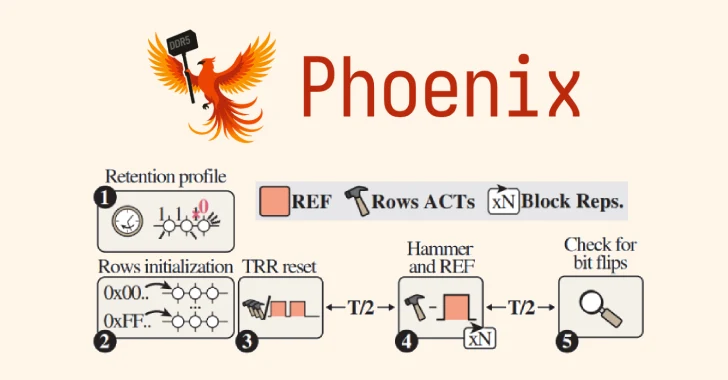
Aug 13, 2025The Hacker NewsArtificial Intelligence / Menace Searching
Safety operations have by no means been a 9-to-5 job. For SOC analysts, the day usually begins and ends deep in a queue of alerts, chasing down what seems to be false positives, or switching between half a dozen instruments to piece collectively context. The work is repetitive, time-consuming, and high-stakes, leaving SOCs underneath fixed stress to maintain up, but usually struggling to remain forward of rising threats. That mixture of inefficiency, elevated threat, and a reactive working mannequin is strictly the place AI-powered SOC capabilities are beginning to make a distinction.
Why AI SOC is gaining traction now
The latest Gartner Hype Cycle for Safety Operations 2025 (obtain a complimentary copy) acknowledges AI SOC Brokers as an innovation set off, reflecting a broader shift in how groups method automation. As a substitute of relying solely on static playbooks or handbook investigation workflows, AI SOC capabilities convey reasoning, adaptability, and context-aware decision-making into the combo.
SOC groups report that their most urgent challenges are inefficient investigations, siloed instruments, and a scarcity of efficient automation. These points gradual response and improve threat. The most recent SANS SOC Survey underscores this, displaying these operational hurdles persistently outpace different considerations. AI-driven triage, investigation, and detection protection evaluation are well-positioned to deal with these gaps head-on.
AI’s greatest wins within the SOC
An AI SOC brings collectively a variety of capabilities that strengthen and scale the core capabilities of a safety operations heart. These capabilities work alongside human experience to enhance how groups triage alerts, examine threats, reply to incidents, and refine detections over time.
Triage at velocity and scale
AI programs can evaluate and prioritize each incoming alert inside minutes, pulling telemetry from throughout the surroundings. True threats rise to the highest shortly, whereas false positives are resolved with out draining analyst time.
Sooner, deeper investigations and response
By correlating information from SIEM, EDR, id, electronic mail, and cloud platforms, AI SOC instruments cut back imply time to research (MTTI) and imply time to reply (MTTR). This shortens dwell time and limits the chance for threats to unfold.
Detection engineering insights
AI can pinpoint protection gaps towards frameworks comparable to MITRE ATT&CK, determine guidelines that want tuning, and suggest changes primarily based on actual investigation information. This offers detection engineers a transparent view of the place adjustments will take advantage of influence.
Enabling extra menace searching
With much less time spent working alert queues, analysts can shift to proactive menace searching. AI SOC platforms with pure language question help make it simpler to discover information, run complicated hunts, and floor hidden threats.
Separating hype from actuality
The AI SOC market is stuffed with sweeping claims about absolutely autonomous SOC and instantaneous outcomes. Whereas AI can automate giant parts of tier 1 and tier 2 investigations and even help tier 3 work, it’s not a alternative for skilled analysts. Complicated, excessive influence instances nonetheless require human judgment, contextual understanding, and resolution making.
The true worth lies in shifting the stability of labor. By eradicating repetitive triage and dashing investigations, AI frees analysts to give attention to greater influence actions like superior menace searching, tuning detections, and investigating refined threats. That is the work that improves each safety outcomes and analyst retention.
Guiding ideas for evaluating AI SOC capabilities
When assessing AI SOC options, give attention to ideas that decide whether or not they can ship sustainable enhancements to safety operations:
Transparency and explainability – The system ought to present clear, detailed reasoning for its findings, permitting analysts to hint conclusions again to the underlying information and logic. This builds belief and allows knowledgeable resolution making.
Information privateness and safety – Perceive precisely the place information is processed and saved, how it’s protected in transit and at relaxation, and whether or not the deployment mannequin meets your compliance necessities.
Integration depth – The answer ought to combine seamlessly along with your present SOC stack and workflows. This consists of preserving the acquainted person expertise of instruments like SIEM, EDR, and case administration programs to keep away from introducing friction.
Adaptability and studying – AI ought to enhance over time by incorporating analyst suggestions, adapting to adjustments in your surroundings, and staying efficient towards evolving threats.
Accuracy and belief – Consider not simply the quantity of labor automated, however the precision and reliability of outcomes. A device that closes false positives at scale however misses actual threats creates extra threat than it solves.
Time to worth – Favor options that ship measurable beneficial properties in investigation velocity, accuracy, or protection inside weeks quite than months, with out heavy customization or prolonged deployments.
The human and AI hybrid SOC
The best SOCs mix the velocity and scale of AI with the contextual understanding and judgment of human analysts. This mannequin provides folks the capability to give attention to the work that issues most.
How Prophet Safety aligns with this imaginative and prescient
Prophet Safety helps organizations transfer past handbook investigations and alert fatigue with an agentic AI SOC platform that automates triage, accelerates investigations, and ensures each alert will get the eye it deserves. By integrating throughout the present stack, Prophet AI improves analyst effectivity, reduces incident dwell time, and delivers extra constant safety outcomes. Safety leaders use Prophet AI to maximise the worth of their folks and instruments, strengthen their safety posture, and switch each day SOC operations into measurable enterprise outcomes. Go to Prophet Safety to request a demo and see how Prophet AI can elevate your SOC operations.
Discovered this text attention-grabbing? This text is a contributed piece from one among our valued companions. Observe us on Google Information, Twitter and LinkedIn to learn extra unique content material we put up.