Ravie LakshmananJan 31, 2026Social Engineering / SaaS Safety
Google-owned Mandiant on Friday stated it recognized an “enlargement in risk exercise” that makes use of tradecraft in line with extortion-themed assaults orchestrated by a financially motivated hacking group referred to as ShinyHunters.
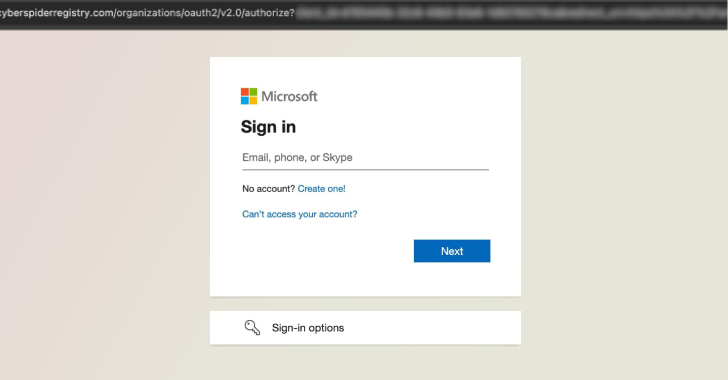
The assaults leverage superior voice phishing (aka vishing) and bogus credential harvesting websites mimicking focused corporations to achieve unauthorized entry to sufferer environments by amassing sign-on (SSO) credentials and multi-factor authentication (MFA) codes.
The top objective of the assaults is to focus on cloud-based software-as-a-service (SaaS) purposes to siphon delicate knowledge and inner communications and extort victims.
The tech large’s risk intelligence crew stated it is monitoring the exercise underneath a number of clusters, together with UNC6661, UNC6671, and UNC6240 (aka ShinyHunters), in order to account for the chance that these teams may very well be evolving their modus operandi or mimicking beforehand noticed ways.
“Whereas this technique of focusing on id suppliers and SaaS platforms is in line with our prior observations of risk exercise previous ShinyHunters-branded extortion, the breadth of focused cloud platforms continues to broaden as these risk actors search extra delicate knowledge for extortion,” Mandiant famous.
“Additional, they look like escalating their extortion ways with latest incidents, together with harassment of sufferer personnel, amongst different ways.”
Particulars of the vishing and credential theft exercise are as follows –
UNC6661 has been noticed pretending to be IT workers in calls to workers at focused sufferer organizations, directing them to credential harvesting hyperlinks underneath the guise of instructing them to replace their multi-factor authentication (MFA) settings. The exercise was recorded between early and mid-January 2026.
The stolen credentials are then used to register their very own system for MFA after which transfer laterally throughout the community to exfiltrate knowledge from SaaS platforms. In not less than one case, the risk actor weaponized their entry to compromised e-mail accounts to ship extra phishing emails to contacts at cryptocurrency-focused corporations. The emails had been subsequently deleted to cowl up the tracks. That is adopted by extortion exercise performed by UNC6240.
UNC6671 has additionally been recognized as impersonating IT workers to deceive victims as a part of efforts to acquire their credentials and MFA authentication codes on victim-branded credential harvesting websites since early January 2026. In not less than some cases, the risk actors gained entry to Okta buyer accounts. UNC6671 has additionally leveraged PowerShell to obtain delicate knowledge from SharePoint and OneDrive.
The variations between UNC6661 and UNC6671 relate to using completely different area registrars for registering the credential harvesting domains (NICENIC for UNC6661 and Tucows for UNC6671), in addition to the truth that an extortion e-mail despatched following UNC6671 exercise didn’t overlap with recognized UNC6240 indicators.
This means that completely different units of individuals could also be concerned, illustrating the amorphous nature of those cybercrime teams. What’s extra, the focusing on of cryptocurrency corporations means that the risk actors may additionally be seeking to discover additional avenues for monetary achieve.
To counter the risk posed to SaaS platforms, Google has outlined a protracted listing of hardening, logging, and detection suggestions –
Enhance assist desk processes, together with requiring personnel to require a dwell video name to confirm their id
Restrict entry to trusted egress factors and bodily places; implement sturdy passwords; and take away SMS, telephone name, and e-mail as authentication strategies
Limit management-plane entry, audit for uncovered secrets and techniques and implement system entry controls
Implement logging to extend visibility into id actions, authorizations, and SaaS export behaviors
Detect MFA system enrollment and MFA life cycle adjustments; search for OAuth/app authorization occasions that counsel mailbox manipulation exercise utilizing utilities like ToogleBox E-mail Recall, or id occasions occurring exterior regular enterprise hours
“This exercise just isn’t the results of a safety vulnerability in distributors’ merchandise or infrastructure,” Google stated. “As a substitute, it continues to focus on the effectiveness of social engineering and underscores the significance of organizations transferring in direction of phishing-resistant MFA the place doable. Strategies resembling FIDO2 safety keys or passkeys are proof against social engineering in ways in which push-based, or SMS authentication will not be.”