Jun 12, 2025Ravie LakshmananThreat Intelligence / Malware
The menace actors behind the VexTrio Viper Site visitors Distribution Service (TDS) have been linked to different TDS companies like Assist TDS and Disposable TDS, indicating that the subtle cybercriminal operation is a sprawling enterprise of its personal that is designed to distribute malicious content material.
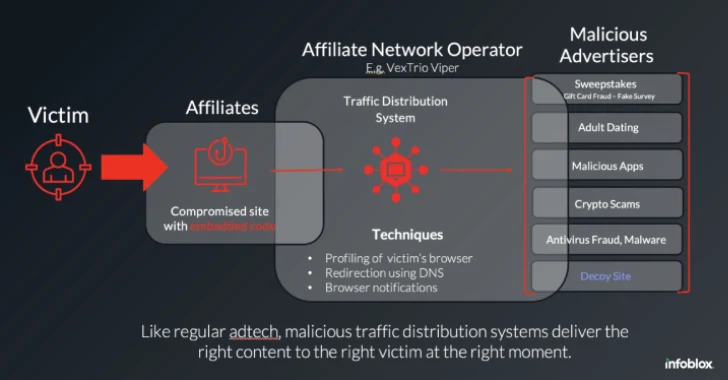
“VexTrio is a bunch of malicious adtech firms that distribute scams and dangerous software program by way of totally different promoting codecs, together with smartlinks and push notifications,” Infoblox mentioned in a deep-dive report shared with The Hacker Information.
A number of the malicious adtech firms underneath VexTrio Viper embrace Los Pollos, Taco Loco, and Adtrafico. These firms function what’s referred to as a industrial affiliate community that connects malware actors whose web sites unsuspecting customers land on and so-called “promoting associates” who supply varied types of illicit schemes like reward card fraud, malicious apps, phishing websites, and scams.
Put otherwise, these malicious visitors distribution techniques are designed to redirect victims to their locations by means of a SmartLink or direct supply. Los Pollos, per the DNS menace intelligence agency, enlists malware distributors (aka publishing associates) with guarantees of high-paying gives, whereas Taco Loco focuses on push monetization and recruits promoting associates.
One other notable element of those assaults is the compromise of WordPress web sites to inject malicious code that is accountable for initiating the redirection chain, in the end main guests to VexTrio rip-off infrastructure. Examples of such injections embrace Balada, DollyWay, Sign1, and DNS TXT file campaigns.
“These scripts redirect web site guests to varied rip-off pages by means of visitors dealer networks related to VexTrio, one of many largest recognized cybercriminal affiliate networks that leverages refined DNS strategies, visitors distribution techniques, and area technology algorithms to ship malware and scams throughout world networks,” GoDaddy famous in a report printed in March 2025.
VexTrio’s operations suffered a blow round mid-November 2024 after Qurium revealed that the Swiss-Czech adtech firm Los Pollos was a part of VexTrio, inflicting Los Pollos to stop their push hyperlink monetization. This, in flip, triggered an exodus, inflicting menace actors that relied closely on the Los Pollos community to maneuver to alternate redirect locations equivalent to Assist TDS and Disposable TDS.
Modifications in habits over time from the 2 unbiased C2 units
Infoblox’s evaluation of 4.5 million DNS TXT file responses from compromised web sites over a six-month interval has revealed that the domains that have been a part of the DNS TXT file campaigns may very well be categorised into two units, every with its personal distinct command-and-control (C2) server.
“Each servers have been hosted in Russian-connected infrastructure, however neither their internet hosting nor their TXT responses overlapped,” the corporate mentioned. “Every set maintained totally different redirect URL buildings, regardless that they each initially led to VexTrio and subsequently to the Assist TDS.”
Additional proof has uncovered that each Assist TDS and Disposable TDS are one and the identical, and that the companies loved an “unique relationship” with VexTrio till November 2024. Assist TDS, which traditionally redirected visitors to VexTrio domains, has since shifted to Monetizer, a monetization platform that makes use of TDS expertise to attach net visitors from writer associates to advertisers.
“The Assist TDS has a robust Russian nexus, with internet hosting and area registration steadily performed by way of Russian entities,” Infoblox mentioned, describing the operators as presumably unbiased. “It doesn’t have the full-blown performance of the VexTrio TDSs and has no apparent industrial ties past its eerie connections with VexTrio.”
VexTrio is one among the many many TDSs which were outed as industrial adtech companies, the others being Companions Home, BroPush, RichAds, Admeking, and RexPush. Many of those are geared in direction of push notification companies by making use of Google Firebase Cloud Messaging (FCM) or Push API-based custom-developed scripts to distribute hyperlinks to malicious content material by way of push notifications.
“A whole lot of 1000’s of compromised web sites around the globe yearly redirect victims to the tangled net of VexTrio and VexTrio-affiliate TDSs,” the corporate mentioned.
“VexTrio and the opposite affiliate promoting firms know who the malware actors are, or they a minimum of have sufficient data to trace them down. Lots of the firms are registered in international locations that require some extent of ‘know your buyer’ (KYC), however even with out these necessities, publishing associates are vetted by their buyer managers.”
Discovered this text attention-grabbing? Observe us on Twitter and LinkedIn to learn extra unique content material we put up.