Sep 20, 2025Ravie LakshmananSoftware Safety / Malware
LastPass is warning of an ongoing, widespread info stealer marketing campaign concentrating on Apple macOS customers by means of faux GitHub repositories that distribute malware-laced packages masquerading as legit instruments.
“Within the case of LastPass, the fraudulent repositories redirected potential victims to a repository that downloads the Atomic infostealer malware,” researchers Alex Cox, Mike Kosak, and Stephanie Schneider from the LastPass Risk Intelligence, Mitigation, and Escalation (TIME) staff stated.
Past LastPass, a few of the common instruments impersonated within the marketing campaign embody 1Password, Basecamp, Dropbox, Gemini, Hootsuite, Notion, Obsidian, Robinhood, Salesloft, SentinelOne, Shopify, Thunderbird, and TweetDeck, amongst others. All of the GiHub repositories are designed to focus on macOS techniques.
The assaults contain the usage of Search Engine Optimization (search engine marketing) poisoning to push hyperlinks to malicious GitHub websites on high of search outcomes on Bing and Google, that then instruct customers to the obtain this system by clicking the “Set up LastPass on MacBook” button, redirecting them a GitHub web page area.
“The GitHub pages seem like created by a number of GitHub usernames to get round takedowns,” LastPass stated.
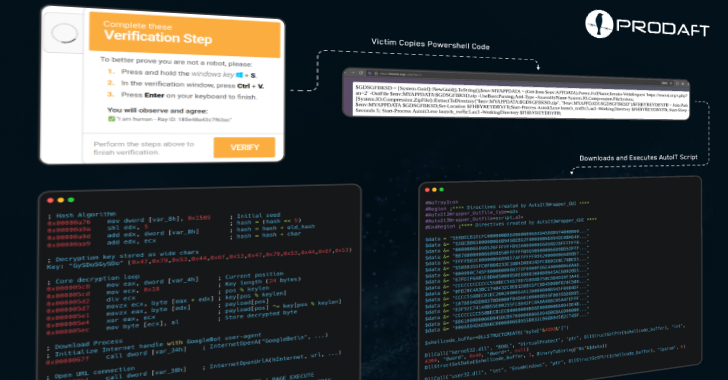
The GitHub web page is designed to take the consumer to a different area that gives ClickFix-style directions to repeat and execute a command on the Terminal app, ensuing within the deployment of the Atomic Stealer malware.
It is price noting comparable campaigns have been beforehand leveraged malicious sponsored Google Adverts for Homebrew to distribute a multi-stage dropper by means of a bogus GitHub repository that may run detect digital machines or evaluation environments, and decode and execute system instructions to ascertain reference to a distant server, per safety researcher Dhiraj Mishra.
In latest weeks, risk actors have been noticed leveraging public GitHub repositories to host malicious payloads and distribute them through Amadey, in addition to make use of dangling commits similar to an official GitHub repository to redirect unwitting customers to malicious packages.