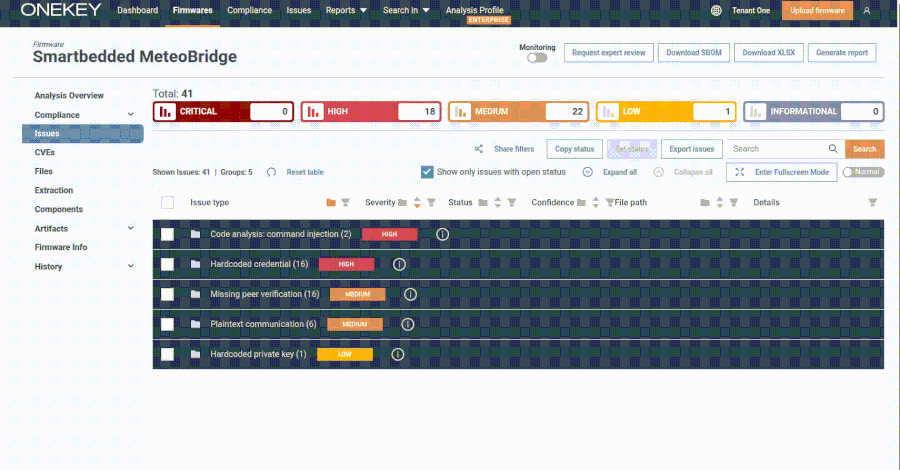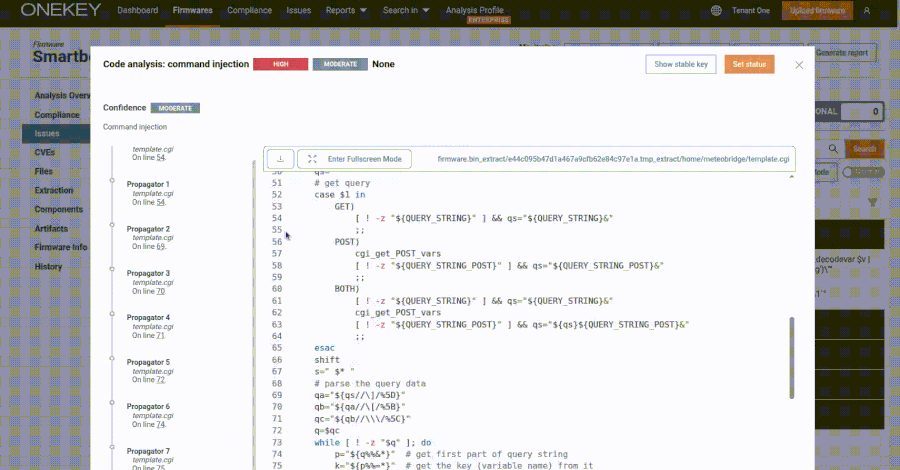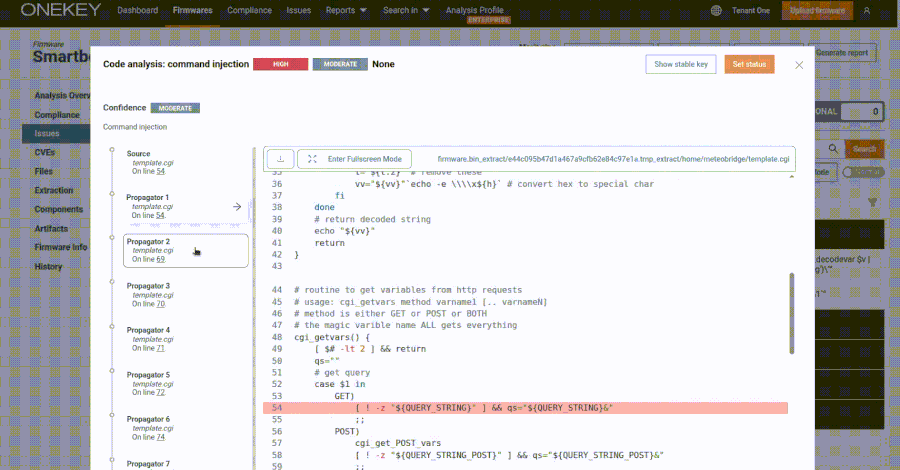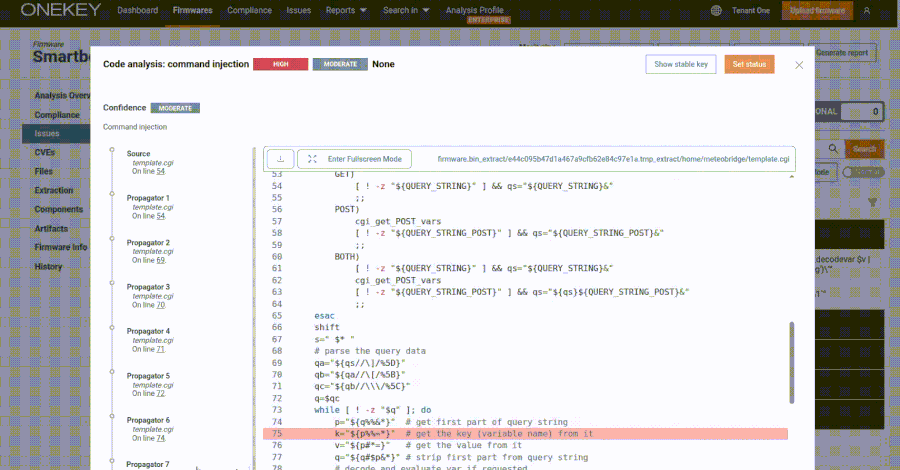
Might 19, 2025Ravie LakshmananRansomware / Malware
A number of ransomware actors are utilizing a malware referred to as Skitnet as a part of their post-exploitation efforts to steal delicate information and set up distant management over compromised hosts.
“Skitnet has been bought on underground boards like RAMP since April 2024,” Swiss cybersecurity firm PRODAFT instructed The Hacker Information. “Nevertheless, since early 2025, we have now noticed a number of ransomware operators utilizing it in real-world assaults.”
“For instance, in April 2025, Black Basta leveraged Skitnet in Groups-themed phishing campaigns focusing on enterprise environments. With its stealth options and versatile structure, Skitnet seems to be gaining traction quickly inside the ransomware ecosystem.”
Skitnet, additionally referred to as Bossnet, is a multi-stage malware developed by a risk actor tracked by the corporate underneath the title LARVA-306. A notable side of the malicious software is that it makes use of programming languages like Rust and Nim to launch a reverse shell over DNS and evade detection.
It additionally incorporates persistence mechanisms, distant entry instruments, instructions for information exfiltration, and even obtain a .NET loader binary that can be utilized to serve further payloads, making it a flexible risk.
First marketed on April 19, 2024, Skitnet is obtainable to potential prospects as a “compact package deal” comprising a server element and malware. The preliminary executable is a Rust binary that decrypts and runs an embedded payload that is compiled in Nim.
“The first operate of this Nim binary is to ascertain a reverse shell reference to the C2 [command-and-control] server through DNS decision,” PRODAFT mentioned. “To evade detection, it employs the GetProcAddress operate to dynamically resolve API operate addresses relatively than utilizing conventional import tables.”
The Nim-based binary additional begins a number of threads to ship DNS requests each 10 seconds, learn DNS responses and extract instructions to be executed on the host, and transmit the outcomes of the execution of the command again to the server. The instructions are issued through a C2 panel that is used to handle the contaminated hosts.
A number of the supported PowerShell instructions are listed beneath –
Startup, which ensures persistence by creating shortcuts within the Startup listing of the sufferer’s machine
Display screen, which captures a screenshot of the sufferer’s desktop
Anydesk/Rutserv, which deploys a respectable distant desktop software program like AnyDesk or Distant Utilities (“rutserv.exe”)
Shell, to run PowerShell scripts hosted on a distant server and ship the outcomes again to the C2 server
AV, which gathers an inventory of put in safety merchandise
“Skitnet is a multi-stage malware that leverages a number of programming languages, and encryption methods,” PRODAFT mentioned. “Through the use of Rust for payload decryption and handbook mapping, adopted by a Nim-based reverse shell speaking over DNS, the malware tries to evade conventional safety measures.”
The disclosure comes as Zscaler ThreatLabz detailed one other malware loader dubbed TransferLoader that is getting used to ship a ransomware pressure referred to as Morpheus focusing on an American legislation agency.
Energetic since at the least February 2025, TransferLoader incorporates three elements, a downloader, a backdoor, and a specialised loader for the backdoor, enabling the risk actors to execute arbitrary instructions on the compromised system.
Whereas the downloader is designed to fetch and execute a payload from a C2 server and concurrently run a PDF decoy file, the backdoor is answerable for working instructions issued by the server, in addition to updating its personal configuration.
“The backdoor makes use of the decentralized InterPlanetary File System (IPFS) peer-to-peer platform as a fallback channel for updating the command-and-control (C2) server,” the cybersecurity firm mentioned. “The builders of TransferLoader use obfuscation strategies to make the reverse engineering course of extra tedious.”
Discovered this text attention-grabbing? Comply with us on Twitter and LinkedIn to learn extra unique content material we put up.