Jan 07, 2026Ravie LakshmananVulnerability / Cloud Safety
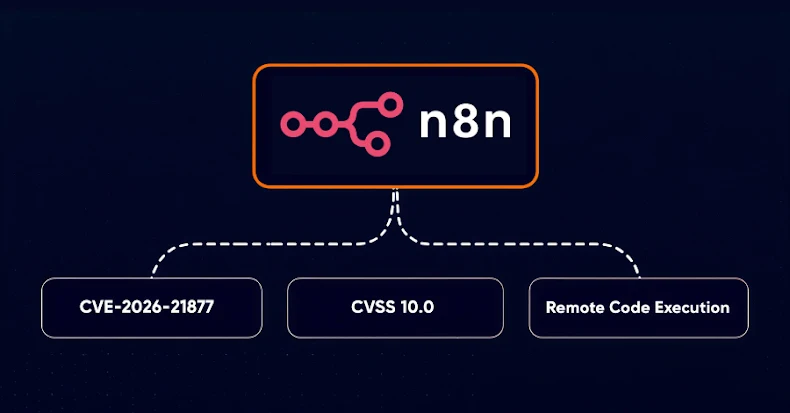
Open-source workflow automation platform n8n has warned of a maximum-severity safety flaw that, if efficiently exploited, might lead to authenticated distant code execution (RCE).
The vulnerability, which has been assigned the CVE identifier CVE-2026-21877, is rated 10.0 on the CVSS scoring system.
“Underneath sure circumstances, an authenticated person might be able to trigger untrusted code to be executed by the n8n service,” n8n stated in an advisory launched Tuesday. “This might lead to full compromise of the affected occasion.”
The maintainers stated each self-hosted deployments and n8n Cloud situations are impacted. The problem impacts the next variations –
It has been addressed in model 1.121.3, which was launched in November 2025. Safety researcher Théo Lelasseux (@theolelasseux) has been credited with discovering and reporting the flaw.
Customers are suggested to improve to this model or later to utterly handle the vulnerability. If quick patching will not be attainable, it is important that directors restrict publicity by disabling the Git node and limiting entry for untrusted customers.
The disclosure comes as n8n has addressed a gradual stream of essential flaws within the platform (CVE-2025-68613 and CVE-2025-68668, CVSS scores: 9.9) that would result in code execution below particular circumstances.