Oct 06, 2025Ravie LakshmananCybersecurity / Hacking Information
The cyber world by no means hits pause, and staying alert issues greater than ever. Each week brings new tips, smarter assaults, and contemporary classes from the sphere.
This recap cuts via the noise to share what actually issues—key traits, warning indicators, and tales shaping at present’s safety panorama. Whether or not you are defending techniques or simply maintaining, these highlights allow you to spot what’s coming earlier than it lands in your display screen.
⚡ Risk of the Week
Oracle 0-Day Beneath Assault — Risk actors with ties to the Cl0p ransomware group have exploited a zero-day flaw in E-Enterprise Suite to facilitate information theft assaults. The vulnerability, tracked as CVE-2025-61882 (CVSS rating: 9.8), issues an unspecified bug that would permit an unauthenticated attacker with community entry by way of HTTP to compromise and take management of the Oracle Concurrent Processing part. In a publish shared on LinkedIn, Charles Carmakal, CTO of Mandiant at Google Cloud, mentioned “Cl0p exploited a number of vulnerabilities in Oracle EBS which enabled them to steal giant quantities of knowledge from a number of victims in August 2025,” including “a number of vulnerabilities had been exploited together with vulnerabilities that had been patched in Oracle’s July 2025 replace in addition to one which was patched this weekend (CVE-2025-61882).”
🔔 Prime Information
Phantom Taurus Targets Africa, the Center East, and Asia — A beforehand undocumented Chinese language nation-state actor has been focusing on authorities businesses, embassies, army operations, and different entities throughout Africa, the Center East, and Asia in a cyber-espionage operation as refined as it’s stealthy and chronic. What makes the marketing campaign completely different from different China-nexus exercise is the risk actor’s surgical precision, unprecedented persistence, and its use of a extremely refined, custom-built toolkit known as NET-STAR to go after high-value techniques at organizations of curiosity. The risk actor’s operations are supported by different bespoke instruments like TunnelSpecter and SweetSpecter to compromise mail servers and steal information based mostly on key phrase searches.
Detour Canine Makes use of Compromised WordPress Websites to Ship Strela Stealer — A longtime, persistent group of cybercriminals has been silently infecting WordPress web sites all over the world since 2020, utilizing them to redirect unsuspecting website guests to rip-off, and, extra just lately, to malware comparable to Strela Stealer. The risk actor is tracked as Detour Canine. The assault entails utilizing DNS TXT data to ship secret instructions to the contaminated websites to both redirect guests to scams or fetch and run malicious code. In about 90% of the instances, the web site performs as supposed, triggering its malicious conduct solely in choose circumstances. As a result of regular guests solely not often encounter the malicious payloads, infections typically go unnoticed for prolonged intervals of time. Infoblox mentioned Detour Canine possible operates as a distribution-as-a-service (DaaS), utilizing its infrastructure to ship different malware.
Self-Spreading WhatsApp Malware SORVEPOTEL Targets Brazil — Brazilian customers have emerged because the goal of a brand new self-propagating malware that spreads by way of the favored messaging app WhatsApp. The marketing campaign, codenamed SORVEPOTEL by Development Micro, weaponizes the belief with the platform to increase its attain throughout Home windows techniques, including that the assault is “engineered for pace and propagation” fairly than information theft or ransomware. The place to begin of the assault is a phishing message despatched from an already compromised contact on WhatsApp to lend it a veneer of credibility. The message comprises a ZIP attachment that masquerades as a seemingly innocent receipt or well being app-related file. As soon as the attachment is opened, the malware mechanically propagates by way of the desktop net model of WhatsApp, finally inflicting the contaminated accounts to be banned for partaking in extreme spam. There aren’t any indications that the risk actors have leveraged the entry to exfiltrate information or encrypt information.
ProSpy and ToSpy Spy ware Campaigns Goal U.A.E. Android Customers — Two Android adware campaigns dubbed ProSpy and ToSpy have impersonated apps like Sign and ToTok to focus on customers within the United Arab Emirates (U.A.E.). The malicious apps are distributed by way of pretend web sites and social engineering to trick unsuspecting customers into downloading them. As soon as put in, each the adware malware strains set up persistent entry to compromised Android units and exfiltrate information. Neither app containing the adware was accessible in official app shops.
Researchers Exhibit Battering RAM and WireTap — A brand new assault known as Battering RAM can use a $50 interposer to bypass the confidential computing defenses of each Intel and AMD processors utilized in {hardware} powering cloud environments, thus permitting attackers to interrupt encryption designed to guard delicate information. Equally, WireTap undermines the ensures supplied by Intel’s Software program Guard eXtensions (SGX) on DDR4 techniques to passively decrypt delicate information. For the assault to achieve success, nonetheless, it requires that somebody have one-time bodily entry to the {hardware} system. Each Intel and AMD have marked the bodily assault as “out of scope” of their risk fashions. The findings coincide with VMScape, one other assault that breaks present virtualization isolation to leak arbitrary reminiscence and expose cryptographic keys. VMScape has been described as “the primary Spectre-based end-to-end exploit through which a malicious visitor consumer can leak arbitrary, delicate info from the hypervisor within the host area, with out requiring any code modifications and in default configuration.”
️🔥 Trending CVEs
Hackers transfer quick. They typically exploit new vulnerabilities inside hours, turning a single missed patch into a serious breach. One unpatched CVE may be all it takes for a full compromise. Under are this week’s most crucial vulnerabilities gaining consideration throughout the business. Evaluation them, prioritize your fixes, and shut the hole earlier than attackers take benefit.
This week’s checklist contains — CVE-2025-27915 (Zimbra Collaboration), CVE-2025-61882 (Oracle E-Enterprise Suite), CVE-2025-4008 (Smartbedded Meteobridge), CVE-2025-10725 (Pink Hat OpenShift AI), CVE-2025-59934 (Formbricks), CVE-2024-58260 (SUSE Rancher), CVE-2025-43400 (iOS 26.0.1, iPadOS 26.0.1, iOS 18.7.1, iPadOS 18.7.1, macOS Tahoe 26.0.1, macOS Sequoia 15.7.1, macOS Sonoma 14.8.1, and visionOS 26.0.1), CVE-2025-30247 (Western Digital MyCloud), CVE-2025-41250, CVE-2025-41251, CVE-2025-41252 (Broadcom VMware), CVE-2025-9230, CVE-2025-9231, CVE-2025-9232 (OpenSSL), CVE-2025-52906 (TOTOLINK), CVE-2025-59951 (Termix Docker), CVE-2025-10547 (DrayTek), CVE-2025-49844 (Redis), CVE-2025-57714 (QNAP NetBak Replicator), and vulnerabilities in a Russian visitor administration system known as PassOffice.
📰 Across the Cyber World
New iOS Video Injection Device Can Conduct Deepfake Assaults — Cybersecurity researchers have uncovered a extremely specialised software designed to carry out superior video injection assaults, marking a big escalation in digital id fraud. “The software is deployed by way of jailbroken iOS 15 or later units and is engineered to bypass weak biometric verification techniques—and crucially, to use id verification processes that lack biometric safeguards altogether,” iProov mentioned. “This improvement alerts a shift towards extra programmatic and scalable assault strategies.” To carry out the assault, the risk actor makes use of a Distant Presentation Switch Mechanism (RPTM) server to attach their laptop to the compromised iOS machine after which inject refined artificial media.
Qilin Ransomware Claims 104 Assaults in August — The Qilin ransomware operation claimed 104 assaults in August 2025, making it probably the most energetic group, adopted by Akira (56), Sinobi (36), DragonForce (30), and SafePay (29). “The U.S. stays overwhelmingly the most important goal for ransomware teams, whereas Europe and Canada proceed to attract vital curiosity from attackers, with Germany and the UK transferring previous Canada into second and third place, respectively,” Cyble mentioned. Based on information compiled by Halcyon, Manufacturing, Retail, and Hospitals and Physicians Clinics had been the sectors most focused business verticals in August 2025.
New Affect Options Toolkit Emerges — A brand new phishing toolkit named Affect Options has surfaced on cybercrime networks, additional democratizing entry to superior phishing assaults for risk actors with minimal technical abilities. The equipment contains modules to construct Home windows shortcut (LNK) attachments, HTML information for HTML smuggling assaults, HTML templates mimicking login pages and safe bill viewers, SVG information embedded with scripts, and payloads that leverage the Home windows Run dialog for ClickFix assaults. “Promoted as a complete payload supply framework, Affect Options gives attackers with a user-friendly, point-and-click interface to create malicious electronic mail attachments that seem fully legit,” Irregular AI mentioned. “The toolkit focuses on creating persuasive social engineering lures designed to bypass each consumer consciousness and safety filters. These embody weaponized Home windows shortcut information (.LNK), covert HTML pages, and cleverly disguised SVG photographs—all constructed to use human belief fairly than technical vulnerabilities.”
Microsoft Plans to Retire SVG Assist in Outlook — Microsoft mentioned it is retiring help for inline Scalable Vector Graphics (SVG) photographs in Outlook for Internet and the brand new Outlook for Home windows beginning early September 2025. “Outlook for Internet and new Outlook for Home windows will cease displaying inline SVG photographs, displaying clean areas as an alternative,” the corporate mentioned in a Microsoft 365 Message Heart replace. “This impacts beneath 0.1% of photographs, improves safety, and requires no consumer motion. SVG attachments stay supported. Organizations ought to replace documentation and inform customers.” The event comes as risk actors are more and more utilizing SVG information as a strategy to distribute malware in phishing campaigns. Beforehand, Microsoft mentioned the Outlook app for Home windows will begin blocking .library-ms and .search-ms file sorts.
Profile of Keymous+ — A profile of Keymous+ has described it as a risk actor that makes use of publicly accessible DDoS booter companies to launch DDoS assaults. Based on NETSCOUT, the group has been attributed to confirmed 249 DDoS assaults focusing on organizations throughout 15 nations and 21 business sectors. Authorities businesses, hospitality and tourism, transportation and logistics, monetary companies, and telecommunications are a number of the most focused sectors. Morocco, Saudi Arabia, Sudan, India, and France have skilled probably the most frequent assaults. “Though the group’s particular person assaults peaked at 11.8Gbps, collaborative efforts with companions reached 44Gbps, demonstrating considerably enhanced disruptive functionality,” the corporate mentioned.
Lunar Spider Makes use of Pretend CAPTCHA for Malware Supply — The Russian-speaking cybercriminal group often called Lunar Spider (aka Gold Swathmore), which is assessed to be behind IcedID and Latrodectus, has been noticed utilizing ClickFix ways to distribute Latrodectus. “The pretend CAPTCHA framework features a command to run PowerShell that downloads an MSI file and in addition options sufferer click on monitoring, which reviews again to a Telegram channel,” NVISO Labs mentioned. “Throughout the execution chain, the MSI file comprises an Intel EXE file registered in a Run key that subsequently sideloads a malicious DLL, recognized as Latrodectus V2.” In a separate report revealed by The DFIR Report, the risk actor has been attributed to a virtually two-month-long intrusion in Could 2024 that started with a JavaScript file disguised as a tax kind to execute the Brute Ratel framework by way of an MSI installer, together with Latrodectus, Cobalt Strike, and a {custom} .NET backdoor. “Risk actor exercise continued for practically two months with intermittent command and management (C2) connections, discovery, lateral motion, and information exfiltration,” it mentioned. “Twenty days into the intrusion, information was exfiltrated utilizing Rclone and FTP.” Particulars of the exercise had been beforehand shared by EclecticIQ.
Pink Hat Confirms Safety Incident — Pink Hat disclosed that unauthorized risk actors broke into its GitLab occasion used for inner Pink Hat Consulting collaboration in choose engagements and copied some information from it. “The compromised GitLab occasion housed consulting engagement information, which can embody, for instance, Pink Hat’s mission specs, instance code snippets, and inner communications about consulting companies,” the corporate mentioned. “This GitLab occasion usually doesn’t home delicate private information.” It additionally mentioned it is reaching out to impacted clients straight. The acknowledgement got here after an extortion group calling itself the Crimson Collective mentioned it stole practically 570GB of compressed information throughout 28,000 inner improvement repositories.
Google Upgrades CSE in Gmail — Google introduced that Gmail client-side encryption (CSE) customers can ship end-to-end encrypted (E2EE) emails to anybody, even when the recipient makes use of a distinct electronic mail supplier. “Recipients will obtain a notification and might simply entry the encrypted message by way of a visitor account, guaranteeing safe communication with out the trouble of exchanging keys or utilizing {custom} software program,” Google mentioned. The corporate first introduced CSE in Gmail means again in December 2022 and made it typically accessible in March 2023.
FunkSec Returns with FunkLocker — The FunkSec ransomware group has resurfaced with a brand new ransomware pressure known as FunkLocker that displays indicators of being developed by synthetic intelligence. “Some variations are barely purposeful, whereas others combine superior options comparable to anti-VM checks,” ANY.RUN mentioned. “FunkLocker forcefully terminates processes and companies utilizing predefined lists, typically inflicting pointless errors however nonetheless resulting in full system disruption.”
Ransomware Risk Actor Related to Play, RansomHub and DragonForce — A September 2024 intrusion that commenced with the obtain of a malicious file mimicking the EarthTime utility by DeskSoft, led to the deployment of SectopRAT, which then dropped SystemBC and different instruments to conduct reconnaissance. Additionally found within the compromised setting had been Grixba, a reconnaissance utility linked to Play ransomware; Betruger, a backdoor related to RansomHub; and the presence of a earlier NetScan output containing information from an organization reportedly compromised by DragonForce ransomware, indicating that the risk actor was possible an affiliate for a number of ransomware teams, the DFIR Report mentioned. Whereas no file-encrypting malware was executed, the actor managed to laterally transfer throughout the community via RDP connections and exfiltrate information over WinSCP to an FTP server within the type of WinRAR archives.
LinkedIn Sues ProAPIs for Unauthorized Scraping — LinkedIn filed a lawsuit towards an organization known as ProAPIs for allegedly working a community of hundreds of thousands of faux accounts used to scrape information from LinkedIn members earlier than promoting the data to third-parties with out permission. The Microsoft-owned firm mentioned ProAPIs costs clients as much as $15,000 per thirty days for scraped consumer information taken from the social media platform. “Defendants’ industrial-scale pretend account mill scrapes member info that actual folks have posted on LinkedIn, together with information that’s solely accessible behind LinkedIn’s password wall and that Defendants’ clients could not in any other case be allowed to entry, and definitely usually are not allowed to repeat and hold in perpetuity,” in line with the lawsuit.
BBC Journalist Supplied Cash to Hack into Firm’s Community — A BBC journalist was supplied a big amount of cash by cybercriminals who sought to hack into the BBC’s community in hopes of stealing helpful information and leveraging it for a ransom. “In case you are , we are able to give you 15% of any ransom cost for those who give us entry to your PC,” the message obtained by the journalist on the Sign messaging app in July 2025. The person who reached out claimed to be a part of the Medusa ransomware group. Ultimately, out of precaution, their account was disconnected from BBC completely. When the journalist stopped responding, the risk actor ended up deleting their Sign account. The findings present that risk actors are more and more on the lookout for underpaid or disgruntled workers at potential targets to promote their entry so as to breach networks.
Spike in Exploitation Efforts Focusing on Grafana Flaw — GreyNoise warned of a pointy one-day surge of exploitation makes an attempt focusing on CVE-2021-43798 – a Grafana path traversal vulnerability that permits arbitrary file reads – on September 28, 2025. Over the course of the day, 110 distinctive malicious IP addresses tried exploitation, with China-, Germany-, and Bangladesh-based IPs focusing on the U.S., Slovakia, and Taiwan. “The uniform focusing on sample throughout supply nations and tooling signifies widespread tasking or shared exploit use,” it mentioned. “The convergence suggests both one operator leveraging various infrastructure or a number of operators reusing the identical exploit equipment and goal set.”
New Information Leak Web site Launched by LAPSUS$, Scattered Spider, and ShinyHunters — The loose-knit group comprising LAPSUS$, Scattered Spider, and ShinyHunters has revealed a devoted information leak website on the darkish net, known as Scattered LAPSUS$ Hunters, threatening to launch practically a billion data stolen from firms that retailer their clients’ information in cloud databases hosted by Salesforce. “We’re conscious of latest extortion makes an attempt by risk actors, which we’ve got investigated in partnership with exterior consultants and authorities,” Salesforce mentioned in response. “Our findings point out these makes an attempt relate to previous or unsubstantiated incidents, and we stay engaged with affected clients to supply help. Presently, there isn’t a indication that the Salesforce platform has been compromised, neither is this exercise associated to any identified vulnerability in our know-how.” In its Telegram channel named “SLSH 6.0 Half 3,” Scattered Lapsus$ Hunters mentioned it plans to launch a second information leak website after the October 10 deadline that can be dedicated to “our (UNC6395) Salesloft Drift App marketing campaign.” The event got here after the cyber extortion group introduced its farewell final month.
Sign Proclaims Sparse Submit Quantum Ratchet — Sign has launched the Sparse Submit Quantum Ratchet (SPQR), a brand new improve to its encryption protocol that mixes quantum-safe cryptography into its present Double Ratchet. The end result, which Sign calls the Triple Ratchet, makes it rather more difficult for future quantum computer systems to interrupt personal chats. The brand new part ensures ahead secrecy and post-compromise safety, guaranteeing that even within the case of key compromise or theft, future messages exchanged between events can be protected. Sign mentioned the rollout of SPQR on the messaging platform can be gradual, and customers need not take any motion for the improve to use aside from holding their purchasers up to date to the most recent model. In September 2023, the messaging app first added help for quantum resistance by upgrading the Prolonged Triple Diffie-Hellman (X3DH) specification to Submit-Quantum Prolonged Diffie-Hellman (PQXDH).
Giant-Scale Phishing Operations Go Undetected for Years — A “multi-year, industrial-scale phishing and model impersonation scheme” operated undetected for greater than three years on Google Cloud and Cloudflare platforms. The exercise pertains to a large-scale phishing-as-a-service (PhaaS) operation that included 48,000 hosts and greater than 80 clusters abusing “high-trust” expired domains. The marketing campaign subsequently used these domains to impersonate trusted manufacturers to distribute pretend login pages, malware, and playing content material. “Lots of the cloned websites nonetheless load sources from the unique model’s cloud infrastructure – which means the unique model could actively be serving content material to a malicious impersonator,” Deep Specter mentioned.
HeartCrypt Evolves right into a Loader for Stealer and RATs — The packer-as-a-service (PaaS) malware known as HeartCrypt has been distributed by way of phishing emails to finally deploy off-the-shelf stealers and distant entry trojans (RATs), in addition to a lesser-prevalent antivirus termination program often called AVKiller. The exercise used copyright infringement notices to focus on victims in Italy utilizing LNK information that contained a URL to fetch an intermediate PowerShell payload that shows a decoy doc whereas additionally concurrently downloading HeartCrypt from Dropbox. “The HeartCrypt packer takes legit executables and modifies them by injecting malicious code within the .textual content part. It additionally inserts just a few further Moveable Executable (PE) sources,” Sophos mentioned. These sources are disguised as bitmap information and begin with a BMP header, however afterwards the malicious content material follows.”
Software program Provide Chain Assault Exploiting Packaging Order — Researchers from the KTH Royal Institute of Expertise and Universtité de Montréal have detailed a novel assault known as Maven-Hijack that exploits the order through which Maven packages dependencies and the way in which the Java Digital Machine (JVM) resolves courses at runtime. “By injecting a malicious class with the identical absolutely certified identify as a legit one right into a dependency that’s packaged earlier, an attacker can silently override core utility conduct with out modifying the principle codebase or library names,” the researchers mentioned.
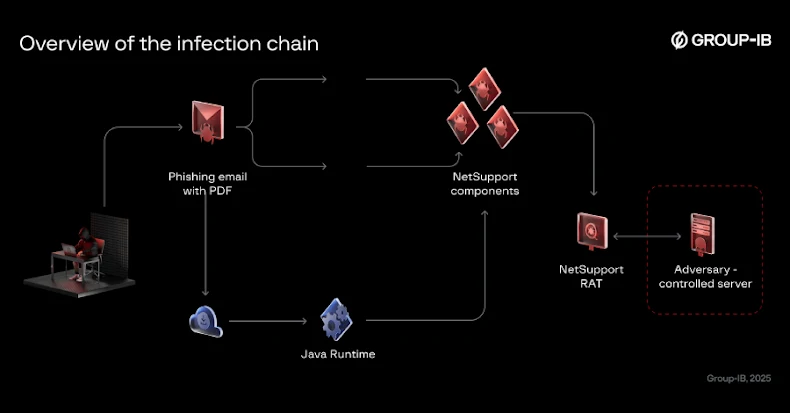
LNK Recordsdata Result in RAT — In a brand new assault chain detailed by K7 Safety Labs, it has been discovered that risk actors are leveraging LNK information distributed by way of Discord to launch a decoy PDF and run PowerShell answerable for dropping a ZIP archive that, in flip, executes a malicious DLL utilizing the Home windows command-line software odbcconf.exe. The DLL is a multi-functional RAT designed to execute instructions from a C2 server and acquire system info from the contaminated host. “It employs a number of strategies, together with accumulating antivirus product info, bypassing Anti-Malware Scan Interface (AMSI), and patching EtwEventWrite to disable Home windows Occasion Tracing (ETW), making it tougher for safety options to detect its malicious actions,” the corporate mentioned.
Unpatched Flaws in Cognex InSight IS2000M-120 Sensible Digicam — As many as 9 safety vulnerabilities have been disclosed in Cognex IS2000M-120, an industrial sensible digicam used for machine imaginative and prescient functions, that permit an attacker to completely compromise the units, undermining their operational integrity and security. No patches are being deliberate for the mannequin, on condition that the corporate is contemplating an end-of-life standing. “First, an unauthenticated attacker on the identical community section because the machine – who’s able to intercepting visitors, for instance by way of a Man-in-the-Center (MitM) assault – can absolutely compromise the machine via a number of assault vectors,” Nozomi Networks mentioned. “This situation presents a vital threat in environments the place community segmentation or encryption will not be enforced.” Moreover, a low-privileged consumer with restricted entry to the digicam can escalate their privileges by creating a brand new administrative account and gaining full management of the machine. Lastly, an attacker with restricted entry to the Home windows workstation the place the Cognex In-Sight Explorer software program is put in can manipulate backup information supposed for the digicam and perform malicious actions.
Hacktivist Group zerodayx1 Launches Ransomware — A professional-Palestinian hacktivist group often called zerodayx1 launched its personal Ransomware-as-a-Service (RaaS) operation known as BQTLock, making it the most recent group to make comparable to pivot. Zerodayx1 is believed to be a Lebanese hacktivist energetic since no less than 2023, positioning themselves as a Muslim and pro-Palestinian risk actor. “Hacktivism is now not confined to ideological messaging,” Outpost24 mentioned. “More and more, teams are integrating financially motivated operations, signaling a shift towards hybrid fashions that mix activism with profit-seeking agendas.”
Cellular Apps Leak Information — New findings from Zimperium have revealed that one in three Android apps and greater than half of iOS apps leak delicate information. Almost half of cellular apps include hard-coded secrets and techniques comparable to API keys. On high of that, an evaluation of 800 free VPN apps for each Android and iOS uncovered that many apps present no actual privateness in any respect, some request extreme permissions far past their objective, others leak private information, and a few depend on outdated, susceptible code. Different dangerous behaviors included lacking privateness vitamin labels for apps and susceptibility to Man-in-the-Center (MitM) assault. “Not all VPN apps may be trusted,’ the corporate mentioned. “Many endure from weak encryption, information leakage, or harmful permission requests—issues which are invisible to most finish customers.” In one other analysis revealed final month, Mike Oude Reimer discovered that misconfigured cellular apps may very well be exploited to realize entry to greater than 150 completely different Firebase companies. This consisted of entry to real-time databases, storage buckets, and secrets and techniques.
Microsoft Shares Insights on XSS Flaws — Based on Microsoft, 15% of all necessary or vital MSRC instances between July 2024 – July 2025 had been cross-site scripting (XSS) flaws. Out of 265 XSS instances, 263 had been rated Vital severity and a couple of had been rated Essential severity. In all, the corporate has mitigated over 970 XSS instances since January 2024 alone as of mid-2025.
Risk Actor Exposes Themselves After Putting in Safety Software program — A risk actor has inadvertently revealed their strategies and day-to-day actions after putting in a trial model of Huntress safety software program on their very own working machine and a premium Malwarebytes browser extension. The actor is alleged to have found Huntress via a Google commercial whereas looking for safety options like Bitdefender. Additional evaluation revealed their makes an attempt to make use of make.com to automate sure workflows, discover working situations of Evilginx, and their curiosity in residential proxy companies like LunaProxy and Nstbrowser. “This incident gave us in-depth details about the day-to-day actions of a risk actor, from the instruments they had been fascinated by to the methods they performed analysis and approached completely different elements of assaults,” Huntress mentioned.
Utilizing bitpixie to Bypass BitLocker — Cybersecurity researchers have discovered that attackers can circumvent BitLocker drive encryption utilizing a Home windows native privilege escalation flaw. “The bitpixie vulnerability in Home windows Boot Supervisor is brought on by a flaw within the PXE tender reboot function, whereby the BitLocker key will not be erased from reminiscence,” SySS mentioned. “To take advantage of this vulnerability on up-to-date techniques, a downgrade assault may be carried out by loading an older, unpatched boot supervisor. This allows attackers to extract the Quantity Grasp Key (VMK) from foremost reminiscence and bypass BitLocker encryption, which may grant them administrative entry.” To counter the risk, it is suggested to make use of a pre-boot PIN or apply a patch that Microsoft launched in 2023 (CVE-2023-21563), which prevents downgrade assaults on the susceptible boot supervisor by changing the previous Microsoft certificates from 2011 with the brand new Home windows UEFI CA 2023 certificates.
How Risk Actors Can Abuse Area Fronting — In area fronting, an attacker may connect with a site that appears outwardly legit by connecting to a site as google.com or meet.google.com, whereas the backend routes quietly diverts the connection to attacker-controlled infrastructure hosted contained in the Google Cloud Platform. By routing C2 visitors via core web infrastructure and domains, it permits malicious visitors to mix in and fly beneath the radar. “You make the SNI [Server Name Indication] appear to be a trusted, high-reputation service (google.com), however the Host header quietly factors visitors to attacker-controlled infrastructure,” Praetorian mentioned. “From the skin, the visitors seems like regular utilization of a serious service. However on the backend, it is routed someplace completely completely different.”
Mis-issued certificates for Cloudflare’s 1.1.1.1 DNS service — Cloudflare revealed that unauthorized certificates had been issued by Fina CA for 1.1.1.1, one of many IP addresses utilized by its public DNS resolver service. “From February 2024 to August 2025, Fina CA issued 12 certificates for 1.1.1.1 with out our permission,” the online infrastructure firm mentioned. “We now have no proof that unhealthy actors took benefit of this error. To impersonate Cloudflare’s public DNS resolver 1.1.1.1, an attacker wouldn’t solely require an unauthorized certificates and its corresponding personal key, however attacked customers would additionally must belief the Fina CA.”
New Assault to Compromise Internet Searching AI Brokers — A novel assault demonstrated by JFrog exhibits that web site cloaking strategies may be weaponized to poison autonomous web-browsing brokers powered by Giant Language Fashions (LLMs). “As these brokers turn out to be extra prevalent, their distinctive and infrequently homogenous digital fingerprints – comprising browser attributes, automation framework signatures, and community traits – create a brand new, distinguishable class of net visitors. The assault exploits this fingerprintability,” safety researcher Shaked Zychlinski mentioned. “A malicious web site can determine an incoming request as originating from an AI agent and dynamically serve a distinct, “cloaked” model of its content material. Whereas human customers see a benign webpage, the agent is introduced with a visually equivalent web page embedded with hidden, malicious directions, comparable to oblique immediate injections. This mechanism permits adversaries to hijack agent conduct, resulting in information exfiltration, malware execution, or misinformation propagation, all whereas remaining fully invisible to human customers and standard safety crawlers.”
Exploit Device Invocation Immediate to Hijack LLM-Based mostly Agentic Techniques — Device Invocation Immediate (TIP) serves as a vital part in LLM techniques, figuring out how LLM-based agentic techniques invoke numerous exterior instruments and interpret suggestions from the execution of those instruments. Nonetheless, new analysis has disclosed that instruments like Cursor and Claude Code are vulnerable to distant code execution or denial-of-service (DoS) by injecting malicious prompts or code into software descriptions. The discovering comes as Forescout famous that LLMs are falling quick in performing vulnerability discovery and exploitation improvement duties.
🎥 Cybersecurity Webinars
Past the Hype: Sensible AI Workflows for Cybersecurity Groups — AI is remodeling cybersecurity workflows, however the very best outcomes come from mixing human oversight with automation. On this webinar, Thomas Kinsella of Tines exhibits how one can pinpoint the place AI actually provides worth, keep away from over-engineering, and construct safe, auditable processes that scale.
Halloween Particular: Actual Breach Tales and the Repair to Finish Password Horrors — Passwords are nonetheless a chief goal for attackers—and a continuing ache for IT groups. Weak or reused credentials, frequent helpdesk resets, and outdated insurance policies expose organizations to pricey breaches and reputational injury. On this Halloween-themed webinar from The Hacker Information and Specops Software program, you will see actual breach tales, uncover why conventional password insurance policies fail, and watch a stay demo on blocking compromised credentials in actual time—so you possibly can finish password nightmares with out including consumer friction.
🔧 Cybersecurity Instruments
Malifiscan – Fashionable software program provide chains depend on public and inner package deal repositories, however malicious uploads more and more slip via trusted channels. Malifiscan helps groups detect and block these threats by cross-referencing exterior vulnerability feeds like OSV towards their very own registries and artifact repositories. It integrates with JFrog Artifactory, helps 10+ ecosystems, and automates exclusion sample creation to forestall compromised dependencies from being downloaded or deployed.
AuditKit – This new software helps groups confirm cloud compliance throughout AWS and Azure with out handbook guesswork. Designed for SOC2, PCI-DSS, and CMMC frameworks, it automates management checks, highlights vital audit gaps, and generates auditor-ready proof guides. Superb for safety and compliance groups making ready for formal assessments, AuditKit bridges the hole between technical scans and the documentation auditors really need.
Disclaimer: These instruments are for academic and analysis use solely. They have not been absolutely security-tested and will pose dangers if used incorrectly. Evaluation the code earlier than attempting them, take a look at solely in protected environments, and observe all moral, authorized, and organizational guidelines.
🔒 Tip of the Week
Fast Home windows Hardening with Open-Supply Instruments — Most Home windows assaults succeed not due to zero-days, however due to weak defaults — open ports, previous protocols, reused admin passwords, or lacking patches. Attackers exploit what’s already there. A couple of small, sensible adjustments can block most threats earlier than they begin.
Harden your Home windows techniques utilizing free, trusted open-source instruments that cowl audit, configuration, and monitoring. You do not want enterprise instruments to lift your protection baseline — just some stable steps.
Fast Actions (Beneath 30 Minutes):
Run Hardentools — disable unsafe defaults immediately.
Use CIS-CAT Lite — determine lacking patches, open RDP, or weak insurance policies.
Verify Native Admins — take away unused accounts, deploy LAPS for password rotation.
Flip On Logging — allow PowerShell, Home windows Defender, and Audit Coverage logs.
Run WinAudit — export a report and evaluate it weekly for unauthorized adjustments.
Scan with Wazuh or OpenVAS — search for outdated software program or uncovered companies.
Key Dangers to Watch:
🔑 Reused or shared admin passwords
🌐 Open RDP/SMB with out firewall or NLA
⚙️ Outdated PowerShell variations with out logging
🧩 Customers working with native admin rights
🪟 Lacking Defender Assault Floor Discount (ASR) guidelines
📦 Unpatched or unsigned software program from third-party repos
These easy, repeatable checks shut 80% of the assault floor exploited in ransomware and credential theft campaigns. They value nothing, take minutes, and construct muscle reminiscence for good cyber hygiene.
Conclusion
Thanks for studying this week’s recap. Continue learning, keep curious, and do not await the subsequent alert to take motion. A couple of sensible strikes at present can prevent lots of cleanup tomorrow.