Nov 26, 2025Ravie LakshmananMalware / Cyber Espionage
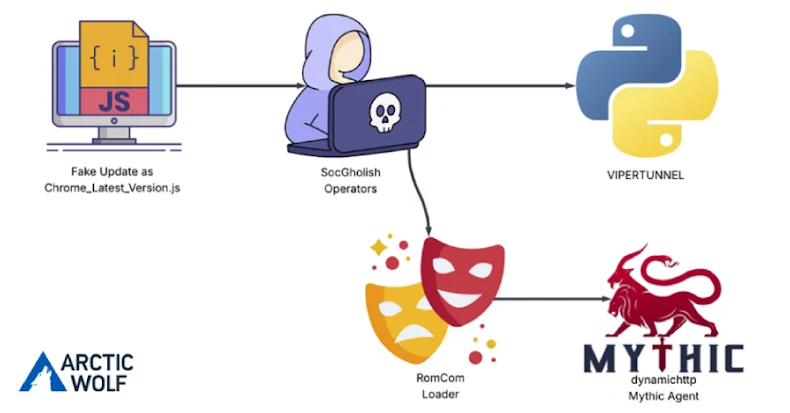
The menace actors behind a malware household often called RomCom focused a U.S.-based civil engineering firm through a JavaScript loader dubbed SocGholish to ship the Mythic Agent.
“That is the primary time {that a} RomCom payload has been noticed being distributed by SocGholish,” Arctic Wolf Labs researcher Jacob Faires stated in a Tuesday report.
The exercise has been attributed with medium-to-high confidence to Unit 29155 of Russia’s Important Directorate of the Common Employees of the Armed Forces of the Russian Federation, also referred to as GRU. In accordance with the cybersecurity firm, the focused entity had labored for a metropolis with shut ties to Ukraine up to now.
SocGholish (aka FakeUpdates), linked to a financially motivated operator tracked as TA569 (aka Gold Prelude, Mustard Tempest, Purple Vallhund, and UNC1543), serves as an preliminary entry dealer, permitting different menace actors to drop a variety of payloads. A few of its identified clients are Evil Corp, LockBit, Dridex, and Raspberry Robin.
The assault chains sometimes contain serving faux browser replace alerts for Google Chrome or Mozilla Firefox on legitimate-but-compromised web sites to trick unsuspecting customers into downloading malicious JavaScript that is accountable for putting in a loader, which then fetches further malware.
For probably the most half, the assaults single out web sites which can be poorly secured, making the most of identified safety vulnerabilities in plugins to inject JavaScript code that is designed to show the pop-up and activate the an infection chain.
RomCom (aka Nebulous Mantis, Storm-0978, Tropical Scorpius, UNC2596, or Void Rabisu), however, is the identify assigned to a Russia-aligned menace actor that is identified to dabble in each cybercrime and espionage operations since a minimum of 2022.
The menace actor leverages a number of strategies, together with spear-phishing and zero-day exploits, to breach goal networks and drop the eponymous distant entry trojan (RAT) on sufferer machines. Assaults mounted by the hacking group have singled out entities in Ukraine, in addition to NATO-related protection organizations.
Within the assault analyzed by Arctic Wolf, the faux replace payload permits the menace actors to run instructions on the compromised machine by way of a reverse shell established to a command-and-control (C2) server. This consists of conducting reconnaissance and dropping a customized Python backdoor codenamed VIPERTUNNEL.
Additionally delivered is a RomCom-linked DLL loader that launches the Mythic Agent, a vital element of the cross-platform, post-exploit, purple teaming framework that communicates with a corresponding server to assist command execution, file operations, and others.
Whereas the assault was finally unsuccessful and was blocked earlier than it might progress any additional, the event exhibits the RomCom menace actor’s continued curiosity in concentrating on Ukraine or entities offering help to the nation, irrespective of how tenuous the connection could also be.
“The timeline from an infection through [the fake update] to the supply of RomCom’s loader was lower than half-hour,” Jacob Faires stated. “Supply isn’t made till the goal’s Lively Listing area has been verified to match a identified worth offered by the menace actor.”
“The widespread nature of SocGholish assaults and the relative pace at which the assault progresses from preliminary entry to an infection makes it a potent menace to organizations worldwide.”