Oct 22, 2025Ravie LakshmananVulnerability / Knowledge Safety
Cybersecurity researchers have disclosed particulars of a high-severity flaw impacting the favored async-tar Rust library and its forks, together with tokio-tar, that might end in distant code execution beneath sure circumstances.
The vulnerability, tracked as CVE-2025-62518 (CVSS rating: 8.1), has been codenamed TARmageddon by Edera, which found the problem in late August 2025. It impacts a number of widely-used initiatives, reminiscent of testcontainers and wasmCloud.
“Within the worst-case state of affairs, this vulnerability has a severity of 8.1 (Excessive) and may result in Distant Code Execution (RCE) by file overwriting assaults, reminiscent of changing configuration recordsdata or hijacking construct backends,” the Seattle-based safety firm mentioned.
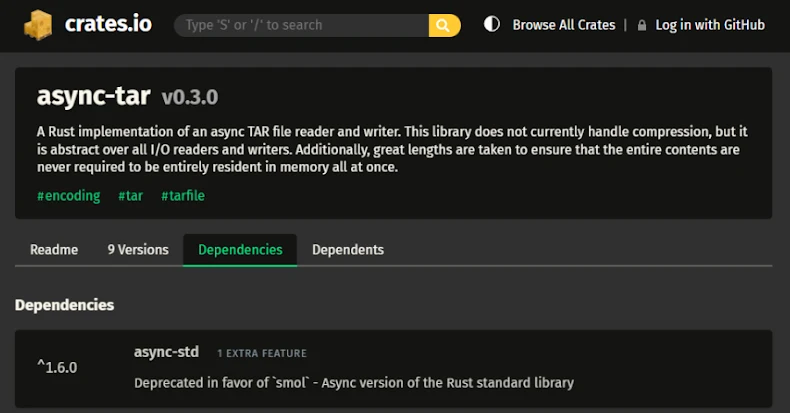
The issue is compounded by the truth that tokio-tar is basically abandonware regardless of attracting 1000’s of downloads by way of crates.io. Tokio-tar is a Rust library for asynchronously studying and writing TAR archives constructed atop the Tokio runtime for the programming language. The Rust crate was final up to date on July 15, 2023.
Within the absence of a patch for tokio-tar, customers counting on the library are suggested emigrate to astral-tokio-tar, which has launched model 0.5.6 to remediate the flaw.
“Variations of astral-tokio-tar previous to 0.5.6 comprise a boundary parsing vulnerability that enables attackers to smuggle further archive entries by exploiting inconsistent PAX/ustar header dealing with,” Astral developer William Woodruff mentioned in an alert.
“When processing archives with PAX-extended headers containing dimension overrides, the parser incorrectly advances stream place based mostly on ustar header dimension (typically zero) as an alternative of the PAX-specified dimension, inflicting it to interpret file content material as official TAR headers.”
The difficulty, in a nutshell, is the results of inconsistent dealing with when dealing with PAX prolonged headers and ustar headers when figuring out file information boundaries. PAX, quick for transportable archive interchange, is an prolonged model of the USTAR format used to retailer properties of member recordsdata in a TAR archive.
The mismatch between a PAX prolonged headers and ustar headers – the place the PAX header accurately specifies the file dimension, whereas the ustar header incorrectly specifies the file dimension as zero (as an alternative of the PAX dimension) – results in a parsing inconsistency, inflicting the library to interpret the inside content material as further outer archive entries.
“By advancing 0 bytes, the parser fails to skip over the precise file information (which is a nested TAR archive) and instantly encounters the subsequent legitimate TAR header positioned initially of the nested archive,” Edera defined. “It then incorrectly interprets the inside archive’s headers as official entries belonging to the outer archive.”
In consequence, an attacker might exploit this habits to “smuggle” additional archives when the library is processing nested TAR recordsdata, thereby making it potential to overwrite recordsdata inside extraction directories, finally paving the best way for arbitrary code execution.
In a hypothetical assault state of affairs, an attacker might add a specially-crafted package deal to PyPI such that the outer TAR incorporates a official pyproject.toml, whereas the hidden inside TAR incorporates a malicious one which hijacks the construct backend and overwrites the precise file throughout set up.
“Whereas Rust’s ensures make it considerably tougher to introduce reminiscence security bugs (like buffer overflows or use-after-free), it doesn’t eradicate logic bugs – and this parsing inconsistency is essentially a logic flaw,” Edera mentioned. “Builders should stay vigilant towards all courses of vulnerabilities, whatever the language used.”