Nov 06, 2025Ravie LakshmananMalware / Community Safety
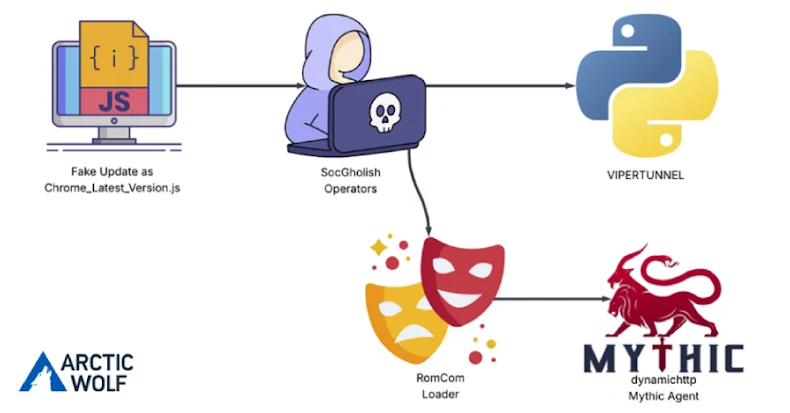
The risk actor referred to as Curly COMrades has been noticed exploiting virtualization applied sciences as a strategy to bypass safety options and execute customized malware.
In keeping with a brand new report from Bitdefender, the adversary is claimed to have enabled the Hyper-V position on chosen sufferer techniques to deploy a minimalistic, Alpine Linux-based digital machine.
“This hidden atmosphere, with its light-weight footprint (solely 120MB disk area and 256MB reminiscence), hosted their customized reverse shell, CurlyShell, and a reverse proxy, CurlCat,” safety researcher Victor Vrabie, together with Adrian Schipor and Martin Zugec, stated in a technical report.
Curly COMrades was first documented by the Romanian cybersecurity vendor in August 2025 in reference to a collection of assaults focusing on Georgia and Moldova. The exercise cluster is assessed to be lively since late 2023, working with pursuits which might be aligned with Russia.
These assaults have been discovered to deploy instruments like CurlCat for bidirectional knowledge switch, RuRat for persistent distant entry, Mimikatz for credential harvesting, and a modular .NET implant dubbed MucorAgent, with early iterations relationship again all the way in which to November 2023.
In a follow-up evaluation performed in collaboration with Georgia CERT, extra tooling related to the risk actor has been recognized, alongside makes an attempt to determine long-term entry by weaponizing Hyper-V on compromised Home windows 10 hosts to arrange a hidden distant working atmosphere.
“By isolating the malware and its execution atmosphere inside a VM, the attackers successfully bypassed many conventional host-based EDR detections,” the researchers stated. “The risk actor demonstrated a transparent willpower to keep up a reverse proxy functionality, repeatedly introducing new tooling into the atmosphere.”
In addition to utilizing Resocks, Rsockstun, Ligolo-ng, CCProxy, Stunnel, and SSH-based strategies for proxy and tunneling, Curly COMrades has employed numerous different instruments, together with a PowerShell script designed for distant command execution and CurlyShell, a beforehand undocumented ELF binary deployed within the digital machine that gives a persistent reverse shell.
Written in C++, the malware is executed as a headless background daemon to connect with a command-and-control (C2) server and launch a reverse shell, permitting the risk actors to run encrypted instructions. Communication is achieved by way of HTTP GET requests to ballot the server for brand spanking new instructions and utilizing HTTP POST requests to transmit the outcomes of the command execution again to the server.
“Two customized malware households – CurlyShell and CurlCat – have been on the heart of this exercise, sharing a largely equivalent code base however diverging in how they dealt with obtained knowledge: CurlyShell executed instructions straight, whereas CurlCat funneled visitors by way of SSH,” Bitdefender stated. “These instruments have been deployed and operated to make sure versatile management and adaptableness.”