Chainguard, the trusted supply for open supply, has a singular view into how fashionable organizations really eat open supply software program and the place they run into danger and operational burdens. Throughout a rising buyer base and an intensive catalog of over 1800 container picture tasks, 148,000 variations, 290,000 photos, and 100,000 language libraries, and nearly half a billion builds, they’ll see what groups pull, deploy, and preserve day-to-day, together with the vulnerabilities and remediation realities that come hand in hand.
That is why they created The State of Trusted Open Supply, a quarterly pulse on the open supply software program provide chain. As they analyzed anonymized product utilization and CVE information, the Chainguard staff seen frequent themes round what open supply engineering groups are literally constructing with and the dangers related.
Here is what they discovered:
AI is reshaping the baseline stack: Python led the best way as the most well-liked open supply picture amongst Chainguard’s international buyer base, powering the trendy AI stack.
Over half of manufacturing occurs outdoors of the most well-liked tasks: Most groups could standardize on a well-recognized set of photos, however real-world infrastructure is powered by a broad portfolio that extends far past the highest 20 hottest, which they discuss with on this report as longtail photos.
Reputation does not map to danger: 98% of the vulnerabilities discovered and remediated in Chainguard photos occurred outdoors of the highest 20 hottest tasks. Meaning the largest safety burden accumulates within the less-visible a part of the stack, the place patching is hardest to operationalize.
Compliance will be the catalyst for motion: Compliance takes many kinds immediately: from SBOM and vulnerability necessities to business frameworks like PCI DSS, SOC 2, and rules just like the EU’s Cyber Resilience Act. FIPS is only one instance, targeted particularly on U.S. federal encryption requirements. Even so, 44% of Chainguard prospects run a FIPS picture in manufacturing, underscoring how ceaselessly regulatory wants form real-world software program selections.
Belief is constructed on remediation pace: Chainguard eradicated Essential CVEs, on common, in underneath 20 hours.
Earlier than we dive in, a notice on the methodology: This report analyzes 1800+ distinctive container picture tasks, 10,100 whole vulnerability cases, and 154 distinctive CVEs tracked from September 1, 2025, by November 30, 2025. After we use phrases like “high 20 tasks” and “longtail tasks” (as outlined by photos outdoors of the highest 20), we’re referring to actual utilization patterns noticed throughout Chainguard’s buyer portfolio and in manufacturing pulls.
Utilization: What groups really run in manufacturing
Should you zoom out, immediately’s manufacturing container footprint appears precisely such as you’d anticipate: foundational languages, runtimes, and infrastructure elements dominate the most well-liked listing.
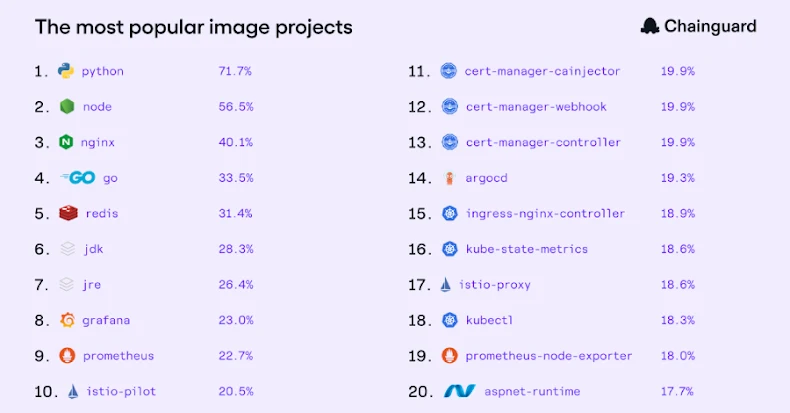
Hottest photos: AI is reshaping the baseline stack
Throughout all areas, the highest photos are acquainted staples: Python (71.7% of consumers), Node (56.5%), nginx (40.1%), go (33.5%), redis (31.4%), adopted by JDK, JRE, and a cluster of core observability and platform tooling like Grafana, Prometheus, Istio, cert-manager, argocd, ingress-nginx, and kube-state-metrics.
This means that prospects function a portfolio of essential constructing blocks – together with languages, gateways, service mesh, monitoring, and controllers – that collectively type the muse of their enterprise.
It is not stunning to see Python main the best way globally, because the default glue language for the trendy AI stack. Groups usually standardize on Python for mannequin improvement, information pipelines, and more and more for manufacturing inference companies as properly.
Hottest by area: Comparable foundations, completely different longtail combine
North America exhibits a broad and constant set of default manufacturing constructing blocks: Python (71.7% of consumers), Node (56.6%), nginx (39.8%), go (31.9%), redis (31.5%), plus sturdy penetration of Kubernetes ecosystem elements (cert-manager, istio, argocd, prometheus, kube-state-metrics, node-exporter, kubectl). Notably, even utility photos like busybox present up meaningfully.
Exterior North America, the identical core stack seems, however the portfolio spreads in another way: Python (72% of consumers), Node (55.8%), Go (44.2%), nginx (41.9%), and a noticeable presence of .NET runtimes (aspnet-runtime, dotnet-runtime, dotnet-sdk) and PostgreSQL.
The longtail of photos is essential to manufacturing, not edge instances
Chainguard’s hottest photos signify just one.37% of all obtainable photos and account for roughly half of all container pulls. The opposite half of manufacturing utilization comes from in every single place else: 1,436 longtail photos that make up 61.42% of the typical buyer’s container portfolio.
In different phrases, half of all manufacturing workloads run on longtail photos. These aren’t edge instances. They’re core to Chainguard’s prospects’ infrastructure. It is comparatively simple to maintain the highest handful of photos polished, however what trusted open supply requires is sustaining that safety and velocity throughout the breadth of what prospects really run.
FIPS utilization: Compliance is a catalyst for motion
FIPS encryption is a necessary expertise within the compliance panorama, targeted on satisfying U.S. federal encryption necessities. And it provides a helpful window into how regulatory strain drives adoption. Within the information, 44% of consumers run no less than one FIPS picture in manufacturing.
The sample is constant: when working inside compliance frameworks like FedRAMP, DoD IL-5, PCI DSS, SOC 2, CRA, Important Eight or HIPAA, groups want hardened, trusted open supply software program that mirrors their business workloads. Essentially the most used FIPS photos align with the broader portfolio, merely with cryptographic modules strengthened for audit and verification.
High FIPS picture tasks embrace Python-fips (62% of consumers with no less than one FIPS picture in manufacturing), Node-fips (50%), nginx-fips (47.2%), go-fips (33.8%), redis-fips (33.1%), plus platform elements like istio-pilot-fips, istio-proxy-fips, and cert-manager variants. Even supporting libraries and crypto foundations present up, corresponding to glibc-openssl-fips.
FIPS will not be the entire story, nevertheless it illustrates a broader reality: compliance is a common driver, emphasizing the necessity for trusted open supply throughout your complete software program stack.
CVEs: Reputation does not map to danger
When trying throughout Chainguard’s catalog of photos, danger is overwhelmingly concentrated outdoors of the most well-liked photos. Of the CVEs Chainguard remediated prior to now three months, 214 occurred within the high 20 photos, accounting for under 2% of the whole CVEs. Transcend these high photos, and you will find the opposite 98% of CVEs Chainguard remediated (10,785 CVE cases). That is 50 occasions the variety of CVEs within the high 20 photos!
The biggest quantity of CVEs are categorized as Medium, however operational urgency usually stems from how rapidly Essential and Excessive CVEs are addressed, and whether or not prospects can depend on that pace throughout their whole portfolio, not simply the most typical photos.
Belief is constructed on remediation pace
For us, belief is measured in time-to-fix, and Chainguard is aware of that is most vital in relation to Essential CVEs. Through the three-month interval analyzed, Chainguard’s staff achieved a lower than 20-hour common remediation time for Essential CVEs, with 63.5% of Essential CVEs being resolved inside 24 hours, 97.6% inside two days, and 100% inside three days.
Along with Essential CVE remediation, the staff addressed Excessive CVEs in 2.05 days, Medium CVEs in 2.5 days, and Low CVEs in 3.05 days, notably quicker than Chainguard’s SLAs (seven days for Essential CVEs and 14 days for prime, medium, and low CVEs).
And this pace is not confined to the most well-liked packages. For each single CVE remediated in a high 20 picture undertaking, they resolved 50 CVEs in less-popular photos.
That longtail is the place most of your actual publicity hides and it may well really feel hopeless attempting to maintain up. Most engineering organizations merely cannot allocate sources to patch vulnerabilities in packages that fall outdoors their core stack, however the information makes it clear that it’s important to safe the “quiet majority” of your software program provide chain with the identical rigor as your most important workloads.
A brand new baseline for trusted open supply
Throughout the info, one takeaway stands out: fashionable software program is powered by a large, shifting portfolio of open supply elements, most of which dwell outdoors the highest 20 hottest photos. That is not the place builders spend their time, nevertheless it’s the place the majority of safety and compliance danger accumulates.
This creates a regarding disconnect: it is rational for engineering groups to give attention to the small set of tasks that matter most to their stack, however the majority of publicity sits within the huge set of dependencies they do not have the time to handle.
That is why breadth issues. Chainguard is constructed to soak up the operational burden of the longtail, offering protection and remediation at a scale that particular person groups cannot justify on their very own. As open supply provide chains develop extra complicated, Chainguard will proceed to trace utilization patterns and shine a light-weight on the place danger actually resides, so you do not have to battle the battle towards the longtail alone.
Able to get began with the trusted supply for open supply? Contact Chainguard to study extra.
Notice: This text was expertly written and contributed by Ed Sawma, VP Product Advertising and marketing, Sasha Itkis, Product Analyst.
Discovered this text attention-grabbing? This text is a contributed piece from one among our valued companions. Observe us on Google Information, Twitter and LinkedIn to learn extra unique content material we submit.