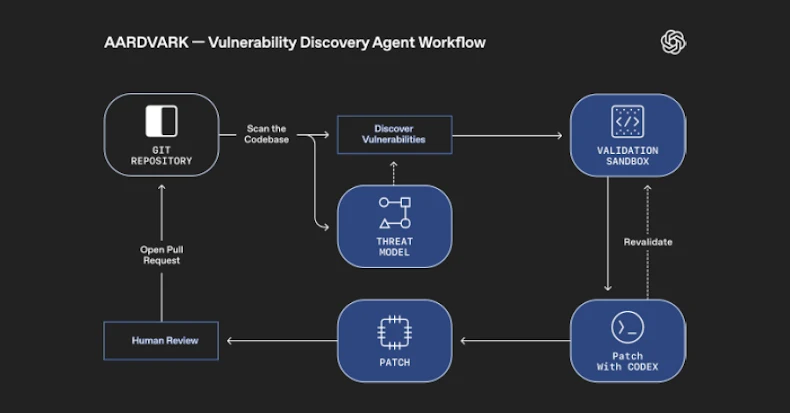
Jul 10, 2025Ravie LakshmananEndpoint Safety / Vulnerability
Cybersecurity researchers have found new artifacts related to an Apple macOS malware known as ZuRu, which is thought to propagate by way of trojanized variations of legit software program.
SentinelOne, in a brand new report shared with The Hacker Information, mentioned the malware has been noticed masquerading because the cross‑platform SSH shopper and server‑administration software Termius in late Might 2025.
“ZuRu malware continues to prey on macOS customers searching for legit enterprise instruments, adapting its loader and C2 strategies to backdoor its targets,” researchers Phil Stokes and Dinesh Devadoss mentioned.
ZuRu was first documented in September 2021 by a person on Chinese language question-and-answer web site Zhihu as a part of a malicious marketing campaign that hijacked searches for iTerm2, a legit macOS Terminal app, to direct customers to pretend websites that tricked unsuspecting customers into downloading the malware.
Then in January 2024, Jamf Menace Labs mentioned it found a chunk of malware distributed by way of pirated macOS apps that shared similarities with ZuRu. Among the different in style software program that has been trojanized to ship the malware embrace Microsoft’s Distant Desktop for Mac, together with SecureCRT and Navicat.
The truth that ZuRu primarily depends on sponsored net searches for distribution signifies the risk actors behind the malware are extra opportunistic than focused of their assaults, whereas additionally making certain that solely these on the lookout for distant connections and database administration are compromised.
Just like the samples detailed by Jamf, the newly found ZuRu artifacts make use of a modified model of the open-source post-exploitation toolkit referred to as Khepri to allow attackers to achieve distant management of contaminated hosts.
“The malware is delivered by way of a .dmg disk picture and accommodates a hacked model of the real Termius.app,” the researchers mentioned. “Because the utility bundle contained in the disk picture has been modified, the attackers have changed the developer’s code signature with their very own advert hoc signature with the intention to cross macOS code signing guidelines.”
The altered app packs in two further executables inside Termius Helper.app, a loader named “.localized” that is designed to obtain and launch a Khepri command-and-control (C2) beacon from an exterior server (“obtain.termius[.]information”) and “.Termius Helper1,” which is a renamed model of the particular Termius Helper app.
“Whereas the usage of Khepri was seen in earlier variations of ZuRu, this implies of trojanizing a legit utility varies from the risk actor’s earlier method,” the researchers defined.
“In older variations of ZuRu, the malware authors modified the primary bundle’s executable by including an extra load command referencing an exterior .dylib, with the dynamic library functioning because the loader for the Khepri backdoor and persistence modules.”
In addition to downloading the Khepri beacon, the loader is designed to arrange persistence on the host and checks if the malware is already current at a pre-defined path within the system and employs(“/tmp/.fseventsd”) and in that case, compares the MD5 hash worth of the payload in opposition to the one which’s hosted on the server.
A brand new model is subsequently downloaded if the hash values do not match. It is believed that the function probably serves as an replace mechanism to fetch new variations of the malware as they grow to be out there. However SentinelOne additionally theorized it may very well be a approach to make sure that the payload has not been corrupted or modified after it was dropped.
The modified Khepri software is a feature-packed C2 implant that enables file switch, system reconnaissance, course of execution and management, and command execution with output seize. The C2 server used to speak with the beacon is “ctl01.termius[.]enjoyable.”
“The most recent variant of macOS.ZuRu continues the risk actor’s sample of trojanizing legit macOS functions utilized by builders and IT professionals,” the researchers mentioned.
“The shift in method from Dylib injection to trojanizing an embedded helper utility is probably going an try to avoid sure sorts of detection logic. Even so, the actor’s continued use of sure TTPs – from selection of goal functions and area title patterns to the reuse of file names, persistence and beaconing strategies – counsel these are providing continued success in environments missing enough endpoint safety.”
Discovered this text attention-grabbing? Comply with us on Twitter and LinkedIn to learn extra unique content material we publish.