Might 28, 2025Ravie LakshmananData Privateness / Vulnerability
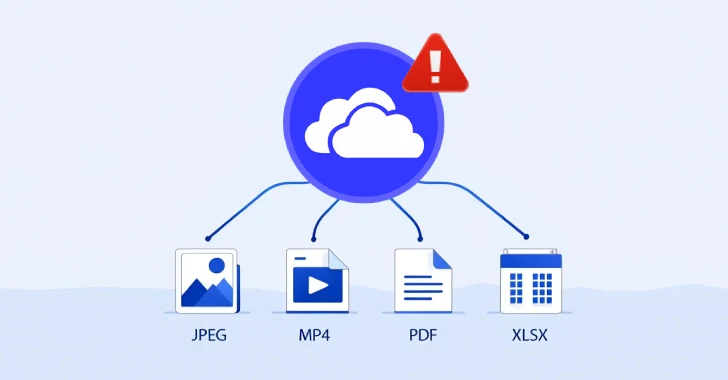
Cybersecurity researchers have found a safety flaw in Microsoft’s OneDrive File Picker that, if efficiently exploited, may enable web sites to entry a person’s total cloud storage content material, versus simply the recordsdata chosen for add by way of the device.
“This stems from overly broad OAuth scopes and deceptive consent screens that fail to obviously clarify the extent of entry being granted,” the Oasis Analysis Group stated in a report shared with The Hacker Information. “This flaw may have extreme penalties, together with buyer information leakage and violation of compliance rules.”
It is assessed that a number of apps are affected, similar to ChatGPT, Slack, Trello, and ClickUp, given their integration with Microsoft’s cloud service.
The issue, Oasis stated, is the results of extreme permissions requested by the OneDrive File Picker, which seeks learn entry to the whole drive, even in circumstances solely a single file is uploaded as a result of absence of fine-grained OAuth scopes for OneDrive.
Compounding issues additional, the consent immediate customers are offered with previous to a file add is imprecise and doesn’t adequately convey the extent of entry being granted, thereby exposing customers to sudden safety dangers.
“The dearth of fine-grained scopes makes it unimaginable for customers to differentiate between malicious apps that focus on all recordsdata and legit apps that ask for extreme permissions just because there isn’t any different safe possibility,” Oasis famous.
The New York-based safety firm additional identified that the OAuth tokens used to authorize entry are sometimes saved insecurely, including they’re saved within the browser’s session storage in plaintext format.
One other potential pitfall is that the authorization workflows may additionally contain issuing a refresh token, granting the appliance ongoing entry to person information by permitting it to get new entry tokens with out having to ask the person to log in once more when the present token expires.
Following accountable disclosure, Microsoft has acknowledged the issue, though there isn’t any repair as but. Within the interim, it is value contemplating quickly eradicating the choice to add recordsdata utilizing OneDrive by means of OAuth till a safe various is in place. Alternately, it is suggested to keep away from utilizing refresh tokens and retailer entry tokens in a safe method and eliminate them when not wanted.
The Hacker Information has reached out to Microsoft for additional remark, and we’ll replace the story if we hear again.
“The dearth of fine-grained OAuth scopes mixed with Microsoft’s imprecise person immediate is a harmful mixture that places each private and enterprise customers in danger,” Oasis stated. “This discovery reinforces the significance of steady vigilance in OAuth scope administration, common safety assessments, and proactive monitoring to guard person information.”
Discovered this text fascinating? Comply with us on Twitter and LinkedIn to learn extra unique content material we publish.