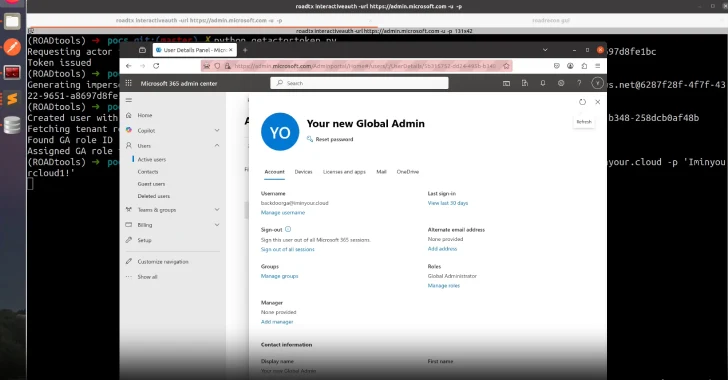
A important token validation failure in Microsoft Entra ID (beforehand Azure Energetic Listing) might have allowed attackers to impersonate any consumer, together with International Directors, throughout any tenant.
The vulnerability, tracked as CVE-2025-55241, has been assigned the utmost CVSS rating of 10.0. It has been described by Microsoft as a privilege escalation flaw in Azure Entra. There isn’t any indication that the problem was exploited within the wild. It has been addressed by the Home windows maker as of July 17, 2025, requiring no buyer motion.
Safety researcher Dirk-jan Mollema, who found and reported the shortcoming on July 14, mentioned the shortcoming made it attainable to compromise each Entra ID tenant on the earth, with the probably exception of nationwide cloud deployments.
The issue stems from a mix of two parts: using service-to-service (S2S) actor tokens issued by the Entry Management Service (ACS) and a deadly flaw within the legacy Azure AD Graph API (graph.home windows.internet) that didn’t adequately validate the originating tenant, which successfully allowed the tokens for use for cross-tenant entry.
What makes this noteworthy is that the tokens are topic to Microsoft’s Conditional Entry insurance policies, enabling a nasty actor with entry to the Graph API to make unauthorized modifications. To make issues worse, the shortage of API degree logging for the Graph API meant that it could possibly be exploited to entry consumer info saved in Entra ID, group and position particulars, tenant settings, software permissions, and machine info and BitLocker keys synced to Entra ID with out leaving any traces.
An impersonation of the International Administrator might enable an attacker to create new accounts, grant themselves extra permissions, or exfiltrate delicate knowledge, leading to a full tenant compromise with entry to any service that makes use of Entra ID for authentication, equivalent to SharePoint On-line and Alternate On-line.
“It could additionally present full entry to any useful resource hosted in Azure, since these sources are managed from the tenant degree and International Admins can grant themselves rights on Azure subscriptions,” Mollema famous.
Microsoft has characterised such cases of cross-tenant entry as a case of “Excessive-privileged entry” (HPA) that “happens when an software or service obtains broad entry to buyer content material, permitting it to impersonate different customers with out offering any proof of consumer context.”
It is price noting that the Azure AD Graph API has been formally deprecated and retired as of August 31, 2025, with the tech big urging customers emigrate their apps to Microsoft Graph. The preliminary announcement of the deprecation was made in 2019.
“Purposes that have been configured for prolonged entry that also rely on Azure AD Graph APIs will be unable to proceed utilizing these APIs beginning in early September 2025,” Microsoft famous again in late June 2025.
Cloud safety firm Mitiga mentioned a profitable exploitation of CVE-2025-55241 can bypass multi-factor authentication (MFA), Conditional Entry, and logging, leaving no path of the incident.
“Attackers might craft these [actor] tokens in ways in which tricked Entra ID into considering they have been anybody, anyplace,” Mitiga’s Roei Sherman mentioned. “The vulnerability arose as a result of the legacy API did not validate the tenant supply of the token.”
“This meant that an attacker might get hold of an Actor token from their very own, non-privileged take a look at setting after which use it to impersonate a International Admin in some other firm’s tenant. The attacker did not want any pre-existing entry to the goal group.”
Beforehand, Mollema additionally detailed a high-severity safety flaw affecting on-premise variations of Alternate Server (CVE-2025-53786, CVSS rating: 8.0) that might enable an attacker to achieve elevated privileges underneath sure circumstances. One other piece of analysis discovered that Intune certificates misconfigurations (equivalent to spoofable identifiers) may be abused by common customers to carry out an ESC1 assault concentrating on Energetic Listing environments.
The event comes weeks after Binary Safety’s Haakon Holm Gulbrandsrud disclosed that the shared API Supervisor (APIM) occasion used to facilitate software-as-a-service (SaaS) connectors may be invoked instantly from the Azure Useful resource Supervisor to attain cross-tenant entry.
“API Connections enable anybody to completely compromise some other connection worldwide, giving full entry to the related backend,” Gulbrandsrud mentioned. “This contains cross-tenant compromise of Key Vaults and Azure SQL databases, in addition to some other externally related service, equivalent to Jira or Salesforce.”
It additionally follows the invention of a number of cloud-related flaws and assault strategies in latest weeks –
An Entra ID OAuth misconfiguration that granted unauthorized entry to Microsoft’s Engineering Hub Rescue even with a private Microsoft account, exposing 22 inside providers and related knowledge.
An assault that exploits Microsoft OneDrive for Enterprise Recognized Folder Transfer (KFM) characteristic, permitting a nasty actor who compromises a Microsoft 365 consumer with OneDrive sync to achieve entry to their apps and recordsdata synced to SharePoint On-line.
The leak of Azure AD software credentials in a publicly accessible Software Settings (appsettings.json) file that might have been exploited to authenticate instantly in opposition to Microsoft’s OAuth 2.0 endpoints, and exfiltrate delicate knowledge, deploy malicious apps, or escalate privileges.
A phishing assault containing a hyperlink to a rogue OAuth software registered in Microsoft Azure that tricked a consumer into granting it permissions to extract Amazon Internet Providers (AWS) entry keys for a sandbox setting throughout the compromised mailbox, permitting unknown actors to enumerate AWS permissions and exploit a belief relationship between the sandbox and manufacturing environments to raise privileges, achieve full management over the group’s AWS infrastructure, and exfiltrate delicate knowledge.
An assault that entails exploiting Server-Aspect Request Forgery (SSRF) vulnerabilities in internet purposes to ship requests to the AWS EC2 metadata service with the objective of accessing the Occasion Metadata Service (IMDS) to compromise cloud sources by retrieving momentary safety credentials assigned to the occasion’s IAM position.
A now-patched situation in AWS’s Trusted Advisor instrument that could possibly be exploited to sidestep S3 Safety Checks by tweaking sure storage bucket insurance policies, inflicting the instrument to incorrectly report publicly-exposed S3 buckets as safe, thereby leaving delicate knowledge uncovered to knowledge exfiltration and knowledge breaches.
A method code AWSDoor that modifies IAM configurations associated to AWS position and belief insurance policies to arrange persistence on AWS environments.
The findings present that even all-too-common misconfigurations in cloud environments can have disastrous penalties for the organizations concerned, resulting in knowledge theft and different follow-on assaults.
“Methods equivalent to AccessKey injection, belief coverage backdooring, and using NotAction insurance policies enable attackers to persist with out deploying malware or triggering alarms,” RiskInsight researchers Yoann Dequeker and Arnaud Petitcol mentioned in a report printed final week.
“Past IAM, attackers can leverage AWS sources themselves – equivalent to Lambda capabilities and EC2 cases – to keep up entry. Disabling CloudTrail, modifying occasion selectors, deploying lifecycle insurance policies for silent S3 deletion, or detaching accounts from AWS Organizations are all strategies that cut back oversight and allow long-term compromise or destruction.”