Key Points
- Information-stealing malware now targets macOS using Python.
- Fake ads and deceptive installers are key distribution methods.
- Social engineering tactics like ClickFix are employed.
Growing Threat to macOS Users
Microsoft has issued a warning about the increasing reach of information-stealing malware targeting macOS systems. These attacks exploit cross-platform programming languages, such as Python, and trusted distribution platforms to expand their impact beyond Windows environments. The warning comes as attackers leverage these sophisticated tools to target Apple’s operating system.
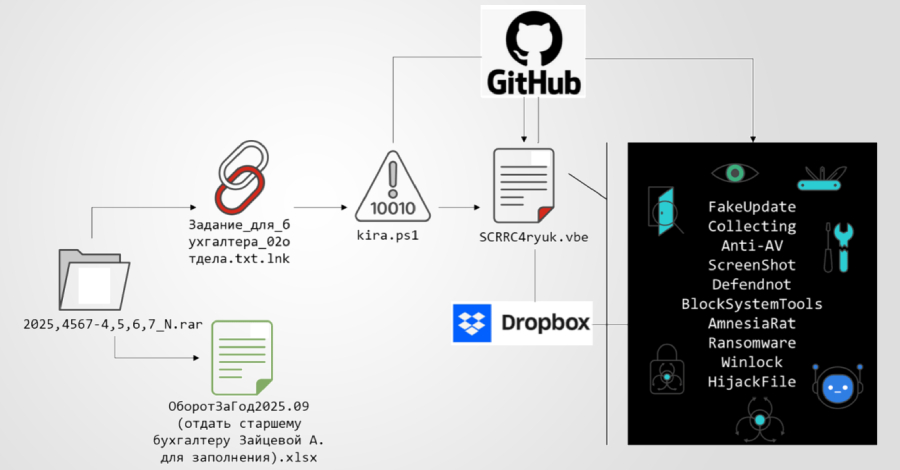
The Defender Security Research Team at Microsoft has noted that since late 2025, there has been a noticeable uptick in infostealer campaigns directed at macOS. These campaigns utilize social engineering ploys like ClickFix to trick users into downloading malicious disk image (DMG) installers. These installers deploy a range of malware, including Atomic macOS Stealer (AMOS), MacSync, and DigitStealer, which are designed to extract sensitive information.
Techniques and Targeted Data
Cybercriminals employ a variety of advanced techniques to execute these attacks, including fileless execution and the use of native macOS utilities and AppleScript automation. The primary aim is to siphon off critical data such as web browser credentials, session data, iCloud Keychain information, and developer secrets. The attacks often originate from deceptive ads, particularly those served through Google Ads, which redirect users looking for specific tools to counterfeit sites.
As Microsoft highlights, Python-based infostealers are favored by attackers due to their adaptability and efficiency in targeting diverse systems with minimal effort. These stealers are commonly distributed through phishing emails, gathering login credentials, session cookies, authentication tokens, credit card information, and cryptocurrency wallet data.
Notable Campaigns and Distribution Methods
Among the identified threats is the PXA Stealer, linked to Vietnamese-speaking threat actors, known for collecting login credentials, financial details, and browser information. Microsoft uncovered two PXA Stealer campaigns in October and December 2025, both initiated via phishing emails. The campaigns employed registry Run keys or scheduled tasks for persistence and used Telegram for command-and-control operations and data exfiltration.
Furthermore, threat actors have been observed utilizing popular messaging apps like WhatsApp to distribute malware such as Eternidade Stealer, which targets financial and cryptocurrency accounts. These campaigns were documented by LevelBlue/Trustwave in November 2025, highlighting the diverse methods attackers use to infiltrate systems.
Defensive Measures for Organizations
To mitigate these threats, organizations are urged to educate employees about social engineering tactics, including malvertising, bogus installers, and ClickFix-style prompts. Monitoring for unusual Terminal activity and scrutinizing network egress for suspicious POST requests to new or dubious domains are also recommended. Vigilance against such infostealers is crucial to prevent data breaches, unauthorized access to internal networks, business email compromises, supply chain attacks, and potential ransomware incidents.
Conclusion
The expansion of Python-based infostealers to macOS underscores the need for robust cybersecurity measures. As attackers refine their strategies, staying informed and implementing proactive defenses are vital to safeguarding sensitive information against these evolving threats.