Risk actors with ties to China have been noticed utilizing an up to date model of a backdoor known as COOLCLIENT in cyber espionage assaults in 2025 to facilitate complete information theft from contaminated endpoints.
The exercise has been attributed to Mustang Panda (aka Earth Preta, Fireant, HoneyMyte, Polaris, and Twill Storm) with the intrusions primarily directed in opposition to authorities entities situated throughout campaigns throughout Myanmar, Mongolia, Malaysia, and Russia.
Kaspersky, which disclosed particulars of the up to date malware, mentioned it is deployed as a secondary backdoor together with PlugX and LuminousMoth infections.
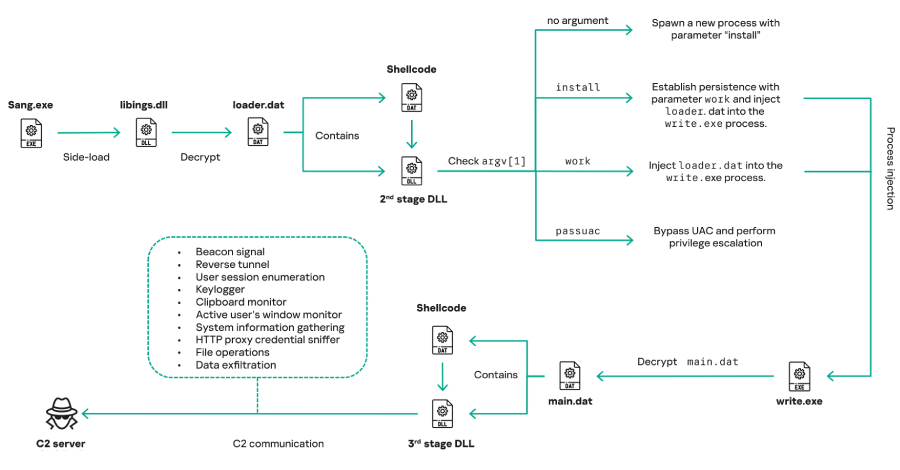
“COOLCLIENT was sometimes delivered alongside encrypted loader recordsdata containing encrypted configuration information, shellcode, and in-memory next-stage DLL modules,” the Russian cybersecurity firm mentioned. “These modules relied on DLL side-loading as their major execution methodology, which required a professional signed executable to load a malicious DLL.”
Between 2021 and 2025, Mustang Panda is claimed to have leveraged signed binaries from numerous software program merchandise, together with Bitdefender (“qutppy.exe”), VLC Media Participant (“vlc.exe” renamed as “googleupdate.exe”), Ulead PhotoImpact (“olreg.exe”), and Sangfor (“sang.exe”) for this goal.
Campaigns noticed in 2024 and 2025 have been discovered to abuse professional software program developed by Sangfor, with one such wave concentrating on Pakistan and Myanmar utilizing it to ship a COOLCLIENT variant that drops and executes a beforehand unseen rootkit.
COOLCLIENT was first documented by Sophos in November 2022 in a report detailing the widespread use of DLL side-loading by China-based APT teams. A subsequent evaluation from Development Micro formally attributed the backdoor to Mustang Panda and highlighted its capability to learn/delete recordsdata, in addition to monitor the clipboard and energetic home windows.
The malware has additionally been put to make use of in assaults concentrating on a number of telecom operators in a single Asian nation in a long-running espionage marketing campaign which will have commenced in 2021, Broadcom’s Symantec and Carbon Black Risk Hunter Crew revealed in June 2024.
COOLCLIENT is designed for accumulating system and consumer info, resembling keystrokes, clipboard contents, recordsdata, and HTTP proxy credentials from the host’s HTTP visitors packets primarily based on directions despatched from a command-and-control (C2) server over TCP. It will possibly additionally arrange a reverse tunnel or proxy, and obtain and execute further plugins in reminiscence.
A number of the supported plugins are listed under –
ServiceMgrS.dll, a service administration plugin to supervise all providers on the sufferer host
FileMgrS.dll, a file administration plugin to enumerate, create, transfer, learn, compress, search, or delete recordsdata and folders
RemoteShellS.dll, a distant shell plugin that spawns a “cmd.exe” course of to permit the operator to concern instructions and seize the ensuing output
Mustang Panda has additionally been noticed deploying three totally different stealer applications as a way to extract saved login credentials from Google Chrome, Microsoft Edge, and different Chromium-based browsers. In not less than one case, the adversary ran a cURL command to exfiltrate the Mozilla Firefox browser cookie file (“cookies.sqlite”) to Google Drive.
These stealers, detected in assaults in opposition to the federal government sector in Myanmar, Malaysia, and Thailand, are suspected for use as a part of broader post-exploitation efforts.
Moreover, the assaults are characterised by way of a identified malware known as TONESHELL (aka TOnePipeShell), which has been employed with various ranges of capabilities to ascertain persistence and drop further payloads like QReverse, a distant entry trojan with distant shell, file administration, screenshot seize, and knowledge gathering options, and a USB worm codenamed TONEDISK.
Kaspersky’s evaluation of the browser credential stealer has additionally uncovered code-level similarities with a cookie stealer utilized by LuminousMoth, suggesting some degree of software sharing between the 2 clusters. On high of that, Mustang Panda has been recognized as utilizing batch and PowerShell scripts to collect system info, conduct doc theft actions, and steal browser login information.
“With capabilities resembling keylogging, clipboard monitoring, proxy credential theft, doc exfiltration, browser credential harvesting, and large-scale file theft, HoneyMyte’s campaigns seem to go far past conventional espionage targets like doc theft and persistence,” the corporate mentioned.
“These instruments point out a shift towards the energetic surveillance of consumer exercise that features capturing keystrokes, accumulating clipboard information, and harvesting proxy credentials.”