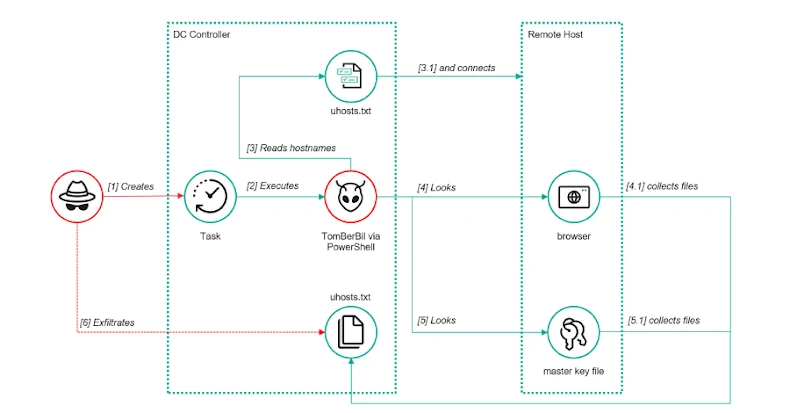
A legislation enforcement operation coordinated by INTERPOL has led to the restoration of $3 million and the arrest of 574 suspects by authorities from 19 nations, amidst a continued crackdown on cybercrime networks in Africa.
The coordinated effort, named Operation Sentinel, befell between October 27 and November 27, 2025, and primarily targeted on enterprise electronic mail compromise (BEC), digital extortion, and ransomware on the continent.
Collaborating nations included Benin, Botswana, Burkina Faso, Cameroon, Chad, Congo, Djibouti, Democratic Republic of the Congo, Gabon, Ghana, Kenya, Malawi, Nigeria, Senegal, South Africa, South Sudan, Uganda, Zambia, and Zimbabwe.
Over the course of the initiative, greater than 6,000 malicious hyperlinks have been taken down and 6 distinct ransomware variants have been decrypted. The names of the ransomware households weren’t disclosed. The investigated incidents have been linked to estimated monetary losses exceeding $21 million, INTERPOL added.
A number of suspects have been arrested in reference to a ransomware assault concentrating on an unnamed Ghanaian monetary establishment that encrypted 100 terabytes of knowledge and stole about $120,000.
As well as, Ghanaian authorities took down a cyber fraud community working throughout Ghana and Nigeria that defrauded greater than 200 victims of over $400,000 utilizing well-designed web sites and cellular apps, which impersonated in style fast-food manufacturers to gather funds for pretend orders.
As a part of the hassle, 10 people have been apprehended, 100 digital gadgets have been seized, and 30 fraudulent servers have been taken offline.
Regulation enforcement from Benin additionally dismantled 43 malicious domains and 4,318 social media accounts that have been used to additional extortion schemes and scams. The operation culminated within the arrest of 106 folks.
“The size and class of cyber assaults throughout Africa are accelerating, particularly in opposition to vital sectors like finance and power,” Neal Jetton, INTERPOL’s director of cybercrime, mentioned.
Operation Sentinel is a part of the African Joint Operation in opposition to Cybercrime (AFJOC), which goals to boost the capabilities of nationwide legislation enforcement businesses in Africa and higher disrupt cybercriminal exercise within the area.
Ukrainian Nationwide Pleads Responsible to Nefilim Ransomware Assaults
The disclosure comes as a 35-year-old from Ukraine pleaded responsible within the U.S. to utilizing Nefilim ransomware to assault corporations within the nation and elsewhere in his capability as an affiliate. Artem Aleksandrovych Stryzhak was arrested in Spain in June 2024 and extradited to the U.S. earlier this April.
In September, the Justice Division (DoJ) charged one other Ukrainian nationwide, Volodymyr Viktorovich Tymoshchuk, for his function because the administrator of the LockerGoga, MegaCortex, and Nefilim ransomware operations between December 2018 and October 2021.
Tymoshchuk stays at giant, though authorities have introduced a $11 million reward for info resulting in his arrest or conviction. Tymoshchuk can be on essentially the most wished lists of each the U.S. Federal Bureau of Investigation (FBI) and the European Union (E.U.). Nefilim’s victims span the U.S., Germany, the Netherlands, Norway, and Switzerland.
“In June 2021, Nefilim directors gave Stryzhak entry to the Nefilim ransomware code in trade for 20 % of his ransom proceeds,” the DoJ mentioned. “Stryzhak and others researched potential victims after gaining unauthorized entry to their networks, together with by utilizing on-line databases to acquire details about the businesses’ internet price, measurement, and phone info.”
Round July 2021, a Nefilim administrator is alleged to have inspired Stryzhak to focus on corporations within the U.S., Canada, and Australia with greater than $200 million {dollars} in annual income. Nefilim operated underneath a double extortion mannequin, pressurizing victims to pay up or danger getting their stolen knowledge revealed on a publicly accessible knowledge leaks website referred to as Company Leaks that was maintained by the directors.
Stryzhak pleaded responsible to conspiracy to commit fraud associated to computer systems in connection along with his Nefilim ransomware actions. He’s scheduled to be sentenced on Could 6, 2026. If discovered responsible, he faces a most penalty of 10 years in jail.