Cybersecurity researchers have make clear a novel assault chain that employs phishing emails to ship an open-source backdoor referred to as VShell.
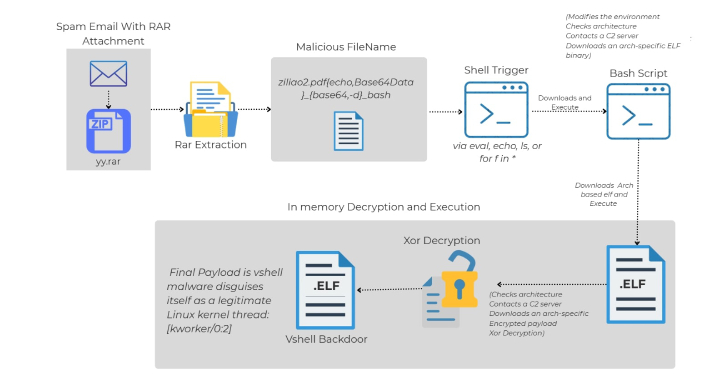
The “Linux-specific malware an infection chain that begins with a spam electronic mail with a malicious RAR archive file,” Trellix researcher Sagar Bade stated in a technical write-up.
“The payload is not hidden contained in the file content material or a macro, it is encoded instantly within the filename itself. By way of intelligent use of shell command injection and Base64-encoded Bash payloads, the attacker turns a easy file itemizing operation into an automated malware execution set off.”
The method, the cybersecurity firm added, takes benefit of a easy but harmful sample generally noticed in shell scripts that arises when file names are evaluated with insufficient sanitization, thereby inflicting a trivial command like eval or echo to facilitate the execution of arbitrary code.
What’s extra, the method provides the added benefit of getting round conventional defenses, as antivirus engines do not usually scan file names.
The start line of the assault is an electronic mail message containing a RAR archive, which features a file with a maliciously crafted file title: “ziliao2.pdf`{echo,}|{base64,-d}|bash`”
Particularly, the file title incorporates Bash-compatible code that is engineered to execute instructions when it is interpreted by the shell. It is price noting that merely extracting the file from the archive doesn’t set off execution. Fairly, it happens solely when a shell script or command makes an attempt to parse the file title.
One other necessary facet to contemplate right here is that it is not attainable to manually create a file title with this syntax, that means it was probably created utilizing one other language or dropped utilizing an exterior instrument or script that bypasses shell enter validation, Trellix stated.
This, in flip, results in the execution of an embedded Base64-encoded downloader, which then retrieves from an exterior server an ELF binary for the suitable system structure (x86_64, i386, i686, armv7l, or aarch64). The binary, for its half, initiates communication with a command-and-control (C2) server to acquire the encrypted VShell payload, decode, and execute it on the host.
Trellix stated the phishing emails are disguised as an invite for a magnificence product survey, luring recipients with a financial reward (10 RMB) for finishing it.
“Crucially, the e-mail features a RAR archive attachment (‘yy.rar’), though it does not explicitly instruct the person to open or extract it,” Bade defined. “The social engineering angle is refined: The person is distracted by the survey content material, and the presence of the attachment could be mistaken for a survey-related doc or information file.”
VShell is a Go-based distant entry instrument that has been extensively put to make use of by Chinese language hacking teams lately, together with UNC5174, supporting reverse shell, file operations, course of administration, port forwarding, and encrypted C2 communications.
What makes this assault harmful is that the malware operates fully in-memory, avoiding disk-based detection, to not point out it might probably goal a variety of Linux units.
“This evaluation highlights a harmful evolution in Linux malware supply the place a easy file title embedded in a RAR archive will be weaponized to execute arbitrary instructions,” Trellix stated. “The an infection chain exploits command injection in shell loops, abuses Linux’s permissive execution atmosphere, and in the end delivers a strong backdoor VShell malware able to full distant management over the system.”
The event comes as Picus Safety launched a technical evaluation of a Linux-focused post-exploit instrument dubbed RingReaper that leverages the Linux kernel’s io_uring framework to bypass conventional monitoring instruments. It is at present not recognized who’s behind the malware.
“As an alternative of invoking commonplace capabilities comparable to learn, write, recv, ship, or join, RingReaper employs io_uringprimitives (e.g., io_uring_prep_*) to execute equal operations asynchronously,” safety researcher Sıla Özeren Hacıoğlu stated. “This methodology helps bypass hook-based detection mechanisms and reduces the visibility of malicious exercise in telemetry generally gathered by EDR platforms.”
RingReaper makes use of io_uring to enumerate system processes, lively pseudo-terminal (PTS) classes, community connections, and logged-in customers, whereas decreasing its footprint and avoiding detection. It is also able to amassing person info from the “/and so on/passwd” file, abusing SUID binaries for privilege escalation, and erasing traces of itself after execution.
“It exploits the Linux kernel’s trendy asynchronous I/O interface, io_uring, to attenuate reliance on standard system calls that safety instruments incessantly monitor or hook,” Picus stated.