Aug 21, 2025Ravie LakshmananMalware / E-mail Safety
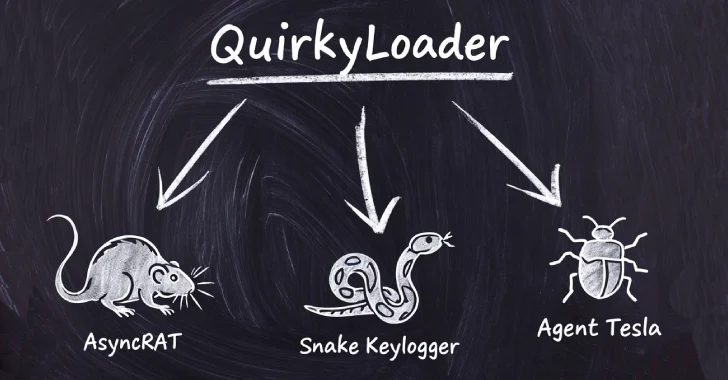
Cybersecurity researchers have disclosed particulars of a brand new malware loader known as QuirkyLoader that is getting used to ship through e mail spam campaigns an array of next-stage payloads starting from data stealers to distant entry trojans since November 2024.
Among the notable malware households distributed utilizing QuirkyLoader embody Agent Tesla, AsyncRAT, Formbook, Masslogger, Remcos RAT, Rhadamanthys Stealer, and Snake Keylogger.
IBM X-Power, which detailed the malware, stated the assaults contain sending spam emails from each respectable e mail service suppliers and a self-hosted e mail server. These emails function a malicious archive, which accommodates a DLL, an encrypted payload, and an actual executable.
“The actor makes use of DLL side-loading, a way the place launching the respectable executable additionally masses the malicious DLL,” safety researcher Raymond Joseph Alfonso stated. “This DLL, in flip, masses, decrypts, and injects the ultimate payload into its goal course of.”
That is achieved by utilizing course of hollowing to inject the malware into one of many three processes: AddInProcess32.exe, InstallUtil.exe, or aspnet_wp.exe.
The DLL loader, per IBM, has been utilized in restricted campaigns for the previous few months, with two campaigns noticed in July 2025 concentrating on Taiwan and Mexico.
The marketing campaign concentrating on Taiwan is claimed to have particularly singled out workers of Nusoft Taiwan, a community and web safety analysis firm based mostly in New Taipei Metropolis, with the aim of infecting them with Snake Keylogger, which is able to stealing delicate data from common internet browsers, keystrokes, and clipboard content material.
The Mexico-related marketing campaign, however, is assessed to be random, with the an infection chains delivering Remcos RAT and AsyncRAT.
“The menace actor persistently writes the DLL loader module in .NET languages and makes use of ahead-of-time (AOT) compilation,” Alfonso stated. “This course of compiles the code into native machine code earlier than execution, making the ensuing binary seem as if it had been written in C or C++.”
New Phishing Tendencies
The event comes as menace actors are utilizing new QR code phishing (aka quishing) techniques like splitting malicious QR codes into two elements or embedding them inside respectable ones in e mail messages propagated through phishing kits like Gabagool and Tycoon, respectively, to evade detection, demonstrating ongoing evolution.
“Malicious QR codes are common with attackers for a number of causes,” Barracuda researcher Rohit Suresh Kanase stated. “They can’t be learn by people so do not elevate any crimson flags, and so they can typically bypass conventional safety measures akin to e mail filters and hyperlink scanners.”
“Moreover, since recipients typically have to modify to a cellular gadget to scan the code, it could take customers out of the corporate safety perimeter and away from safety.”
The findings additionally comply with the emergence of a phishing equipment utilized by the PoisonSeed menace actor to accumulate credentials and two-factor authentication (2FA) codes from people and organizations to realize entry to victims’ accounts and use them to ship emails for finishing up cryptocurrency scams.
“The domains internet hosting this phishing equipment impersonate login companies from distinguished CRM and bulk e mail corporations like Google, SendGrid, Mailchimp, and certain others, concentrating on people’ credentials,” NVISO Labs stated. “PoisonSeed employs spear-phishing emails embedding malicious hyperlinks, which redirect victims to their phishing equipment.”
A noteworthy facet of the equipment is the usage of a way referred to as precision-validated phishing wherein the attacker validates an e mail handle in real-time within the background, whereas a faux Cloudflare Turnstile problem is served to the consumer. As soon as the checks are handed, a login kind impersonating the respectable on-line platform seems, permitting the menace actors to seize submitted credentials after which relay them to the service.