Oct 01, 2025Ravie LakshmananVulnerability / API Safety
A high-severity safety flaw has been disclosed within the One Identification OneLogin Identification and Entry Administration (IAM) resolution that, if efficiently exploited, may expose delicate OpenID Join (OIDC) utility consumer secrets and techniques below sure circumstances.
The vulnerability, tracked as CVE-2025-59363, has been assigned a CVSS rating of seven.7 out of 10.0. It has been described as a case of incorrect useful resource switch between spheres (CWE-669), which causes a program to cross safety boundaries and acquire unauthorized entry to confidential knowledge or features.
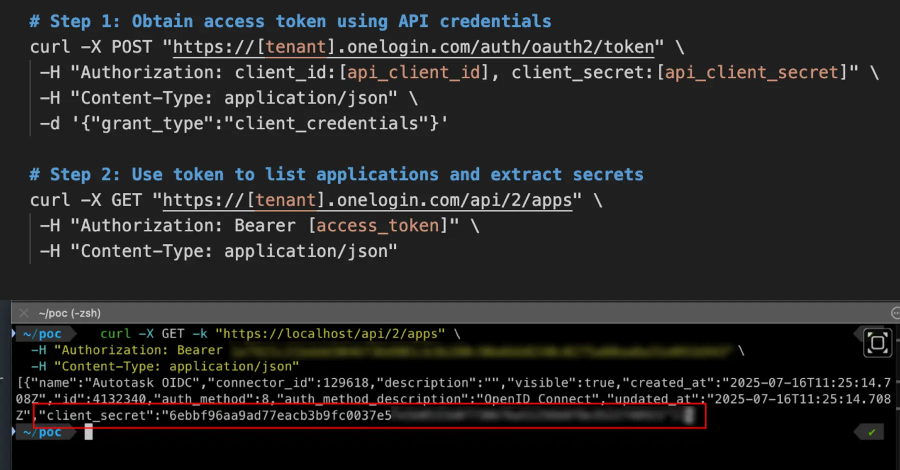
CVE-2025-59363 “allowed attackers with legitimate API credentials to enumerate and retrieve consumer secrets and techniques for all OIDC functions inside a corporation’s OneLogin tenant,” Clutch Safety mentioned in a report shared with The Hacker Information.
The identification safety mentioned the issue stems from the truth that the applying itemizing endpoint – /api/2/apps – was configured to return extra knowledge than anticipated, together with the client_secret values within the API response alongside metadata associated to the apps in a OneLogin account.
The steps to drag off the assault are listed under –
Attacker makes use of legitimate OneLogin API credentials (consumer ID and secret) to authenticate
Request entry token
Name the /api/2/apps endpoint to record all functions
Parse the response to retrieve consumer secrets and techniques for all OIDC functions
Use extracted consumer secrets and techniques to impersonate functions and entry built-in companies
Profitable exploitation of the flaw may permit an attacker with legitimate OneLogin API credentials to retrieve consumer secrets and techniques for all OIDC functions configured inside a OneLogin tenant. Armed with this entry, the menace actor may leverage the uncovered secret to impersonate customers and achieve entry to different functions, providing alternatives for lateral motion.
OneLogin’s role-based entry management (RBAC) grants API keys broad endpoint entry, that means the compromised credentials could possibly be used to entry delicate endpoints throughout your complete platform. Compounding issues additional is the dearth of IP deal with allowlisting, because of which it is potential for attackers to use the flaw from wherever on the planet, Clutch famous.
Following accountable disclosure on July 18, 2025, the vulnerability was addressed in OneLogin 2025.3.0, which was launched final month by making OIDC client_secret values not seen. There isn’t any proof that the problem was ever exploited within the wild.
“Identification suppliers function the spine of enterprise safety structure,” Clutch Safety mentioned. “Vulnerabilities in these methods can have cascading results throughout complete expertise stacks, making rigorous API safety important.”