The financially motivated risk actor generally known as Storm-0501 has been noticed refining its ways to conduct knowledge exfiltration and extortion assaults focusing on cloud environments.
“Not like conventional on-premises ransomware, the place the risk actor sometimes deploys malware to encrypt crucial information throughout endpoints throughout the compromised community after which negotiates for a decryption key, cloud-based ransomware introduces a basic shift,” the Microsoft Menace Intelligence group mentioned in a report shared with The Hacker Information.
“Leveraging cloud-native capabilities, Storm-0501 quickly exfiltrates giant volumes of information, destroys knowledge and backups throughout the sufferer setting, and calls for ransom — all with out counting on conventional malware deployment.”
Storm-0501 was first documented by Microsoft nearly a 12 months in the past, detailing its hybrid cloud ransomware assaults focusing on authorities, manufacturing, transportation, and legislation enforcement sectors within the U.S., with the risk actors pivoting from on-premises to cloud for subsequent knowledge exfiltration, credential theft, and ransomware deployment.
Assessed to be energetic since 2021, the hacking group has developed right into a ransomware-as-a-service (RaaS) affiliate delivering numerous ransomware payloads over time, resembling Sabbath, Hive, BlackCat (ALPHV), Hunters Worldwide, LockBit, and Embargo.
“Storm-0501 has continued to exhibit proficiency in transferring between on-premises and cloud environments, exemplifying how risk actors adapt as hybrid cloud adoption grows,” the corporate mentioned. “They hunt for unmanaged gadgets and safety gaps in hybrid cloud environments to evade detection and escalate cloud privileges and, in some instances, traverse tenants in multi-tenant setups to realize their targets.”
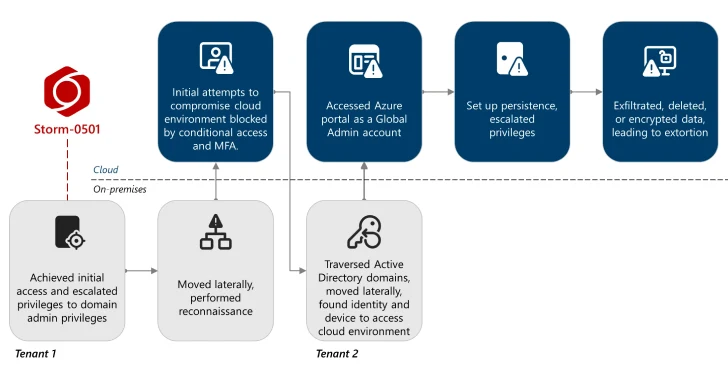
Typical assault chains contain the risk actor abusing their preliminary entry to realize privilege escalation to a site administrator, adopted by on-premises lateral motion and reconnaissance steps that enable the attackers to breach the goal’s cloud setting, thereby initiating a multi-stage sequence involving persistence, privilege escalation, knowledge exfiltration, encryption, and extortion.
Preliminary entry, per Microsoft, is achieved by way of intrusions facilitated by entry brokers like Storm-0249 and Storm-0900, profiting from stolen, compromised credentials to register to the goal system, or exploiting numerous recognized distant code execution vulnerabilities in unpatched public-facing servers.
In a current marketing campaign focusing on an unnamed giant enterprise with a number of subsidiaries, Storm-0501 is claimed to have carried out reconnaissance earlier than laterally transferring throughout the community utilizing Evil-WinRM. The attackers additionally carried out what’s referred to as a DCSync Assault to extract credentials from Lively Listing by simulating the habits of a site controller.
“Leveraging their foothold within the Lively Listing setting, they traversed between Lively Listing domains and finally moved laterally to compromise a second Entra Join server related to a distinct Entra ID tenant and Lively Listing area,” Microsoft mentioned.
“The risk actor extracted the Listing Synchronization Account to repeat the reconnaissance course of, this time focusing on identities and sources within the second tenant.”
These efforts finally enabled Storm-0501 to determine a non-human synced id with a World Admin function in Microsoft Entra ID on that tenant, and missing in multi-factor authentication (MFA) protections. This subsequently opened the door to a situation the place the attackers reset the person’s on-premises password, inflicting it to be synced to the cloud id of that person utilizing the Entra Join Sync service.
Armed with the compromised World Admin account, the digital intruders have been discovered to entry the Azure Portal, registering a risk actor-owned Entra ID tenant as a trusted federated area to create a backdoor, after which elevate their entry to crucial Azure sources, earlier than setting the stage for knowledge exfiltration and extortion.
“After finishing the exfiltration part, Storm-0501 initiated the mass-deletion of the Azure sources containing the sufferer group knowledge, stopping the sufferer from taking remediation and mitigation motion by restoring the info,” Microsoft mentioned.
“After efficiently exfiltrating and destroying the info throughout the Azure setting, the risk actor initiated the extortion part, the place they contacted the victims utilizing Microsoft Groups utilizing one of many beforehand compromised customers, demanding ransom.”
The corporate mentioned it has enacted a change in Microsoft Entra ID that forestalls risk actors from abusing Listing Synchronization Accounts to escalate privileges. It has additionally launched updates to Microsoft Entra Join (model 2.5.3.0) to assist Trendy Authentication to permit clients to configure application-based authentication for enhanced safety.
“It is usually necessary to allow Trusted Platform Module (TPM) on the Entra Join Sync server to securely retailer delicate credentials and cryptographic keys, mitigating Storm-0501’s credential extraction strategies,” the tech big added.