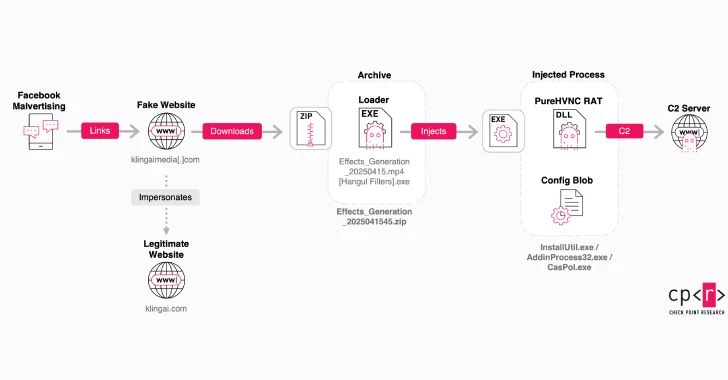
In response to the brand new Browser Safety Report 2025, safety leaders are discovering that the majority id, SaaS, and AI-related dangers converge in a single place, the person’s browser. But conventional controls like DLP, EDR, and SSE nonetheless function one layer too low.
What’s rising is not only a blindspot. It is a parallel risk floor: unmanaged extensions appearing like provide chain implants, GenAI instruments accessed by means of private accounts, delicate information copy/pasted straight into immediate fields, and classes that bypass SSO altogether.
This text unpacks the important thing findings from the report and what they reveal in regards to the shifting locus of management in enterprise safety.
GenAI Is Now the Prime Knowledge Exfiltration Channel
The rise of GenAI in enterprise workflows has created an enormous governance hole. Practically half of workers use GenAI instruments, however most achieve this by means of unmanaged accounts, exterior of IT visibility.
Key stats from the report:
77% of workers paste information into GenAI prompts
82% of these pastes come from private accounts
40% of uploaded information include PII or PCI
GenAI accounts for 32% of all corporate-to-personal information motion
Legacy DLP instruments weren’t designed for this. The browser has change into the dominant channel for copy/paste exfiltration, unmonitored and policy-free.
AI Browsers Are An Rising Menace Floor
One other rising browser-based risk floor is ‘agentic’ AI browsers, which mix the standard safety dangers of browsers with the brand new considerations over AI utilization.
AI browsers like OpenAI’s Atlas, Arc Search, and Perplexity Browser are redefining how customers work together with the online, merging search, chat, and looking right into a single clever expertise. These browsers combine massive language fashions straight into the looking layer, enabling them to learn, summarize, and purpose over any web page or tab in actual time. For customers, this implies seamless productiveness and contextual help. However for enterprises, it represents a brand new and largely unmonitored assault floor: an “always-on co-pilot” that quietly sees and processes every little thing an worker can, with out coverage enforcement or visibility into what’s being shared with the cloud.
The dangers are important and multifaceted: session reminiscence leakage exposes delicate information by means of AI-powered personalization; invisible “auto-prompting” sends web page content material to third-party fashions; and shared cookies blur id boundaries, enabling potential hijacks. With no enterprise-grade guardrails, these AI browsers successfully bypass conventional DLP, SSE, and browser safety instruments, making a file-less, invisible path for information exfiltration. As organizations embrace GenAI and SaaS-driven workflows, understanding and addressing this rising blind spot is crucial to stopping the subsequent era of knowledge leaks and id compromises.
Browser Extensions: The Most Widespread and Least Ruled Provide Chain
99% of enterprise customers have at the least one extension put in. Over half grant excessive or crucial permissions. Many are both sideloaded or revealed by Gmail accounts, with no verification, updates, or accountability.
From the telemetry:
26% of extensions are sideloaded
54% are revealed by Gmail accounts
51% have not been up to date in over a yr
6% of GenAI-related extensions are categorized as malicious
This is not about productiveness anymore, it is an unmanaged software program provide chain embedded in each endpoint.
Id Governance Ends on the IdP. Threat Begins within the Browser.
The report finds that over two-thirds of logins occur exterior of SSO, and practically half use private credentials, making it inconceivable for safety groups to know who’s accessing what, or from the place.
Breakdown:
68% of company logins are accomplished with out SSO
43% of SaaS logins use private accounts
26% of customers reuse passwords throughout a number of accounts
8% of browser extensions entry customers’ identities or cookies
Assaults like Scattered Spider proved this: browser session tokens, not passwords, at the moment are the first goal.
SaaS and Messaging Apps Are Quietly Exfiltrating Delicate Knowledge
Workflows that after relied on file uploads have shifted towards browser-based pasting, AI prompting, and third-party plugins. Most of this exercise now happens within the browser layer, not the app.
Noticed behaviors:
62% of pastes into messaging apps embrace PII/PCI
87% of that occurs through non-corporate accounts
On common, customers paste 4 delicate snippets per day into non-corporate instruments
In incidents just like the Rippling/Deel leak, the breach did not contain malware or phishing, it got here from unmonitored chat apps contained in the browser.
Conventional Instruments Weren’t Constructed for This Layer
EDR sees processes. SSE sees community site visitors. DLP scans information. None of them examine what’s taking place contained in the session, like which SaaS tab is open, what information is being pasted, or which extension is injecting scripts.
Safety groups are blind to:
Shadow AI utilization and immediate inputs
Extension exercise and code modifications
Private vs. company account crossovers
Session hijacking and cookie theft
That is why securing the browser requires a brand new method.
Session-Native Controls Are the Subsequent Frontier
To regain management, safety groups want browser-native visibility, capabilities that function on the session stage with out disrupting person expertise.
What this contains:
Monitoring copy/paste and uploads throughout apps
Detecting unmanaged GenAI instruments and extensions
Implementing session isolation and SSO in all places
Making use of DLP to non-file-based interactions
A contemporary browser safety platform, just like the one outlined within the full report, can present these controls with out forcing customers onto a brand new browser.
Learn the Full Report back to See the Blindspots You are Lacking
The Browser Safety Report 2025 provides a data-rich view into how the browser has quietly change into probably the most crucial and weak endpoint within the enterprise. With insights from thousands and thousands of actual browser classes, it maps the place immediately’s controls fail and the place trendy breaches start.
Obtain the total report back to see what conventional controls are lacking, and what prime CISOs are doing subsequent.
Discovered this text attention-grabbing? This text is a contributed piece from considered one of our valued companions. Observe us on Google Information, Twitter and LinkedIn to learn extra unique content material we publish.