Could 08, 2025Ravie LakshmananMalware / Cyber Espionage
The nation-state risk actor generally known as MirrorFace has been noticed deploying malware dubbed ROAMINGMOUSE as a part of a cyber espionage marketing campaign directed towards authorities businesses and public establishments in Japan and Taiwan.
The exercise, detected by Development Micro in March 2025, concerned the usage of spear-phishing lures to ship an up to date model of a backdoor known as ANEL.
“The ANEL file from the 2025 marketing campaign mentioned on this weblog carried out a brand new command to help an execution of BOF (Beacon Object File) in reminiscence,” safety researcher Hara Hiroaki stated. “This marketing campaign additionally probably leveraged SharpHide to launch the second stage backdoor NOOPDOOR.”
The China-aligned risk actor, also called Earth Kasha, is assessed to be a sub-cluster inside APT10. In March 2025, ESET make clear a marketing campaign known as Operation AkaiRyū that focused a diplomatic group within the European Union in August 2024 with ANEL (aka UPPERCUT).
The focusing on of assorted Japanese and Taiwanese entities factors to a continued growth of their footprint, because the hacking crew seeks to conduct data theft to advance their strategic goals.
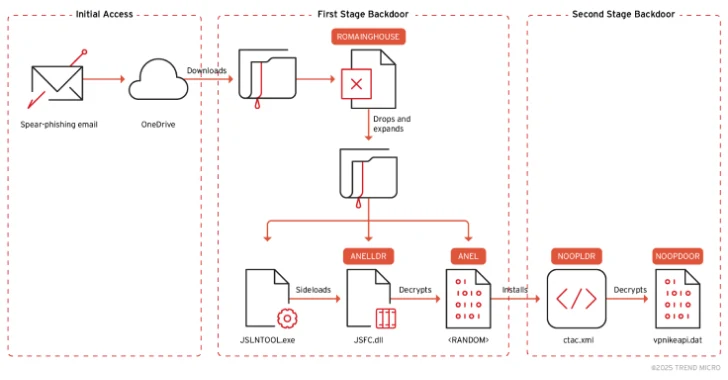
The assault begins with a spear-phishing electronic mail — a few of that are despatched from legitimate-but-compromised accounts — that comprises an embedded Microsoft OneDrive URL, which, in flip, downloads a ZIP file.
The ZIP archive features a malware-laced Excel doc, and a macro-enabled dropper codenamed ROAMINGMOUSE that serves as a conduit to ship elements associated to ANEL. It is price noting that ROAMINGMOUSE has been put to make use of by MirrorFace since final yr.
“ROAMINGMOUSE then decodes the embedded ZIP file by utilizing Base64, drops the ZIP on a disk, and expands its elements,” Hiroaki stated. This contains –
JSLNTOOL.exe, JSTIEE.exe, or JSVWMNG.exe (a reliable binary)
JSFC.dll (ANELLDR)
An encrypted ANEL payload
MSVCR100.dll (a reliable DLL dependency of the executable)
The top purpose of the assault chain is to launch the reliable executable utilizing explorer.exe after which use it to sideload the malicious DLL, on this case, ANELLDR, which is answerable for decrypting and launching the ANEL backdoor.
What’s notable concerning the ANEL artifact used within the 2025 marketing campaign is the addition of a brand new command to help in-memory execution of beacon object information (BOFs), that are compiled C packages designed to increase the Cobalt Strike agent with new post-exploitation options.
“After putting in the ANEL file, actors behind Earth Kasha obtained screenshots utilizing a backdoor command and examined the sufferer’s atmosphere,” Development Micro defined. “The adversary seems to analyze the sufferer by trying by means of screenshots, working course of lists, and area data.”
Choose situations have additionally leveraged an open-source instrument named SharpHide to launch a brand new model of NOOPDOOR (aka HiddenFace), one other backdoor beforehand recognized as utilized by the hacking group. The implant, for its half, helps DNS-over-HTTPS (DoH) to hide its IP tackle lookups throughout command-and-control (C2) operations.
“Earth Kasha continues to be an lively superior persistent risk and is now focusing on authorities businesses and public establishments in Taiwan and Japan in its newest marketing campaign which we detected in March 2025,” Hiroaki stated.
“Enterprises and organizations, particularly these with high-value property like delicate information referring to governance, in addition to mental property, infrastructure information, and entry credentials ought to proceed to be vigilant and implement proactive safety measures to stop falling sufferer to cyber assaults.”
Discovered this text attention-grabbing? Observe us on Twitter and LinkedIn to learn extra unique content material we submit.