Ravie LakshmananJan 22, 2026Vulnerability / Electronic mail Safety
A brand new safety flaw in SmarterTools SmarterMail e-mail software program has come beneath lively exploitation within the wild, two days after the discharge of a patch.
The vulnerability, which presently doesn’t have a CVE identifier, is tracked by watchTowr Labs as WT-2026-0001. It was patched by SmarterTools on January 15, 2026, with Construct 9511, following accountable disclosure by the publicity administration platform on January 8, 2026.
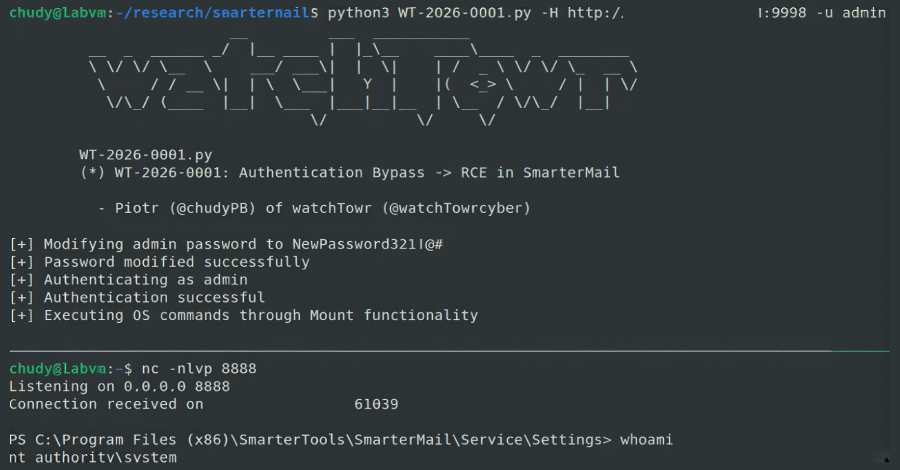
It has been described as an authentication bypass flaw that might permit any consumer to reset the SmarterMail system administrator password by way of a specifically crafted HTTP request to the “/api/v1/auth/force-reset-password” endpoint.
“The kicker after all being that mentioned consumer is ready to use RCE-as-a-feature features to immediately execute OS [operating system] instructions,” watchTowr Labs researchers Piotr Bazydlo and Sina Kheirkhah mentioned.
The issue is rooted within the perform “SmarterMail.Internet.Api.AuthenticationController.ForceResetPassword,” which not solely permits the endpoint to be reached with out authentication, but additionally leverages the truth that the reset request is accompanied by a boolean flag named “IsSysAdmin” to deal with the incoming request relying on whether or not the consumer is a system administrator or not.
In case the flag is ready to “true” (i.e., indicating that the consumer is an administrator), the underlying logic performs the next sequence of actions –
Acquire the configuration akin to the username handed as enter within the HTTP request
Create a brand new system administrator merchandise with the brand new password
Replace the administrator account with the brand new password
In different phrases, the privileged path is configured such that it could trivially replace an administrator consumer’s password by sending an HTTP request with the username of an administrator account and a password of their alternative. This entire lack of safety management could possibly be abused by an attacker to acquire elevated entry, offered they’ve data of an current administrator username.
It does not finish there, for the authentication bypass supplies a direct path to distant code execution via a built-in performance that enables a system administrator to execute working system instructions on the underlying working system and acquire a SYSTEM-level shell.
This may be achieved by navigating to the Settings web page, creating a brand new quantity, and supplying an arbitrary command within the Quantity Mount Command discipline that will get subsequently executed by the host’s working system.
The cybersecurity firm mentioned it selected to make the discovering public following a submit on the SmarterTools Neighborhood Portal, the place a consumer claimed that they misplaced entry to their admin account, with the logs indicating the usage of the identical “force-reset-password” endpoint to alter the password on January 17, 2026, two days after the discharge of the patch.
This possible signifies that the attackers managed to reverse engineer the patches and reconstruct the flaw. To make issues worse, it does not assist that SmarterMail’s launch notes are obscure and don’t explicitly point out what points had been addressed. One merchandise within the bulleted checklist for Construct 9511 merely mentions “IMPORTANT: Important safety fixes.”
In response, SmarterTools CEO Tim Uzzanti hinted that that is achieved so to keep away from giving menace actors extra ammunition, however famous they plan to ship an e-mail each time a brand new CVE is found and once more when a construct has been launched to resolve the difficulty.
“In our 23+ years, now we have had only some CVEs, which had been primarily communicated via launch notes and significant repair references,” Uzzanti mentioned in response to transparency considerations raised by its prospects. “We recognize the suggestions that inspired this variation in coverage transferring ahead.”
It is presently not clear whether or not such an e-mail was despatched to SmarterMail directors this time round. The Hacker Information has reached out to SmarterTools for remark, and we are going to replace the story if we hear again.
The event comes lower than a month after the Cyber Safety Company of Singapore (CSA) disclosed particulars of a maximum-severity safety flaw in SmarterMail (CVE-2025-52691, CVSS rating: 10.0) that could possibly be exploited to attain distant code execution.