Cybersecurity researchers have make clear two service suppliers that provide on-line felony networks with the mandatory instruments and infrastructure to gasoline the pig butchering-as-a-service (PBaaS) economic system.
No less than since 2016, Chinese language-speaking felony teams have erected industrial-scale rip-off facilities throughout Southeast Asia, creating particular financial zones which can be dedicated to fraudulent funding and impersonation operations.
These compounds are host to 1000’s of people who find themselves lured with the promise of high-paying jobs, solely to have their passports and be pressured to conduct scams beneath the specter of violence. INTERPOL has characterised these networks as human trafficking-fuelled fraud on an industrial scale.
One of many essential drivers of the pig butchering (aka romance baiting) scams is service suppliers who provide the networks with all of the instruments to run and handle social engineering operations, in addition to swiftly launder stolen funds and cryptocurrencies and transfer ill-gotten proceeds to accounts that can not be reached by regulation enforcement.
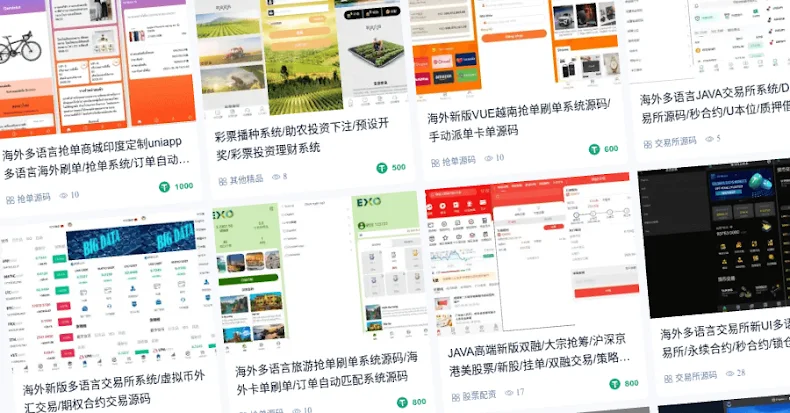
“Massive rip-off compounds such because the Golden Triangle Financial Zone (GTSEZ) are actually utilizing ready-made purposes and templates from PBaaS suppliers,” Infoblox stated in a report revealed final week.
“Compounding the state of affairs additional, what as soon as required technical experience, or an outlay for bodily infrastructure, can now be bought as an off-the-shelf service providing every part from stolen identities and entrance corporations to turnkey rip-off platforms and cell apps, dramatically reducing the barrier to entry.”
These companies have been discovered to supply full packages and fraud kits that set the groundwork for launching scalable on-line rip-off operations with out a lot effort. One such menace actor is Penguin Account Retailer, which additionally goes by the names Heavenly Alliance and Abroad Alliance.
Penguin operates beneath a crimeware-as-a-service (CaaS) mannequin, promoting fraud kits, rip-off templates, and “shè gōng kù” datasets comprising stolen private data belonging to Chinese language residents. The group additionally peddles account knowledge from varied widespread so-called media platforms like Twitter, Tinder, YouTube, Snapchat, Fb, Instagram, Apple Music, OpenAI ChatGPT, Spotify, and Netflix, amongst others.
It is believed that these credentials are probably obtained by means of information-stealing logs bought on the darkish net. But it surely’s presently not recognized in the event that they function the stealers themselves or whether or not they’re merely performing as a dealer of stolen knowledge for different menace actors. Costs for pre-registered social media accounts begin from simply $0.10 and go up in worth relying on the date of registration and authenticity.
Additionally supplied by Penguin are bulk pre-registered SIM playing cards, stolen social media accounts, 4G or 5G routers, IMSI catchers, and packages of stolen photos (aka character units) which can be used to entrap victims. Moreover these, the menace actor has developed a Social Buyer Relationship Administration (SCRM) platform dubbed SCRM AI to permit rip-off operators to facilitate automated sufferer engagement on social media.
“The menace actor additionally advertises BCD Pay, a cost processing platform. BCD Pay, which hyperlinks on to the Bochuang Assure (博创担保自), is an nameless peer-to-peer (P2P) resolution à la HuiOne, with deep roots within the unlawful on-line playing area.”
A second service class that is central to the PBaaS economic system is buyer relationship administration (CRM) platforms, which give centralized management over a number of particular person brokers. UWORK, a vendor of content material and agent administration instruments, gives pre-made templates for creating funding rip-off web sites. Many a rip-off providing additionally claims to have integration with reputable buying and selling platforms like MetaTrader to lend the websites a veneer of belief by displaying real-time monetary data.
These web sites additionally come fitted with a Know Your Buyer (KYC) panel that requires victims to add proof of their id. The web sites’ settings are configured by an administrator by means of a devoted panel, granting them a high-level view of the complete operation, together with the power to create profiles for brokers, who probably interface with the victims.
Panel so as to add a brand new sufferer account and assign them a direct agent
“The admin panel affords every part wanted to run a pig butchering operation. A number of e-mail templates, consumer administration, agent administration, profitability metrics, in addition to chat and e-mail information,” Infoblox stated. “The administration of brokers could be very complicated, and brokers may even be associates of each other.”
PBaaS suppliers have additionally been discovered to supply cell purposes for Android and iOS by distributing them within the type of APK information and enrolling a restricted variety of Apple units right into a testing program with a purpose to bypass app retailer controls.
Some menace actors have taken it a step additional, opting to launch such apps instantly on app marketplaces whereas concealing their performance by masquerading as seemingly innocent information apps. The buying and selling panel is displayed solely when a consumer enters a selected password within the search bar.
Web site templates that embody internet hosting can price as little as $50. An entire pack, together with a web site with admin entry, VPS internet hosting, cell app, entry to a buying and selling platform, entrance firm incorporation in a tax haven to masks their actions, and registration with the related native monetary regulator, can begin at round $2,500.
“Refined Asian crime syndicates have created a world shadow economic system from their protected havens in Southeast Asia,” researchers Maël Le Touz and John Wòjcik stated. “PBaaS gives the mechanisms to scale an operation with comparatively little effort and price.”
Parked Domains as a Conduit for Scams and Malware
The disclosure comes towards the backdrop of a brand new examine from the DNS menace intelligence agency, discovering that the overwhelming majority of parked domains – domains which can be principally expired or dormant, or frequent misspellings of widespread web sites (aka typosquatting) – are getting used to redirect guests to websites that serve scams and malware.
Infoblox revealed that guests to a typosquat of the reputable area belonging to a monetary establishment from a digital non-public community (VPN) are proven a traditional parking web page, however are redirected to rip-off or malware websites if they’re visiting from a residential IP handle. The parked pages, for his or her half, ship guests by means of a redirect chain, whereas concurrently profiling their system utilizing IP geolocation, gadget fingerprinting, and cookies to find out the place to redirect them.
“In massive scale experiments, we discovered that over 90% of the time, guests to a parked area can be directed to unlawful content material, scams, scareware and anti-virus software program subscriptions, or malware, because the ‘click on’ was bought from the parking firm to advertisers, who usually resold that site visitors to one more occasion,” the corporate stated. “None of this displayed content material was associated to the area title we visited.”
Malicious Evilginx AitM Infrastructure Drives Credential Harvesting
In current months, it has additionally emerged that menace actors are leveraging an adversary-in-the-middle (AitM) phishing toolkit named Evilginx in assaults focusing on at the very least 18 universities and academic establishments throughout the U.S. since April 12, 2025, with an purpose to steal login credentials and session cookies. As many as 67 domains have been recognized as linked to the exercise.
“The low detection charges throughout the cybersecurity group spotlight how efficient Evilginx’s evasion strategies have develop into,” Infoblox stated. “Current variations, reminiscent of Evilginx Professional, add options that make detection even tougher.”
“These embody default use of wildcard TLS certificates, bot filtering by means of superior fingerprinting like JA4, decoy net pages, improved integration with DNS suppliers (e.g., Cloudflare, DigitalOcean), multi-domain assist for phishlets, and JavaScript obfuscation. As Evilginx continues to mature, figuring out its phishing URLs will solely develop into more difficult.”
Fraudulent Playing Community Exhibits Indicators of APT Operation
Final month, researchers from safety agency Malanta disclosed particulars of a sprawling infrastructure spanning greater than 328,000 domains and subdomains, together with over 236,000 gambling-related domains, that has been lively since at the very least 2011 and is probably going a twin operation run by a nation-state-sponsored group focusing on victims within the U.S., Europe, and Southeast Asia.
The community, primarily used to focus on Indonesian-speaking guests, is assessed to be half of a bigger operation that features 1000’s of playing domains, malicious Android purposes, hijacking of domains and subdomains hosted on cloud companies, and stealth infrastructure embedded inside enterprise and authorities web sites worldwide, researchers Yinon Azar, Noam Yitzhack, Tzur Leibovitz, and Assaf Morag stated.
“Mixing unlawful playing, search engine marketing manipulation, malware distribution, and extremely persistent takeover strategies, this marketing campaign represents one of many largest and most complicated Indonesian-speaking, well-funded, state-sponsored-level ecosystems noticed up to now,” Malanta stated.
The exercise includes systematic exploitation of WordPress, PHP elements, dangling DNS, and expired cloud belongings to hijack and weaponize trusted domains. The infrastructure has additionally been discovered to energy an enormous Android malware ecosystem hosted on Amazon Net Companies (AWS) S3 buckets to distribute APK droppers with command-and-control (C2) and data-theft capabilities.
The menace actors behind the scheme depend on social media and immediate messaging platforms to promote the playing websites and direct customers to put in the Android apps. As many as 7,700 domains have been flagged containing hyperlinks to at the very least 20 AWS S3 buckets staging the APK information (e.g., “jayaplay168.apk” or “1poker-32bit.apk”).
Some features of the 14-year-old operation have been beforehand highlighted by Imperva and Sucuri, with the latter monitoring it as an internet on line casino spam marketing campaign dubbed Slot Gacor that was discovered hijacking present pages on compromised WordPress web sites by changing them with on line casino spam pages.
The longevity of the infrastructure, mixed with the dimensions and class, has raised the likelihood that it is maintained by an Superior Persistent Risk (APT) that’s deeply embedded within the Indonesian cybercrime ecosystem whereas actively exploiting governmental digital belongings worldwide.