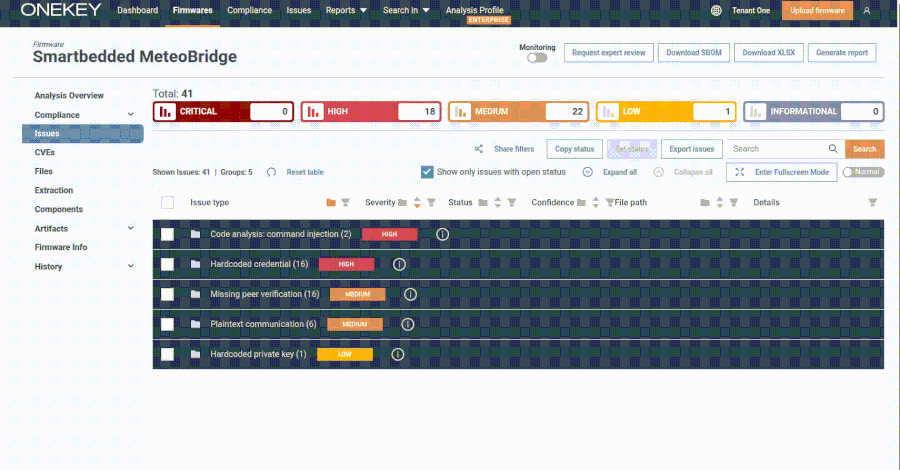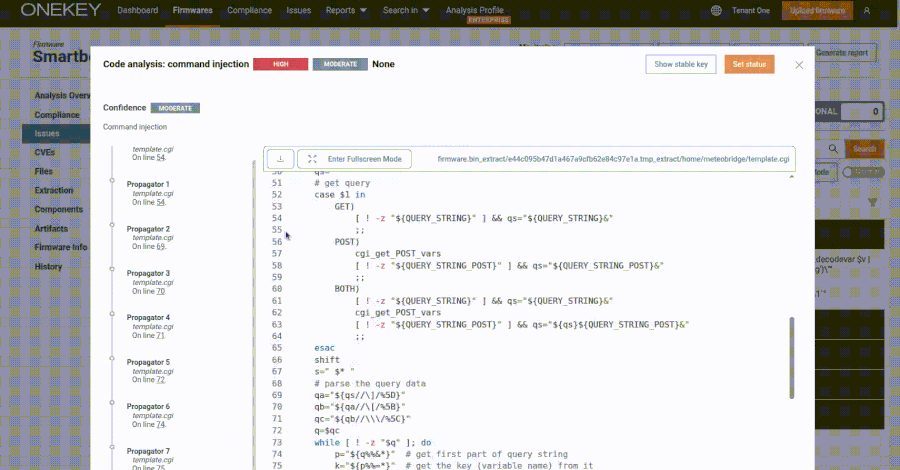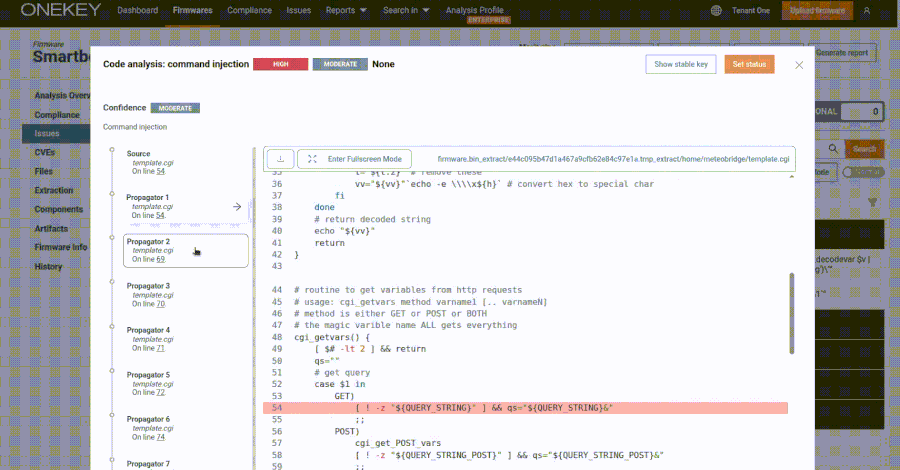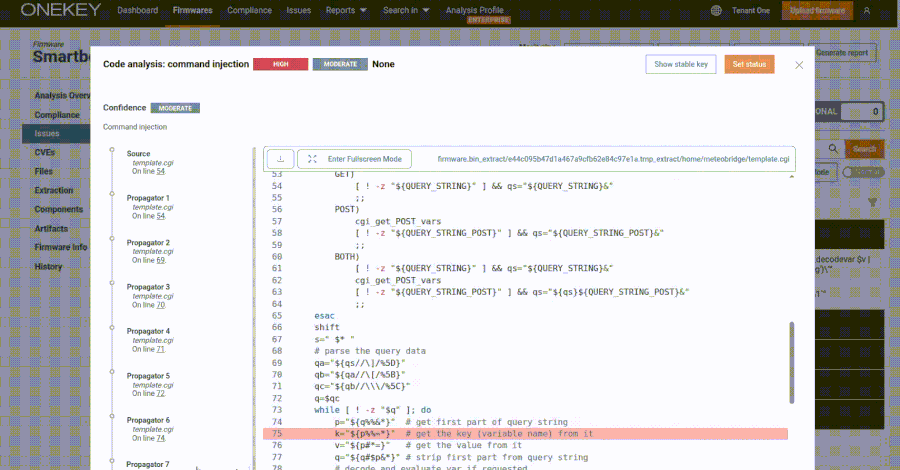
The maintainers of the nx construct system have alerted customers to a provide chain assault that allowed attackers to publish malicious variations of the favored npm bundle and different auxiliary plugins with data-gathering capabilities.
“Malicious variations of the nx bundle, in addition to some supporting plugin packages, have been printed to npm, containing code that scans the file system, collects credentials, and posts them to GitHub as a repo below the person’s accounts,” the maintainers mentioned in an advisory printed Wednesday.
Nx is an open-source, technology-agnostic construct platform that is designed to handle codebases. It is marketed as an “AI-first construct platform that connects every thing out of your editor to CI [continuous integration].” The npm bundle has over 3.5 million weekly downloads.
The checklist of affected packages and variations is under. These variations have since been faraway from the npm registry. The compromise of the nx bundle passed off on August 26, 2025.
nx 21.5.0, 20.9.0, 20.10.0, 21.6.0, 20.11.0, 21.7.0, 21.8.0, 20.12.0
@nx/devkit 21.5.0, 20.9.0
@nx/enterprise-cloud 3.2.0
@nx/eslint 21.5.0
@nx/js 21.5.0, 20.9.0
@nx/key 3.2.0
@nx/node 21.5.0, 20.9.0
@nx/workspace 21.5.0, 20.9.0
The venture maintainers mentioned the basis reason for the difficulty stemmed from a weak workflow that launched the power to inject executable code utilizing a specifically crafted title in a pull request (PR).
“The pull_request_target set off was used as a technique to set off the motion to run every time a PR was created or modified,” the nx crew mentioned. “Nevertheless, what was missed is the warning that this set off, not like the usual pull_request set off, runs workflows with elevated permissions, together with a GITHUB_TOKEN which has learn/write repository permission.”
It is believed the GITHUB_TOKEN was utilized to set off the “publish.yml” workflow, which is chargeable for publishing the Nx packages to the registry utilizing an npm token.
However with the PR validation workflow working with elevated privileges, the “publish.yml workflow” is triggered to run on the “nrwl/nx” repository whereas additionally introducing malicious modifications that made it doable to exfiltrate the npm token to an attacker-controlled webhook[.]website endpoint.
“As a part of the bash injection, the PR validation workflows triggered a run of the publish.yml with this malicious commit and despatched our npm token to an unfamiliar webhook,” the nx crew defined. “We consider that is how the person obtained a maintain of the npm token used to publish the malicious variations of nx.”
In different phrases, the injection flaw enabled arbitrary command execution if a malicious PR title was submitted, whereas the pull_request_target set off granted elevated permissions by offering a GITHUB_TOKEN with learn/write entry to the repository.
The rogue variations of the packages have been discovered to comprise a postinstall script that is activated after bundle set up to scan a system for textual content information, gather credentials, and ship the main points as a Base64-encoded string to a publicly accessible GitHub repository containing the identify “s1ngularity-repository” (or “s1ngularity-repository-0” and “s1ngularity-repository-1”) below the person’s account.
“The malicious postinstall script additionally modified the .zshrc and .bashrc information that are run every time a terminal is launched to incorporate sudo shutdown -h 0 which immediate customers for his or her system password and if offered, would shut down the machine instantly,” the maintainers added.
Whereas GitHub has since began to archive these repositories, customers who encounter the repositories are suggested to imagine compromise and rotate GitHub and npm credentials and tokens. Customers are additionally advisable to cease utilizing the malicious packages and verify .zshrc and .bashrc information for any unfamiliar directions and take away them.
The nx crew mentioned they’ve additionally undertaken remedial actions by rotating their npm and GitHub tokens, auditing GitHub and npm actions throughout the group for suspicious actions, and updating Publish entry for nx to require two-factor authentication (2FA) or automation.
Wiz researchers Merav Bar and Rami McCarthy mentioned 90% of over 1,000 leaked GitHub tokens are nonetheless legitimate, in addition to dozens of legitimate cloud credentials and npm tokens. It is mentioned the malware was run on developer machines, usually by way of the nx Visible Studio Code extension. As many as 1,346 repositories with the string “s1ngularity-repository” have been detected by GitGuardian.
Among the many 2,349 distinct secrets and techniques leaked, the overwhelming majority of them account for GitHub OAuth keys and private entry tokens (PATs), adopted by API keys and credentials for Google AI, OpenAI, Amazon Internet Providers, OpenRouter, Anthropic Claude, PostgreSQL, and Datadog.
The cloud safety agency discovered that the payload is able to working solely on Linux and macOS programs, systematically looking for delicate information and extracting credentials, SSH keys, and .gitconfig information.
“Notably, the marketing campaign weaponized put in AI CLI instruments by prompting them with harmful flags (–dangerously-skip-permissions, –yolo, –trust-all-tools) to steal file system contents, exploiting trusted instruments for malicious reconnaissance,” the corporate mentioned.
StepSecurity mentioned the incident marks the primary identified case the place attackers have turned developer AI assistants like Claude, Google Gemini, and Amazon Q into instruments for provide chain exploitation and bypass conventional safety boundaries.
“There are a couple of variations between the malware within the scoped nx packages (i.e. @nx/devkit, @nx/eslint) versus the malware within the nx bundle,” Socket mentioned. “First, the AI immediate is completely different. In these packages, the AI immediate is a little more fundamental. This LLM immediate can be a lot much less broad in scope, concentrating on crypto-wallet keys and secret patterns in addition to particular directories, whereas those in @nx grabs any fascinating textual content file.”
Charlie Eriksen of Aikido mentioned using LLM shoppers as a vector for enumerating secrets and techniques on the sufferer machine is a novel strategy, and provides defenders perception into the route the attackers could also be heading sooner or later.
“Given the recognition of the Nx ecosystem, and the novelty of AI software abuse, this incident highlights the evolving sophistication of provide chain assaults,” StepSecurity’s Ashish Kurmi mentioned. “Fast remediation is crucial for anybody who put in the compromised variations.”