Cybersecurity researchers are calling consideration to a brand new marketing campaign that is leveraging a mix of ClickFix lures and pretend grownup web sites to deceive customers into operating malicious instructions beneath the guise of a “crucial” Home windows safety replace.
“Marketing campaign leverages pretend grownup web sites (xHamster, PornHub clones) as its phishing mechanism, probably distributed through malvertising,” Acronis stated in a brand new report shared with The Hacker Information. “The grownup theme, and potential connection to shady web sites, provides to the sufferer’s psychological strain to adjust to sudden ‘safety replace’ set up.”
ClickFix-style assaults have surged over the previous yr, usually tricking customers into operating malicious instructions on their very own machines utilizing prompts for technical fixes or finishing CAPTCHA verification checks. In response to knowledge from Microsoft, ClickFix has develop into the most typical preliminary entry methodology, accounting for 47% of assaults.
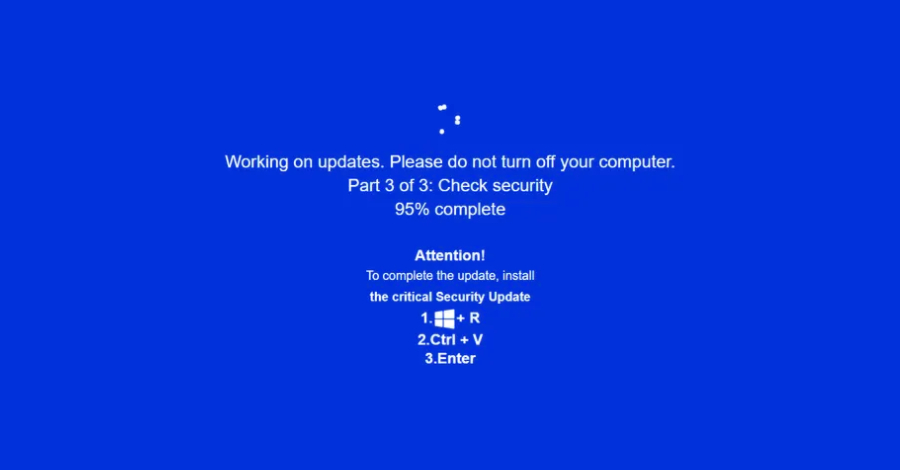
The newest marketing campaign shows extremely convincing pretend Home windows replace screens in an try and get the sufferer to run malicious code, indicating that attackers are shifting away from the standard robot-check lures. The exercise has been codenamed JackFix by the Singapore-based cybersecurity firm.
Maybe probably the most regarding facet of the assault is that the phony Home windows replace alert hijacks your entire display screen and instructs the sufferer to open the Home windows Run dialog, press Ctrl + V, and hit Enter, thereby triggering the an infection sequence.
It is assessed that the place to begin of the assault is a pretend grownup website to which unsuspecting customers are redirected through malvertising or different social engineering strategies, solely to immediately serve them an “pressing safety replace.” Choose iterations of the websites have been discovered to incorporate developer feedback in Russian, hinting at the opportunity of a Russian-speaking risk actor.
“The Home windows Replace display screen is created completely utilizing HTML and JavaScript code, and pops up as quickly because the sufferer interacts with any component on the phishing website,” safety researcher Eliad Kimhy stated. “The web page makes an attempt to go full display screen through JavaScript code, whereas on the similar time creating a reasonably convincing Home windows Replace window composed of a blue background and white textual content, paying homage to Home windows’ notorious blue display screen of loss of life.”
What’s notable in regards to the assault is that it closely leans on obfuscation to hide ClickFix-related code, in addition to blocks customers from escaping the full-screen alert by disabling the Escape and F11 buttons, together with F5 and F12 keys. Nonetheless, resulting from defective logic, customers can nonetheless press the Escape and F11 buttons to do away with the total display screen.
The preliminary command executed is an MSHTA payload that is launched utilizing the reliable mshta.exe binary, which, in flip, accommodates JavaScript designed to run a PowerShell command to retrieve one other PowerShell script from a distant server. These domains are designed such that immediately navigating to those addresses redirects the consumer to a benign website like Google or Steam.
“Solely when the positioning is reached out to through an irm or iwr PowerShell command does it reply with the right code,” Acronis defined. “This creates an additional layer of obfuscation and evaluation prevention.”
The downloaded PowerShell script additionally packs in numerous obfuscation and anti-analysis mechanisms, certainly one of which is using rubbish code to complicate evaluation efforts. It additionally makes an attempt to raise privileges and creates Microsoft Defender Antivirus exclusions for command-and-control (C2) addresses and paths the place the payloads are staged.
To realize privilege escalation, the malware makes use of the Begin-Course of cmdlet along side the “-Verb RunAs” parameter to launch PowerShell with administrative rights and constantly prompts for permission till it is granted by the sufferer. As soon as this step is profitable, the script is designed to drop further payloads, akin to easy distant entry trojans (RATs) which might be programmed to contact a C2 server, presumably to drop extra malware.
The PowerShell script has additionally been noticed to serve as much as eight completely different payloads, with Acronis describing it because the “most egregious instance of spray and pray.” These embrace Rhadamanthys Stealer, Vidar Stealer 2.0, RedLine Stealer, Amadey, in addition to different unspecified loaders and RATs.
“If solely certainly one of these payloads manages to run efficiently, victims danger shedding passwords, crypto wallets, and extra,” Kimhy stated. “Within the case of some of those loaders — the attacker could select to herald different payloads into the assault, and the assault can rapidly escalate additional.”
The disclosure comes as Huntress detailed a multi-stage malware execution chain that originates from a ClickFix lure masquerading as a Home windows replace and deploys stealer malware like Lumma and Rhadamanthys by concealing the ultimate levels inside a picture, a method referred to as steganography.
Like within the case of the aforementioned marketing campaign, the ClickFix command copied to the clipboard and pasted into the Run dialog makes use of mshta.exe to run a JavaScript payload that is able to operating a remotely-hosted PowerShell script immediately in reminiscence.
The PowerShell code is used to decrypt and launch a .NET meeting payload, a loader dubbed Stego Loader that serves as a conduit for the execution of Donut-packed shellcode hidden inside an embedded and encrypted PNG file. The extracted shellcode is then injected right into a goal course of to in the end deploy Lumma or Rhadamanthys.
Curiously, one of many domains listed by Huntress as getting used to fetch the PowerShell script (“securitysettings[.]reside”) has additionally been flagged by Acronis, suggesting these two exercise clusters could also be associated.
“The risk actor typically modifications the URI (/tick.odd, /gpsc.dat, /ercx.dat, and many others.) used to host the primary mshta.exe stage,” safety researchers Ben Folland and Anna Pham stated within the report.
“Moreover, the risk actor moved from internet hosting the second stage on the area securitysettings[.]reside and as an alternative hosted on xoiiasdpsdoasdpojas[.]com, though each level to the identical IP handle 141.98.80[.]175, which was additionally used to ship the primary stage [i.e., the JavaScript code run by mshta.exe].”
ClickFix has develop into vastly profitable because it depends on a easy but efficient methodology, which is to entice a consumer into infecting their very own machine and bypassing safety controls. Organizations can defend towards such assaults by coaching staff to raised spot the risk and disabling the Home windows Run field through Registry modifications or Group Coverage.