Risk actors with ties to North Korea have been noticed focusing on Web3 and cryptocurrency-related companies with malware written within the Nim programming language, underscoring a continuing evolution of their ways.
“Unusually for macOS malware, the menace actors make use of a course of injection method and distant communications by way of wss, the TLS-encrypted model of the WebSocket protocol,” SentinelOne researchers Phil Stokes and Raffaele Sabato mentioned in a report shared with The Hacker Information.
“A novel persistence mechanism takes benefit of SIGINT/SIGTERM sign handlers to put in persistence when the malware is terminated or the system rebooted.”
The cybersecurity firm is monitoring the malware elements collectively beneath the title NimDoor. It is price noting that some points of the marketing campaign had been beforehand documented by Huntabil.IT and later by Huntress and Validin, however with variations within the payloads deployed.
The assault chains contain social engineering ways, approaching targets on messaging platforms like Telegram to schedule a Zoom assembly by way of Calendly, an appointment scheduling software program. The goal is then despatched an e-mail containing a supposed Zoom assembly hyperlink together with directions to run a Zoom SDK replace script to make sure that they’re operating the newest model of the videoconferencing software program.
This step leads to the execution of an AppleScript that acts as a supply automobile for a second-stage script from a distant server, whereas ostensibly redirecting the person to a respectable Zoom redirect hyperlink. The newly downloaded script subsequently unpacks ZIP archives containing binaries which are accountable for organising persistence and launching data stealing bash scripts.
On the coronary heart of the an infection sequence is a C++ loader referred to as InjectWithDyldArm64 (aka InjectWithDyld), which decrypts two embedded binaries named Goal and trojan1_arm64. InjectWithDyldArm64 launches Goal in a suspended state and injects into it the trojan1_arm64’s binary’s code, after which the execution of the suspended course of is resumed.
The malware proceeds to ascertain communication with a distant server and fetch instructions that enable it to collect system data, run arbitrary instructions, and alter or set the present working listing. The outcomes of the execution are despatched again to the server.
Trojan1_arm64, for its half, is able to downloading two extra payloads, which come fitted with capabilities to reap credentials from net browsers like Arc, Courageous, Google Chrome, Microsoft Edge, and Mozilla Firefox, in addition to extract knowledge from the Telegram software.
Additionally dropped as a part of the assaults is a set of Nim-based executable which are used as a launchpad for CoreKitAgent, which displays for person makes an attempt to kill the malware course of and ensures persistence.
“This habits ensures that any user-initiated termination of the malware leads to the deployment of the core elements, making the code resilient to fundamental defensive actions,” the researchers mentioned.
The malware additionally launches an AppleScript that beacons out each 30 seconds to certainly one of two hard-coded command-and-control (C2) servers, whereas additionally exfiltrating a snapshot of the listing of operating processes and executing further scripts despatched by the server.
The findings display how North Korean menace actors are more and more coaching their sights on macOS methods, weaponizing AppleScript to behave as a post-exploitation backdoor to fulfill their knowledge gathering objectives.
“North Korean-aligned menace actors have beforehand experimented with Go and Rust, equally combining scripts and compiled binaries into multi-stage assault chains,” the researchers mentioned.
“Nevertheless, Nim’s fairly distinctive capacity to execute features throughout compile time permits attackers to mix complicated behaviour right into a binary with much less apparent management stream, leading to compiled binaries during which developer code and Nim runtime code are intermingled even on the operate degree.”
Kimsuky’s Use of ClickFix Continues
The disclosure comes as South Korean cybersecurity firm Genians uncovered Kimusky’s continued use of the ClickFix social engineering tactic to ship a wide range of distant entry instruments as a part of a marketing campaign dubbed BabyShark, a identified cluster of exercise attributed to the North Korean hacking group.
The assaults, first noticed in January 2025 and focusing on nationwide safety specialists in South Korea, contain using spear-phishing emails masquerading as interview requests for a respectable German-language enterprise newspaper and trick them into opening a malicious hyperlink containing a bogus RAR archive.
Current inside the archive is a Visible Fundamental Script (VBS) file that is engineered to open a decoy Google Docs file within the person’s net browser, whereas, within the background, malicious code is executed to ascertain persistence on the host by way of scheduled duties and harvest system data.
Subsequent assaults noticed in March 2025 have impersonated a senior U.S. nationwide safety official to deceive targets into opening a PDF attachment that included an inventory of questions associated to a gathering throughout the official’s purported go to to South Korea.
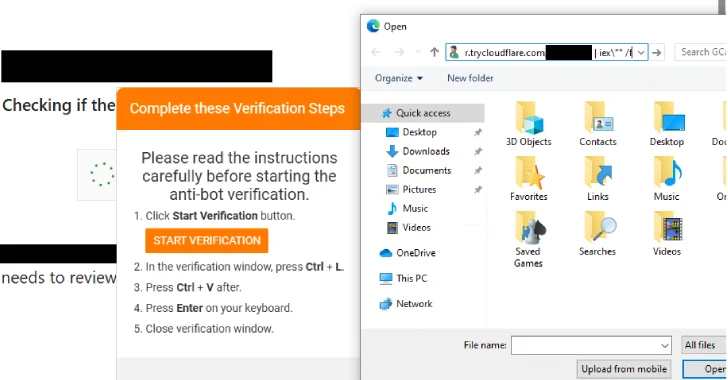
“In addition they tried to trick the goal into opening a guide and getting into an authentication code, supposedly required to entry a safe doc,” Genians mentioned. “Whereas the unique ‘ClickFix’ tactic tricked customers into clicking to repair a particular error, this variant modified the method by prompting customers to repeat and paste an authentication code to entry a safe doc.”
An analogous tactic was documented by Proofpoint in April 2025, the distinction being that the e-mail message claimed to originate from a Japanese diplomat and urged the recipient to arrange a gathering with the Japanese ambassador to america.
As soon as the obfuscated malicious PowerShell command is executed, a decoy Google Docs file is used as a distraction to hide the execution of malicious code that establishes persistent communication with a C2 server to gather knowledge and ship further payloads.
A second variant of the ClickFix technique entails utilizing a pretend web site mimicking a respectable protection analysis job portal and populating it with bogus listings, inflicting website guests who click on on these postings to be served with a ClickFix-style pop-up message to open the Home windows Run dialog and run a PowerShell command.
The command, for its half, guided customers to obtain and set up the Chrome Distant Desktop software program on their methods, enabling distant management over SSH by way of the C2 server “kida.plusdocs.kro[.]kr.” Genians mentioned it found a listing itemizing vulnerability within the C2 server that publicly uncovered knowledge possible collected from victims positioned throughout South Korea.
The C2 server additionally included an IP tackle from China, which has been discovered to comprise a keylogging report for a Proton Drive hyperlink internet hosting a ZIP archive that is used to drop BabyShark malware on the contaminated Home windows host by way of a multi-stage assault chain.
As not too long ago as final month, Kimsuky is believed to have concocted yet one more variant of ClickFix during which the menace actors deploy phony Naver CAPTCHA verification pages to repeat and paste PowerShell instructions into the Home windows Run dialog that launches an AutoIt script to siphon person data.
“The ‘BabyShark’ marketing campaign is thought for its swift adoption of recent assault methods, usually integrating them with script-based mechanisms,” the corporate mentioned. “The ‘ClickFix’ tactic mentioned on this report seems to be one other case of publicly accessible strategies being tailored for malicious use.”
In latest weeks, Kimsuky has additionally been linked to e-mail phishing campaigns that seemingly originate from educational establishments, however distribute malware beneath the pretext of reviewing a analysis paper.
“The e-mail prompted the recipient to open a HWP doc file with a malicious OLE object attachment,” AhnLab mentioned. “The doc was password-protected, and the recipient needed to enter the password offered within the e-mail physique to view the doc.”
Opening the weaponized doc prompts the an infection course of, resulting in the execution of a PowerShell script that performs intensive system reconnaissance and the deployment of the respectable AnyDesk software program for persistent distant entry.
The prolific menace actor that Kimsuky is, the group is in a continuing state of flux concerning its instruments, ways, and methods for malware supply, with a number of the cyber assaults additionally leveraging GitHub as a stager for propagating an open-source trojan referred to as Xeno RAT.
“The malware accesses the attacker’s personal repositories utilizing a hard-coded Github Private Entry Token (PAT),” ENKI WhiteHat mentioned. “This token was used to obtain malware from a personal repository and add data collected from sufferer methods.”
Based on the South Korean cybersecurity vendor, the assaults start with spear-phishing emails with compressed archive attachments containing a Home windows shortcut (LNK) file, which, in flip, is probably going used to drop a PowerShell script that then downloads and launches the decoy doc, in addition to executes Xeno RAT and a PowerShell data stealer.
Different assault sequences have been discovered to make the most of a PowerShell-based downloader that fetches a file with an RTF extension from Dropbox to in the end launch Xeno RAT. The marketing campaign shares infrastructure overlaps with one other set of assaults that delivered a variant of Xeno RAT often known as MoonPeak.
“The attacker managed not solely the malware utilized in assaults but additionally uploaded and maintained contaminated system log recordsdata and exfiltrated data in personal repositories utilizing GitHub Private Entry Tokens (PATs),” ENKI famous. “This ongoing exercise highlights the persistent and evolving nature of Kimsuky’s operations, together with their use of each GitHub and Dropbox as a part of their infrastructure.”
Kimsuky, per knowledge from NSFOCUS, has been one of the lively menace teams from Korea, alongside Konni, accounting for five% of all of the 44 superior persistent menace (APT) actions recorded by the Chinese language cybersecurity firm in Might 2025. Compared, the highest three most lively APT teams in April had been Kimsuky, Sidewinder, and Konni.
Discovered this text fascinating? Observe us on Twitter and LinkedIn to learn extra unique content material we put up.