Jul 23, 2025Ravie LakshmananVulnerability / Software program Safety
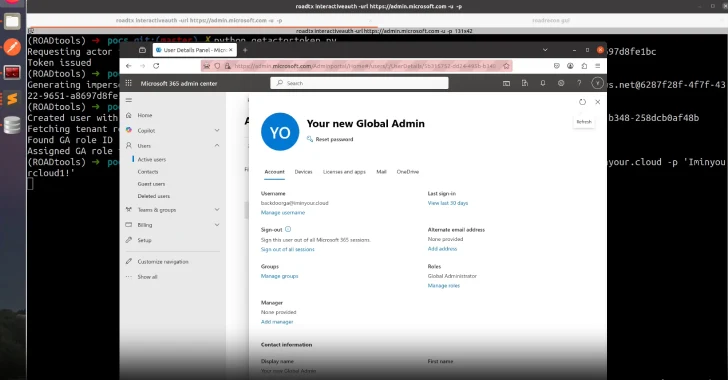
The U.S. Cybersecurity and Infrastructure Safety Company (CISA) added two safety flaws impacting SysAid IT help software program to its Identified Exploited Vulnerabilities (KEV) catalog, based mostly on proof of lively exploitation.
The vulnerabilities in query are listed beneath –
CVE-2025-2775 (CVSS rating: 9.3) – An improper restriction of XML exterior entity (XXE) reference vulnerability within the Checkin processing performance, permitting for administrator account takeover and file learn primitives
CVE-2025-2776 (CVSS rating: 9.3) – An improper restriction of XML exterior entity (XXE) reference vulnerability within the Server URL processing performance, permitting for administrator account takeover and file learn primitives
Each shortcomings had been disclosed by watchTowr Labs researchers Sina Kheirkhah and Jake Knott again in Could, alongside CVE-2025-2777 (CVSS rating: 9.3), a pre-authenticated XXE inside the /lshw endpoint.
The three vulnerabilities had been addressed by SysAid within the on-premise model 24.4.60 construct 16 launched in early March 2025.
The cybersecurity agency famous that the vulnerabilities may permit attackers to inject unsafe XML entities into the online utility, leading to a Server-Aspect Request Forgery (SSRF) assault, and in some circumstances, distant code execution when chained with CVE-2024-36394, a command injection flaw revealed by CyberArk final June.
It is presently not identified how CVE-2025-2775 and CVE-2025-2776 are being exploited in real-world assaults. Neither is any info obtainable concerning the identification of the menace actors, their finish targets, or the dimensions of those efforts.
To safeguard towards the lively menace, Federal Civilian Government Department (FCEB) companies are required to use the required fixes by August 12, 2025.