript (JSC) malware known as JSCEAL that may seize information from credentials and wallets.
The exercise leverages 1000’s of malicious ads posted on Fb in an try to redirect unsuspecting victims to counterfeit websites that instruct them to put in the bogus apps, in keeping with Examine Level. These advertisements are shared both through stolen accounts or newly created ones.
“The actors separate the installer’s performance into completely different elements and most notably transfer some performance to the JavaScript recordsdata contained in the contaminated web sites,” the corporate stated in an evaluation. “A modular, multi-layered an infection move allows the attackers to adapt new ways and payloads at each stage of the operation.”
It is value noting that some features of the exercise had been beforehand documented by Microsoft in April 2025 and WithSecure as not too long ago as this month, with the latter monitoring it as WEEVILPROXY. In keeping with the Finnish safety vendor, the marketing campaign has been lively since March 2024.
The assault chains have been discovered to undertake novel anti-analysis mechanisms that depend on script-based fingerprinting, earlier than delivering the ultimate JSC payload.
“The risk actors applied a singular mechanism that requires each the malicious web site and the installer to run in parallel for profitable execution, which considerably complicates evaluation and detection efforts,” the Israeli cybersecurity firm famous.
Clicking on the hyperlink within the Fb advertisements triggers a redirection chain, finally main the sufferer to a pretend touchdown web page mimicking a reputable service like TradingView or a decoy web site, if the goal’s IP deal with is just not inside a desired vary or the referrer is just not Fb.
The web site additionally features a JavaScript file that makes an attempt to speak with a localhost server on port 30303, along with internet hosting two different JavaScript scripts which might be accountable for monitoring the set up course of and initiating POST requests which might be dealt with by the elements throughout the MSI installer.
For its half, the installer file downloaded from the positioning unpacks a lot of DLL libraries, whereas concurrently initiating HTTP listeners on localhost:30303 to course of incoming POST requests from the phony web site. This interdependency additionally implies that the an infection chain fails to proceed additional if any of those elements does not work.
“To make sure the sufferer doesn’t suspect irregular exercise, the installer opens a webview utilizing msedge_proxy.exe to direct the sufferer to the reputable web site of the applying,” Examine Level stated.
The DLL modules are designed to parse the POST requests from the web site and collect system info and start the fingerprinting course of, after which the captured info is exfiltrated to the attacker within the type of a JSON file via a PowerShell backdoor.
If the sufferer host is deemed worthwhile, the an infection chain strikes to the ultimate stage, resulting in the execution of the JSCEAL malware by leveraging Node.js.
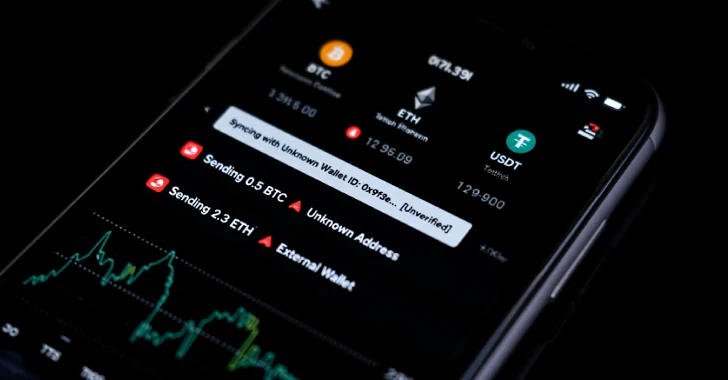
The malware, in addition to establishing connections with a distant server to obtain additional directions, units up an area proxy with the objective of intercepting the sufferer’s net visitors and injecting malicious scripts into banking, cryptocurrency, and different delicate web sites to steal their credentials in real-time.
Different capabilities of JSCEAL embody gathering system info, browser cookies, auto-fill passwords, Telegram account information, screenshots, keystrokes, in addition to conducting adversary-in-the-middle (AitM) assaults and manipulating cryptocurrency wallets. It may additionally act as a distant entry trojan.
“This refined piece of malware is designed to achieve absolute management of the sufferer machine, whereas being resilient in opposition to typical safety instruments,” Examine Level stated. “The mix of compiled code and heavy obfuscation, whereas displaying all kinds of performance, made evaluation efforts difficult and time-consuming.”
“Utilizing JSC recordsdata permits attackers to easily and successfully conceal their code, serving to it evade safety mechanisms, and making it troublesome to investigate.”