Oct 17, 2025Ravie LakshmananVulnerability / VPN Safety
Cybersecurity researchers have disclosed particulars of a not too long ago patched essential safety flaw in WatchGuard Fireware that might permit unauthenticated attackers to execute arbitrary code.
The vulnerability, tracked as CVE-2025-9242 (CVSS rating: 9.3), is described as an out-of-bounds write vulnerability affecting Fireware OS 11.10.2 as much as and together with 11.12.4_Update1, 12.0 as much as and together with 12.11.3 and 2025.1.
“An out-of-bounds write vulnerability within the WatchGuard Fireware OS iked course of might permit a distant unauthenticated attacker to execute arbitrary code,” WatchGuard mentioned in an advisory launched final month. “This vulnerability impacts each the cell person VPN with IKEv2 and the department workplace VPN utilizing IKEv2 when configured with a dynamic gateway peer.”
It has been addressed within the following variations –
2025.1 – Mounted in 2025.1.1
12.x – Mounted in 12.11.4
12.3.1 (FIPS-certified launch) – Mounted in 12.3.1_Update3 (B722811)
12.5.x (T15 & T35 fashions) – Mounted in 12.5.13)
11.x – Reached end-of-life
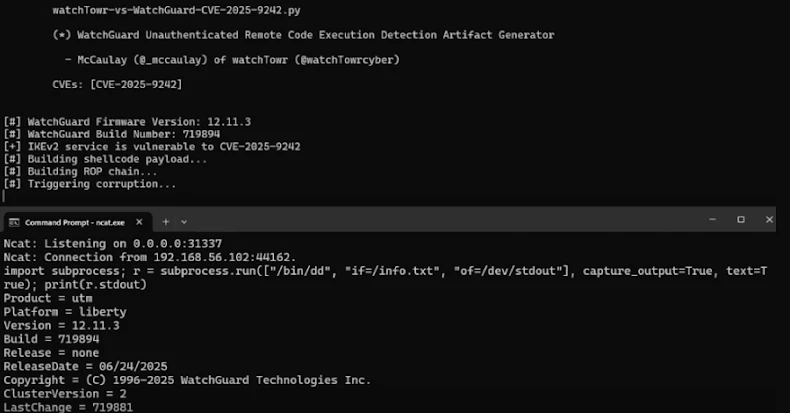
A brand new evaluation from watchTowr Labs has described CVE-2025-9242 as “all of the traits your pleasant neighbourhood ransomware gangs like to see,” together with the truth that it impacts an internet-exposed service, is exploitable sans authentication, and might execute arbitrary code on a fringe equipment.
The vulnerability, per safety researcher McCaulay Hudson, is rooted within the perform “ike2_ProcessPayload_CERT” current within the file “src/ike/iked/v2/ike2_payload_cert.c” that is designed to repeat a consumer “identification” to a neighborhood stack buffer of 520 bytes, after which validate the offered consumer SSL certificates.
The problem arises because of a lacking size test on the identification buffer, thereby permitting an attacker to set off an overflow and obtain distant code execution throughout the IKE_SA_AUTH part of the handshake course of used to determine a digital non-public community (VPN) tunnel between a consumer and WatchGuard’s VPN service through the IKE key administration protocol.
“The server does try certificates validation, however that validation occurs after the weak code runs, permitting our weak code path to be reachable pre-authentication,” Hudson mentioned.
WatchTowr famous that whereas WatchGuard Fireware OS lacks an interactive shell comparable to “/bin/bash,” it is doable to for an attacker to weaponize the flaw and acquire management of the instruction pointer register (aka RIP or program counter) to in the end spawn a Python interactive shell over TCP by leveraging an mprotect() system name, successfully bypassing NX bit (aka no-execute bit) mitigations.
As soon as the distant Python shell, the foothold could be escalated additional via a multi-step course of to acquire a full Linux shell –
Straight executing execve inside Python in an effort to remount the filesystem as learn/write
Downloading a BusyBox busybox binary onto the goal
Symlinking /bin/sh to the BusyBox binary
The event comes as watchTowr demonstrated {that a} now-fixed denial-of-service (DoS) vulnerability impacting Progress Telerik UI for AJAX (CVE-2025-3600, CVSS rating: 7.5) also can allow distant code execution relying on the focused setting. The vulnerability was addressed by Progress Software program on April 30, 2025.
“Relying on the goal codebase – for instance, the presence of explicit no-argument constructors, finalizers, or insecure meeting resolvers – the affect can escalate to distant code execution,” safety researcher Piotr Bazydlo mentioned.
Earlier this month, watchtower’s Sina Kheirkhah additionally make clear a essential pre-authenticated command injection flaw in Dell UnityVSA (CVE-2025-36604, CVSS rating: 9.8/7.3) that might lead to distant command execution. Dell remediated the vulnerability in July 2025 following accountable disclosure on March 28.